
You can configure rules to validate parameters (input) of your web applications.
Input rules define whether or not parameters are required, and their maximum allowed length, for requests that match both the:
as defined in the input rule. Inputs are typically the <input> tags in an HTML form.
type attribute is text; Password’s type attribute is password

For example, one web page might have an HTML form with multiple inputs:
Within the input rule for that web page, you can define separate rules for each parameter in the request: one rule for the user name parameter, one rule for the password parameter, and one rule for the preference parameter. You can use the password rule to enforce password complexity by requiring it to match a Level 2 Password data type.
Unlike hidden field rules, input rules are for visible inputs only, such as buttons and text areas. For information on constraining hidden inputs, see Preventing tampering with hidden inputs.
Each input rule contains one or more individual rules. Collectively, individual rules define all parameter restrictions that apply to requests matching the specified URL and host name combination.
If an HTTP/HTTPS request contains repeated parameters, FortiWeb enforces the input rules for all instances of the parameter — not just the first time it occurs in the request.
|
|
FortiWeb cannot enforce the rule if the parameter is bigger than the memory size you have configured for FortiWeb’s scan buffers. To configure the buffer size, see http-cachesize in the FortiWeb CLI Reference. If your web applications do not require requests larger than the buffer, enable Malformed Request to harden your configuration. |
1. Before you configure an input rule, if you want to apply it only to HTTP requests for a specific real or virtual host, you must first define the web host in a protected host names group (see Defining your protected/allowed HTTP “Host:” header names). If you want to define your own data types, you should also configure those first (see Defining custom data types).
2. Go to Web Protection > Input Validation > Parameter Validation Rule.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Web Protection Configuration category. For details, see Permissions.
3. Click Create New.
A dialog appears.
4. Configure these settings:

| Setting name | Description |
|---|---|
| Name | Type a unique name that can be referenced in other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters. |
| Host Status |
Enable to apply this input rule only to HTTP requests for specific web hosts. Also configure Host. Disable to match the input rule based upon the other criteria, such as the URL, but regardless of the |
| Host |
Select which protected host names entry (either a web host name or IP address) that the This option is available only if Host Status is enabled. |
| Request URL Type | Select whether the Request URL field must contain a literal URL (Simple String), or a regular expression designed to match multiple URLs (Regular Expression). |
| Request URL |
Depending on your selection in Request URL Type, type either:
Do not include the domain name, such as To create and test a regular expression, click the >> (test) icon. This opens the Regular Expression Validator window where you can fine-tune the expression (see Regular expression syntax and Cookbook regular expressions). |
| Action |
Select which action the FortiWeb appliance will take when it detects a violation of the rule:
The default value is Alert. See also Reducing false positives. Caution: This setting will be ignored if Monitor Mode is enabled. Note: Logging and/or alert email will occur only if enabled and configured. See Logging and Alert email. Note: If you will use this rule set with auto-learning, you should select Alert. If Action is Alert & Deny, or any other option that causes the FortiWeb appliance to terminate or modify the request or reply when it detects an attack attempt, the interruption will cause incomplete session information for auto-learning. |
| Block Period |
Type the number of seconds that you want to block subsequent requests from the client after the FortiWeb appliance detects that the client has violated the rule. This setting is available only if Action is set to Period Block. The valid range is from 1 to 3,600 (1 hour). The default value is 1. See also Monitoring currently blocked IPs. |
| Severity |
When rule violations are recorded in the attack log, each log message contains a Severity Level (
The default value is High. |
| Trigger Action | Select which trigger, if any, that the FortiWeb appliance will use when it logs and/or sends an alert email about a violation of the rule. See Viewing log messages. |
5. Click OK.
6. Click Create New to add an entry to the set. You can add up to 1,024.
A dialog appears.
7. Configure these settings:

