FortiWeb can generate reports based on:
When generating a log-based or scan-based report, FortiWeb appliances collate information collected from log files and scan results, and present the information in tabular and graphical format.
Before it can generate a report, in addition to log files and scan results, FortiWeb appliances require a report profile in order to generate a report. A report profile is a group of settings that contains the report name, file format, subject matter, and other aspects that the FortiWeb appliance considers when generating the report.
FortiWeb appliances can generate reports automatically, according to the schedule that you configure in the report profile, or manually, when you click the Run now icon in the report profile list.
|
|
Generating reports can be resource intensive. To avoid traffic processing performance impacts, you may want to generate reports during times with low traffic volume, such as at night or weekends. For more information on scheduling the generation of reports, see Scheduling reports. To determine the current traffic volume, see Real Time Monitor widget. |
|
|
Consider sending reports to your web developers to provide feedback. If your organization develops web applications in-house, this can be a useful way to quickly provide them information on how to improve the security of the application. |
1. Before you generate a report, collect log data and/or vulnerability scan data that will be the basis of the report. For information on enabling logging to the local hard disk, see Configuring logging and Vulnerability scans.
2. Go to Log&Report > Report Config > Report Config.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Log & Report category. For details, see Permissions.
3. Click Create New.
A dialog appears.

4. In Report Name, type the name of the report as it will be referenced in the configuration. The name cannot contain spaces.
5. If you are creating a new report profile, select from Type either to run the report immediately after configuration (On Demand) or run the report at configured intervals (On Schedule). This cannot be changed later.
|
|
For on-demand reports, the FortiWeb appliance does not save the report profile after the generating the report. If you want to save the report profile, but do not want to generate the report at regular intervals, select On Schedule, but then in the Schedule section, select Not Scheduled. |
6. In Report Title, type a display name that will appear in the title area of the report. The title may include spaces.
7. In Description, type a comment or other description.
8. Click the blue expansion arrow next to each section, and configure the following:
| Setting name | Description |
|---|---|
| Properties | Select to add logos, headers, footers and company information to customize the report. For more information, see Customizing the report’s headers, footers, & logo. |
| Report Scope | Select the time span of log messages from which to generate the report. You can also create a data filter to include in the report only those logs that match a set of criteria. For more information, see Restricting the report’s scope. |
| Report Types | Select one or more subject matters to include in the report. For more information, see Choosing the type & format of a report profile. |
| Report Format | Select the number of top items to include in ranked report subtypes, and other advanced features. For more information, see Choosing the type & format of a report profile. |
| Schedule |
Select when the FortiWeb appliance will run the report, such as weekly or monthly. For more information, see Scheduling reports. This section is available only if Type is On Schedule. |
| Output | Select the file formats and destination email addresses, if any, of reports generated from this report profile. For more information, see Selecting the report’s file type & delivery options. |
9. Click OK.
On-demand reports are generated immediately. Scheduled reports are generated at intervals set in the schedule. For information on viewing generated reports, see Viewing & downloading generated reports.
1. Mark the check box of the report.
2. Click Run now.
When configuring a report profile, you can provide text and logos to customize the appearance of reports generated from the profile.

| Setting name | Description |
|---|---|
| Company Name | Type the name of your company or other organization. |
| Header Comment | Type a title or other information to include in the header. |
| Footer Comment |
Select which information to include in the footer:
|
| Title Page Logo |
Select No Logo to omit the title page logo. Select Custom to include a logo, then click Select to locate the logo file, and click Upload to save it to the FortiWeb appliance’s hard disk for use in the report title page. See To upload a logo file. |
| Header Logo |
Select No Logo to omit the header logo. Select Custom to include a logo, then click Select to locate the logo file, and click Upload to save it to the FortiWeb appliance’s hard disk for use in the report header. The header logo will appear on every page in PDF- and Microsoft Word (RTF)-formatted reports, and at the top of the page in HTML-formatted reports. |
1. Expand the Properties section of the Log Report Config dialog. (See To configure a report profile.)
2. Select the Custom option of either Title Page Logo or Header Logo.
3. Click the Select link.
A dialog appears.
