Auto-learning profiles are selected in a server policy in conjunction with an inline or offline protection profile. Auto-learning profiles gather data for the auto-learning report from any attacks and parameters that FortiWeb detects.
You cannot edit or delete Default Auto Learn Profile, the predefined auto-learning profile. If you do not want to configure your own auto-learning profile, or are not sure how to, you can use this profile. Alternatively, use it as a starting point by cloning it and then modifying the clone.
Default Auto Learn Profile assumes that you want to learn about all parameters, and allow web crawlers from the search engines Google, Yahoo!, Baidu, and MSN/Bing.
Default Auto Learn Profile uses a predefined data type group, a predefined suspicious URL pattern, and other settings that populate an auto-learning report with a complete data set. It does not use attack signatures that could cause false positives.
|
|
You can also use an auto-learning report to generate a new auto-learning profile based on existing data. For details, see Generating a profile from auto-learning data. |
1. Before you create an auto-learning profile, configure the following components:
2. Go to Auto Learn > Auto Learn Profile > Auto Learn Profile.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Autolearn Configuration category. For details, see Permissions.
3. Click Create New.
A dialog appears.
4. Configure these settings:
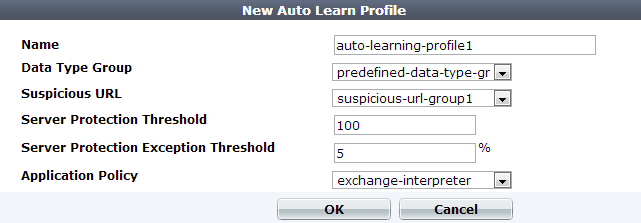
| Setting name | Description |
|---|---|
| Name | Type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters. |
| Data Type Group |
Select the name of a data type group to use, if any. Auto-learning learns about the names, length, and required presence of these types of parameters in HTTP requests. For details, see Grouping predefined data types. |
| Suspicious URL |
Select the name of a suspicious URL pattern to use, if any. Auto-learning considers HTTP requests for these URLs as either malicious vulnerability scanning, data harvesting (a type of web scraping), or administrative login attacks. For details, see Grouping all suspicious request URLs. |
| Server Protection Threshold |
Enter the number of detected attacks to match or exceed. When the number of attacks meets or exceeds this threshold, FortiWeb interprets the attacks as a false positive and the protection profile that the auto-learning feature generates disables scanning for this attack signature for the entire web site. |
| Server Protection Exception Threshold |
Enter a percentage of detected attacks directed at a specific URL relative to the total number of attacks for the entire web site. When the percentage of attacks for a URL meets or exceeds this threshold, and the number of detected attacks for the corresponding attack signature does not exceed the Server Protection Threshold value, the protection profile that the auto-learning feature generates includes an exception that disables scanning for the attack signature for the URL. FortiWeb still uses the signature to scan URLs that do not receive attack traffic that exceeds this threshold.
For example, if an average of 50% of all requests to the web site match an attack signature, are destined for a specific URL, and are actually harmless, you can adjust this setting to |
| Application Policy |
Select a URL interpreter set to use, if any. If the web application embeds parameters in the URL or uses non-standard parameter separators, include an auto-learning adaptor to define how auto-learning should find parameters in the URL. For details, see How to adapt auto-learning to dynamic URLs & unusual parameters. |
5. Click OK.
6. In a server policy, select the auto-learning profile with its protection profile in Web Protection Profile and Auto Learn Profile (see Configuring a server policy). If you do not want to change all Action settings to Alert in each of the protection profile’s components, also enable Monitor Mode.
7. To ensure that the appliance can learn about HTTP/HTTPS requests’ usual page order and other session-related attacks and features, enable the Session Management option in the protection profile.
8. Continue with Running auto-learning.