| Setting name | Description |
|---|---|
| Name Type |
Select one of the following options:
|
| Name |
Enter one of the following:
Note: FortiWeb does not support regular expressions that begin with an exclamation point ( ! ). For information on language and regular expression matching, see Regular expression syntax. |
| Max Length |
Type the maximum length of the string that is the input’s value. For example, if the input’s value is always a short string like To disable the length limit, type Tip: See also Malformed Request. |
| Required | Enable if the parameter is required for HTTP/HTTPS requests to this combination of Host: field and URL. |
| Use Type Check | Enable to validate the data type of the parameter. Also configure Argument Type. |
| Argument Type |
Select one of:
This option is only applicable when Use Type Check is enabled. |
| Data Type |
Select a predefined data type. See Auto-learning. This option is only available when Argument Type is Data Type. |
| Regular Expression |
Type a regular expression that matches all valid values, and no invalid values, for this input. This option is only available when Argument Type is Regular Expression. To create and test a regular expression, click the >> (test) icon. This opens the Regular Expression Validator window where you can fine-tune the expression (see Regular expression syntax). |
| Custom Data Type |
Select a custom data type. See Defining custom data types. This option is only available when Argument Type is Custom Data Type. |
8. Click OK.
9. Repeat the previous steps for each individual validation rule that you want to add to the group of validation rules.
10. Go to Web Protection > Input Validation > Parameter Validation Policy.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Web Protection Configuration category. For details, see Permissions.
11. Click Create New.
A dialog appears.
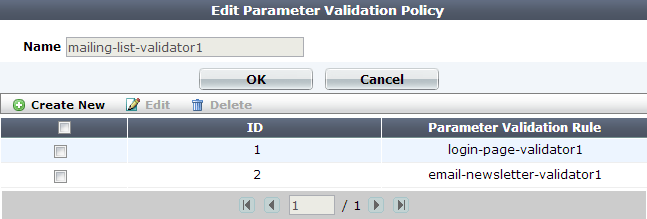
12. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
13. Click OK.
14. Click Create New to add an entry to the set.
A dialog appears.
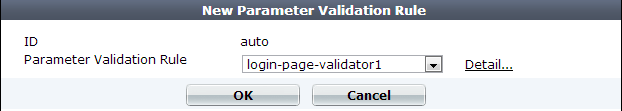
15. From the rule drop-down list, select the name of an existing input validation rule.
To view or change the information associated with the rule, select the Detail link. The Edit Parameter Validation Rule dialog appears. Use the browser Back button to return.
16. Click OK.
17. Repeat the previous steps for each input rule that you want to add to the parameter validation rule.
18. To apply the parameter validation policy, select it in an inline or offline protection profile (see Configuring a protection profile for inline topologies or Configuring a protection profile for an out-of-band topology or asynchronous mode of operation).
Attack log messages contain Parameter Validation Violation when this feature detects a parameter rule violation.
|
|
If you do not want sensitive inputs such as passwords to appear in the attack logs’ packet payloads, you can obscure them. For details, see Obscuring sensitive data in the logs. |
If you need to make the same change to multiple parameter validation rules, you can apply some changes as a batch instead of individually.
1. Go to Web Protection > Input Validation > Parameter Validation Rule.
2. Mark the check boxes of all rules that will receive the same change. Additional buttons will become available on the tool bar, such as Edit Action, Edit Trigger Policy, or Edit Severity.
3. Click one of those buttons, then from the drop-down menu that appears, select the new value for setting.

In addition to using the predefined regular expressions that FortiWeb has to detect data types, you can also configure your own custom data types.
|
|
Unlike predefined data types, custom data types cannot be used by auto-learning profiles. |
|
|
To create a custom data type by modifying a predefined data type, copy the text in the Auto-learning column of the predefined data type, then paste it into a custom data type. |
1. Go to Auto Learn > Custom Pattern > Data Type.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Server Policy Configuration category. For details, see Permissions.
2. Click Create New.
A dialog appears.

3. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
4. In Expression, enter a regular expression that defines this data type.
5. To test the regular expression against sample text, click the >> (test) icon. This opens the Regular Expression Validator window where you can fine-tune the expression (see Regular expression syntax).
6. Click OK.
7. To use a custom data type, select it when configuring an input rule. For details, see Validating parameters (“input rules”).