4. Click Browse and locate the logo file on your computer.
5. Click Upload.
A rendering of the logo appears in the dialog.
6. Select the logo and click OK.
The name of the logo appears next to Custom on the Log Report Config.
When adding a logo to the report, select a logo file format that is compatible with your selected file format outputs. If you select a logo that is not supported for a file format, the logo will not appear in that output. For example, if you provide a logo graphic in WMF format, it will not appear in PDF or HTML output.
| PDF reports | JPG, PNG, GIF |
| RTF reports | JPG, PNG, GIF, WMF |
| HTML reports | JPG, PNG, GIF |
1. Expand the Properties section of the Log Report Config dialog. (See To configure a report profile.)
2. Click the Select link beside the logo name you want to remove in either Title Page Logo or Header Logo.
A dialog appears.
3. Select the logo to remove.
4. Click Delete.
When configuring a report profile, you can select the time span of log messages from which to generate the report. You can also filter out log messages that you do not want to include in the report. (To start at the beginning of the report configuration instructions, see To configure a report profile.)

| Setting name | Description | |
|---|---|---|
| Time Period |
Select the time span of the report, such as This Month or Last N Days. |
|
|
Past N Hours Past N Days Past N Weeks |
Enter the number N of the appliance of time. This option appears only when you have selected Last N Hours, Last N Days, or Last N Weeks from Time Period, and therefore must define N. |
|
|
Hour |
Select and configure the beginning of the time span. For example, you may want the report to include log messages starting from May 5, 2006 at 6 PM. You must also configure To Date. | |
|
Hour |
Select to configure the end of the time span. For example, you may want the report to include log messages up to May 6, at 12 AM. You must also select and configure From Date. | |
| None | Select this option to include all log messages within the time span. | |
| Include logs that match the following criteria |
Select this option to include only the log messages whose values match your filter criteria, such as Priority . Also select whether log messages must meet every other configured criteria (all) or if meeting any one of them is sufficient (any) to be included. To exclude the log messages which match a criterion, mark its not check box, located on the right-hand side of the criterion. Criteria are the fields of log messages. For more information on log messages, see the FortiWeb Log Reference. |
|
| Priority | Mark the check box to filter by log severity threshold (in raw logs, the pri field), then select the name of the severity, such as Emergency, and whether to include logs that are greater than or equal to (>=), equal to (=), or less than or equal to (<=) that severity. |
|
| Source(s) |
Type the source IP address (in raw logs, the Note: Source(s) may be the IP address according to an HTTP header such as |
|
| Destination(s) | Type the destination IP address (in raw logs, the dst field) that log messages must match. |
|
| Http Method(s) | Type the HTTP method (in raw logs, the http_method field) that log messages must match, such as get or post. |
|
| User(s) | Type the administrator account name (in raw logs, the user field) that log messages must match, such as admin. |
|
| Action(s) | Type the action (in raw logs, the action field) that log messages must match, such as login or Alert. |
|
| Subtype(s) | Type the subtype (in raw logs, the subtype field) that log messages must match, such as waf_information. |
|
| Policy(s) | Type the policy name (in raw logs, the policy field) that log messages must match. |
|
| Service(s) | Type the service name (in raw logs, the src field) that log messages must match, such as http or https. |
|
| Message(s) | Type the message (in raw logs, the msg field) that log messages must match. |
|
| Signature Subclass Type(s) | Type the signature subclass type (in raw logs, the signature_subclass field) that log messages must match. |
|
| Signature ID(s) | Type the signature ID value (in raw logs, the signature_id field) that log messages must match. |
|
| Source Country(s) | Type the source country value (in raw logs, the srccountry field) that log messages must match. |
|
| Day of Week | Mark the check boxes for the days of the week whose log messages you want to include. | |
When configuring a report profile, you can select one or more queries or query groups that define the subject matter of the report.
