False Positive Mitigation for SQL Injection signatures
The signatures that FortiWeb uses to detect SQL injection attacks are classified into three classes: SQL Injection, SQL Injection (Extended) and SQL Injection (Syntax Based Detection). You can see them being listed in a signature policy. When SQL Injection or SQL Injection (Extended) is enabled, FortiWeb scans the requests and matches them with the signatures based on pattern recognition (multi-pattern keyword and regular expression pattern). However, such detection approach will inevitably cause false positives; one normal request might be mistakenly marked as a SQL injection attack. For example, the following is a SQL Injection that will trigger a signature violation
GET /test.asp?id=1 and 0<>(select count(*) from user_table where user like 'admin') HTTP/1.1
, however, a harmless request will match the signature as well if the request just has the key words select and user in the parameter value like:
GET /test.asp?text= please select a user from the group to test our new product HTTP/1.1
, which is a false positive.
When FortiWeb's False Positive Mitigation is enabled, a signature triggered request is processed further to validate whether it is a true SQL instruction. If it is then we can make the assumption that this is a SQL Injection attempt.
To verify whether the request is a SQL instruction FortiWeb uses lexical analysis which converts the statement characters in the request into a sequence of tokens. It then runs the tokens through different built-in SQL templates and using a SQL parser it validates whether this is a true SQL structure. If it is then this event is not a false positive and FortiWeb triggers the signature violation action

|
The Syntax-Based SQL Injection detection uses a new approach based on lexical and syntax analysis to detect SQL injection attacks without false positives and false negatives. Therefore, it does not require the False Positive Mitigation feature enabled.
|

|
Although Syntax-Based SQL Injection detection is configured under the signature tab, these are not signatures and do not use regex and pattern matching. For convenience reasons it is configured under the signature tab.
|
Enable False Positive Mitigation to the signatures of SQL Injection and SQL Injection (Extended)
When SQL Injection and/or SQL Injection (Extended) are/is enabled in a signature policy, you can enable False Positive Mitigation to the signatures through Web Protection > Known Attacks > Signatures.
1. Select the signature policy to open the edit panel.
2. Click the buttons of SQL Injection and/or SQL Injection (Extended) in the False Positive Mitigation field on the table.
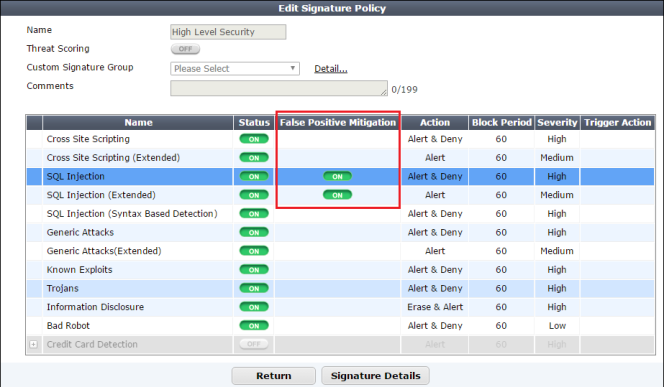
Alternatively, you can apply False Positive Mitigation to SQL Injection and/or SQL Injection (Extended) when editing the signatures (click Edit Signatures or Signature Details).
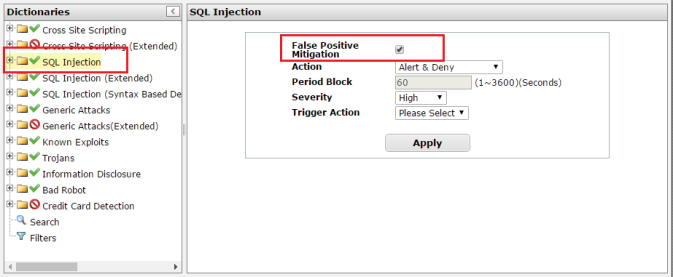
3. Specify the signatures to which you would (or not) like to apply False Positive Mitigation.
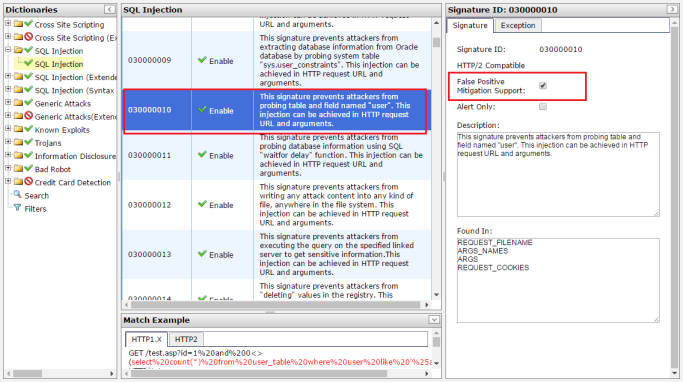
Actually, False Positive Mitigation is not designed for every signature of SQL Injection and SQL Injection (Extended) categories. Particular signatures, such as 030000010, 030000019 and 030000042 in SQL Injection or 040000010, 040000019 and 040000042 in SQL Injection (Extended), support False Positive Mitigation.
When drilling into the categories to check individual signature, you will see a check box named False Positive Mitigation Support in the Signature tab if this signature supports False Positive Mitigation.
By default, all of them are checked. You can uncheck any of them if you would not like to apply False Positive Mitigation to the signature.
Open topic with navigation