When configuring a report profile, you can configure various advanced options that affect how many log messages are used to formulate ranked report subtypes, and how results will be displayed.
(To start at the beginning of the report configuration instructions, see To configure a report profile.)

| Setting name | Description | ||
|---|---|---|---|
| Report Types |
Each query group contains multiple individual queries, each of which correspond to a chart that will appear in the generated report. You can select all queries within the group by marking the check box of the query group, or you can expand the query group and then individually select each query that you want to include: For example:
|
||
| Report Format | |||
| Include reports with no matching data | Enable to include reports for which there is no data. A blank report will appear in the summary. You might enable this option to verify inclusion of report types selected in the report profile when filter criteria or absent logs would normally cause the report type to be omitted. | ||
| Advanced | |||
| In ‘Ranked Reports’ show top |
Ranked reports (top x, or top y of top x) can include a different number of results per cross-section, then combine remaining results under “Others.” For example, in Top Sources By Top Destination, the report includes the top x destination IP addresses, and their top y source IP addresses, then groups the remaining results. You can configure both x and y in the Advanced section of Report Format In ranked reports, (“top x” report types, such as Top Attack Type), you can specify how many items from the top rank will be included in the report. For example, you could set the Top Attack URLs report to include up to 30 of the top x denied URLs by entering Some ranked reports rank not just one aspect, but two, such as Top Sources By Top Destination: this report ranks top source IP addresses for each of the top destination IP addresses. For these double ranked reports, you can also configure the rank threshold of the second aspect by entering the second threshold in values of the second variable for each value of the first variable 1..30. Note: Reports that do not include “Top” in their name display all results. Changing the ranked reports values will not affect these reports. |
||
| values of the first variable 1.. 30 | Type the value of x. | ||
| values of the second variable for each value of the first variable 1.. 30 |
Type the value of y. This value is only considered if the report rankings are nested (i.e. top y of top x). |
||
| Include Summary Information | Enable to include a listing of the report profile settings. | ||
| Include Table of Contents | Enable to include a table of contents for the report. | ||
When configuring a report profile, you can select whether the FortiWeb appliance will generate the report on demand or according to the schedule that you configure. (To start at the beginning of the report configuration instructions, see To configure a report profile.)
|
|
Generating reports can be resource-intensive. To improve performance, schedule reports during times when traffic volume is low, such as at night or during weekends. To determine the current traffic volumes, see Real Time Monitor widget. |

| Setting name | Description | |
|---|---|---|
| Schedules | ||
| Not Scheduled |
Select if you do not want the FortiWeb appliance to generate the report automatically according to a schedule. If you select this option, the report will only be generated on demand, when you manually click the Run now icon from the report profile list. For more information, see Reports. |
|
| Daily | Select to generate the report each day. Also configure Time. | |
| These Days | Select to generate the report on specific days of each week, then mark the check boxes for those days. Also configure Time. | |
| These Dates |
Select to generate the report on specific date of each month, then enter those date numbers. Separate multiple date numbers with a comma. Also configure Time. For example, to generate a report on the first and 30th day of every month, enter |
|
| Time |
Select the time of the day when the report will be generated. This option does not apply if you have selected Not Scheduled. |
|
When you configure a report profile, you can select one or more file formats in which to save reports generated from the profile. You can also configure the FortiWeb appliance to email the reports to specific recipients or send them to an FTP or TFTP server. (To start at the beginning the report configuration instructions, see To configure a report profile.)
| Setting name | Description | |
|---|---|---|
| File Output |
Enable file formats that you want to generate and store on the FortiWeb appliance’s hard drive. FortiWeb always generates HTML file format reports (as indicated by the permanently enabled check box), but you can also choose to generate reports in: |
|
| Email Output | Enable file formats that you want to generate for an email that will be mailed to the recipients defined by the email settings. | |
| Email Policy |
Select the predefined email settings that you want to associate with the report output. This determines who receives the report email. For more information on configuring email settings, see Configuring email settings. |
|
| Email Subject | Type the subject line of the email. | |
| Email Body | Type the message body of the email. | |
| Email Attachment Name | Type a file name that will be used for the attached reports. | |
| Compress Report Files | Enable to enclose the generated report formats in a compressed archive, as a single attachment. | |
| FTP/TFTP Output | Select the formats for files that FortiWeb sends to the FTP or TFTP server specified by FTP/TFTP Policy. | |
| FTP/TFTP Policy | Select the policy that defines a connection to the appropriate server. See Configuring FTP/TFTP policies. | |
Log&Report > Report Browse > Report Browse displays a list of generated reports that you can view, delete, and download.
|
|
In FortiWeb HA clusters, generated reports (PDFs, HTML, RTFs, plain text, or MHT) are recorded on their originating appliance. If you cannot locate a report that should have been generated, a failover may have occurred. Reports generated during that period will be stored on the other appliance. To view those reports, switch to the other appliance. |
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Log & Report category. For details, see Permissions.

In addition to log-based reports, FortiWeb also includes data analytics to help you track web server usage from a page hit, traffic volume, and attack point of view.
Before data analytics can provide meaningful information, you must:
1. Upload a geographic location data file (see Updating data analytics definitions).
2. Enable the Data Analytics option on any inline protection or offline protection profile used by your server policies.
3. Wait for the appliance to collect data about traffic flows.
Similar to other signatures and definitions used by FortiWeb, you can update the geographical mappings of public IP addresses to countries used by the data analytics feature.
1. Download the .dat file from the Fortinet Technical Support web site:
If you want to check the integrity of the .dat file, also download its checksum (.md5). For instructions on how to use it, see the documentation for your checksum software.
2. Log in to the web UI of the FortiWeb appliance as the admin administrator, or an administrator account whose access profile contains Read and Write permissions in the Maintenance category.
3. Go to System > Maintenance > Backup & Restore.
To access this submenu, your administrator's account access profile must have Read and Write permission to items in the Maintenance category. For details, see Permissions.
4. In the Data Analytics area, click Browse.

5. Select the .dat file.
6. Click Open.
The file name appears in the From File field.
7. Click Upload.
Your browser uploads the file. A message appears to display the progress of the upload. Time required varies by the size of the file and the speed of your network connection.
Log&Report > Monitor > Data Analytics displays statistics on traffic from clients internationally, web page hits, and attacks. Clients’ locations are determined by source IP address, which is then mapped to its current known location:
|
|
To make sure that the mappings are correct, you should periodically update FortiWeb’s geography-to-IP mappings. See Updating data analytics definitions. If all client IP addresses appear to originate on private networks (“Internal IPs”) and especially from a single IP, SNAT may be interfering and you may need to configure FortiWeb to deduce the client’s location using X-headers instead. See Defining your proxies, clients, & X-headers. |
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Log & Report category. For details, see Permissions.
|
|
The data analytics feature can be resource-intensive. To avoid impacting performance, view the data analytics report in off-peak hours. |
Data analytics organizes the data collected by server policies into two distinct cross-sections. Click the buttons on the top right corner to toggle between:
Geographic Location View — Displays data per clients’ geographical location (e.g. Canada, China, Portugal, Morocco, Brazil, Australia, etc.) in graphical format.
While this view is selected, a format toggle appears below the view toggle. The format toggle allows you to choose what will accompany the data analytics charts: either List (for a table of statistics by country) or Map (for a map of the Earth). To display the statistics for a country/region, hover your mouse cursor over it. The statistics will appear in a tool tip.
If you click a specific country/region on the map of the Earth, the map will zoom in to show the states within that area. Similar to the view of the entire Earth, to display statistics for a sub-region, hover your mouse cursor over it. The statistics appear in a tool tip.
|
|
If traffic from a country is predominantly attacks instead of legitimate requests, you can block it. See Blacklisting & whitelisting countries & regions. |
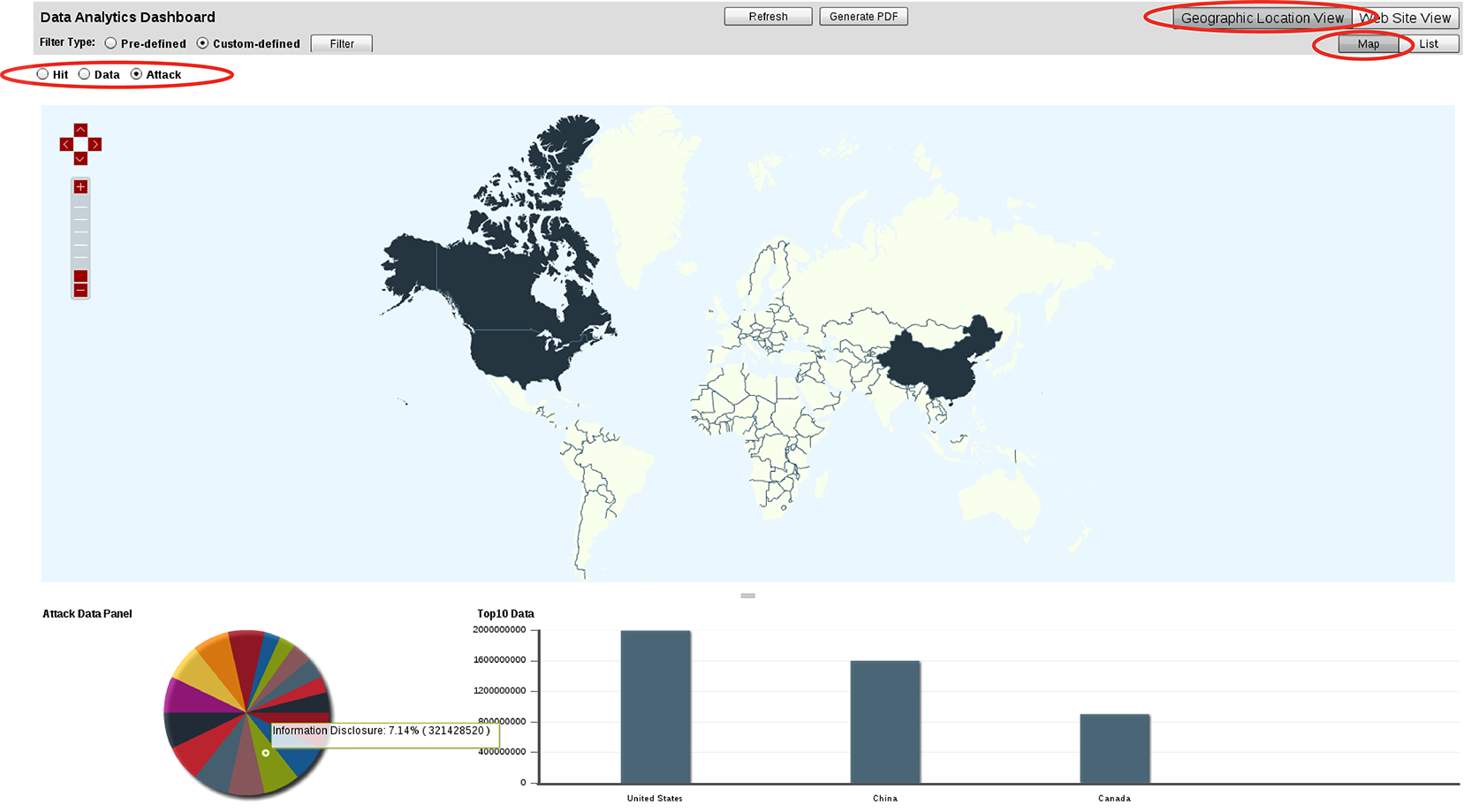

Select either:
|
|
Geographic location is based upon the apparent origin according to the source IP address of the request. Accuracy may vary due to network address translation (NAT) and/or clients’ use of proxies such as Tor and IPSec, SSH, or other VPN tunnels which alter the source IP address in packets and therefore can cause clients’ traffic to appear to originate from a location other than their actual location. |
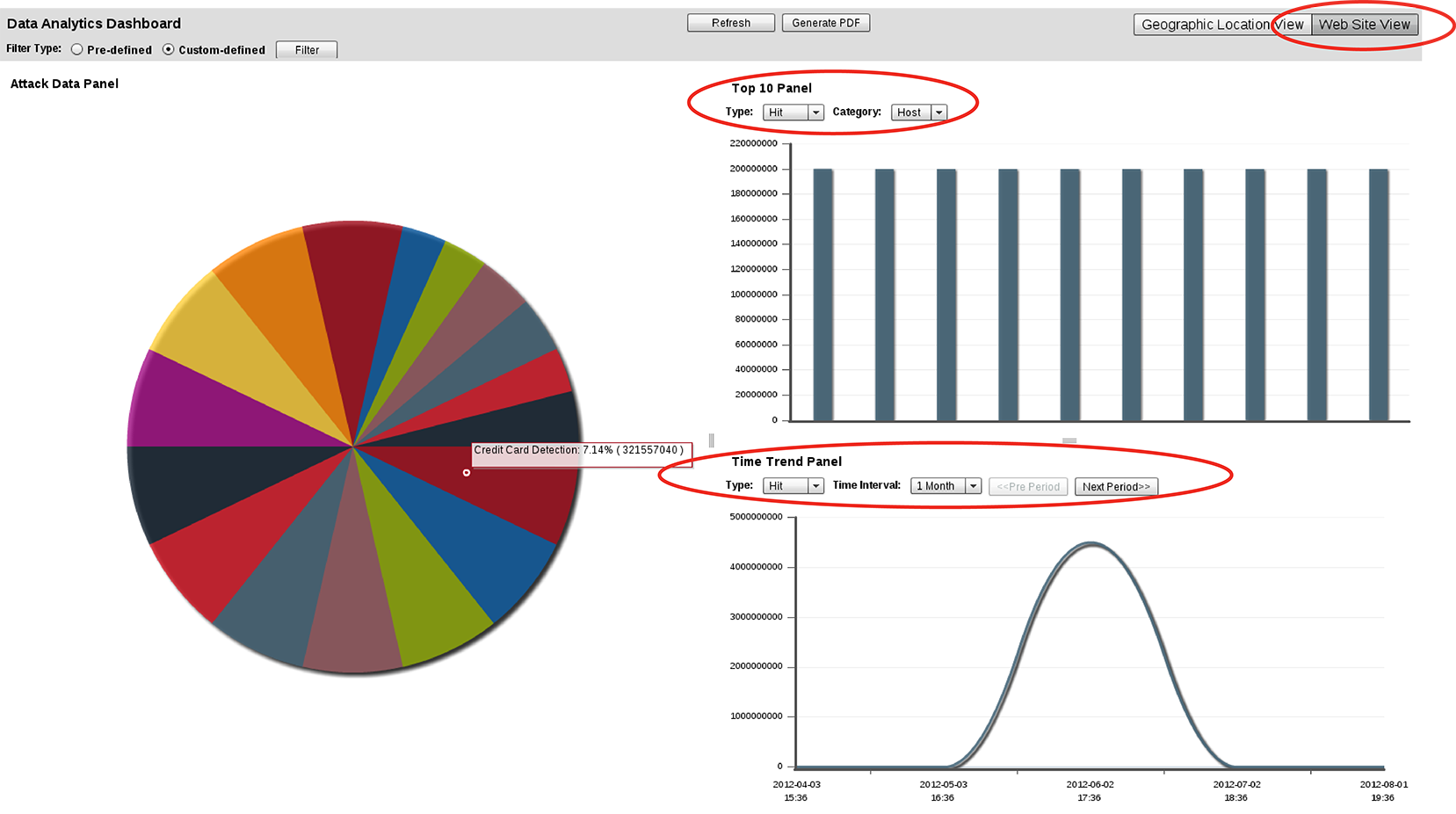
From the Type drop-down lists, select either:
In the Top 10 Panel, from the Category drop-down list, select either:
In the Time Trend Panel, from the Time Interval drop-down list, select a time interval (e.g. 1 Week), then click the Pre Period (previous) and Next Period buttons to advance by that interval through the time span that you have selected in either Time Range or your custom data filter.
For example, if Type is Attack and Category is Host, the panel displays the 10 domains that received the most attack attempts. Let’s say that a trend of attacking www.example.com is consistent over time. (You could confirm this suspicion in the Time Trend Panel.) This could represent either an advanced persistent threat (APT) — an attacker that is an adversary of that specific organization, and likely to continue and attempt more evolved threats until she or he discovers a viable exploit — or it could simply be an attack attempt because security-wise, that specific web server is an easy target. Attacks on weak hosts might be discouraged by applying patches, cloaking the web server, configuring sever protection rules on FortiWeb to mitigate the host’s weaknesses, etc. An APT however, indicates a collectively greater risk than a lone attack attempt against a weak host, and will likely continue regardless of increasing attack difficulty. If you determine that the attacker(s) is an APT, you might decide to devote more resources to protecting that web server, including a full web application source code and security practice audit, as well as configuring anti-defacement.
Both cross-sections have common controls:
Host:), URL, policy name, and/or time span to include matching statistics. For details, see Filtering the data analytics report.By default, in Filter Type, the Pre-defined option is selected, and so the data analytics reports include statistics based solely upon one of a few pre-defined time periods, which you can select from Time Range.
However, you can define your own time span, as well as filter statistics based upon criteria other than time.
1. Go to Log&Report > Monitor > Data Analytics.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Log & Report category. For details, see Permissions.
2. Select the view to use: Web Site View or Geographic Location View.
3. From Filter Type, select the Custom-defined option.
4. Click Filter.
A dialog appears.
5. Configure the following criteria, if any, that a statistic must match in order to be included in the report:

| Setting name | Description | |
|---|---|---|
| Policy | Type the name of a server policy that is gathering data for data analytics. It must use a profile where you have enabled Data Analytics. Otherwise, it will not include any statistics. | |
| Host | Type a domain name or IP address in the Host: field of the HTTP header of requests. |
|
| URL | Type a URL. It usually should be a web page that initiates a session. (Session-initiating URL hit counts may more closely correlate to visit counts. For example, web application preference pages are seldom visited in a session.) | |
| Case Sensitivity |
Enable to differentiate uniform resource locators (URLs) and For example, when this option is enabled, an HTTP request involving |
|
| Use Time Filter | Enable to use only statistics within a specific time period, defined by From and To. | |
| From | Click the calendar icon or its accompanying text field to define the date at the beginning of the time period, then select the Hour, Minute, and Second to define the time of day. | |
| To | Click the calendar icon or its accompanying text field to define the date at the end of the time period, then select the Hour, Minute, and Second to define the time of day. | |
6. Click OK.
The page refreshes and displays data restricted by the new filter. The filter applies until you either:
In Filter Type, choose Pre-defined, then select a predefined Time Range.
Clear the filter by clicking the Filter button to raise the dialog again, click Reset, then click OK.
Log&Report > Monitor > Bot Analysis displays statistics on access by automated clients such as search engine indexers, content scrapers, and other tools. Statistics are gathered by Real Browser Enforcement in anti-DoS rules, Bad Robot and Allow Known Search Engines. Based on this data, if an automated tool is abusing access, you can configure rate limiting such as with Combination access control & rate limiting.
