You can block requests from clients based upon their source IP address directly, their current reputation known to FortiGuard, or which country or region the IP address is associated with.
Conversely, you can also exempt clients from scans typically included by the policy.
Manually identifying and blocking all known attackers in the world would be an impossible task. To block:
you can configure FortiWeb to use the FortiGuard IP Reputation. IP reputation leverages many techniques for accurate, early, and frequently updated identification of compromised and malicious clients so you can block attackers before they target your servers. Data about dangerous clients derives from many sources around the globe, including:
From these sources, Fortinet compiles a reputation for each public IP address. Clients will have poor reputations if they have been participating in attacks, willingly or otherwise. Because blacklisting innocent clients is equally undesirable, Fortinet also restores the reputations of clients that improve their behavior. This is crucial when an infected computer is cleaned, or in DHCP or PPPoE pools where an innocent client receives an IP address that was previously leased by an attacker.
|
|
Because IP reputation data is based on evidence of hostility rather than a client’s current physical location on the globe, if your goal is to block attackers rather than restrict delivery, this feature may be preferable. |
IP reputation knowledge is regularly updated if you have subscribed and connected your FortiWeb to the FortiGuard IP Reputation service (see Connecting to FortiGuard services). Due to this, new options appear periodically. You can monitor the FortiGuard web site feed for security advisories which may correlate with new IP reputation-related options.
|
|
Because geographical IP policies are evaluated before many other techniques, defining these IP addresses can be used to improve performance. For details, see Sequence of scans. |
|
|
The IP Reputation feature can block or log clients based on X-header-derived client source IPs. See Defining your proxies, clients, & X-headers. |
1. If you need to exempt some clients’ public IP addresses due to possible false positives, configure IP reputation exemptions first. Go to IP Reputation > IP Reputation > Exceptions.
2. Go to IP Reputation > IP Reputation > Policy.
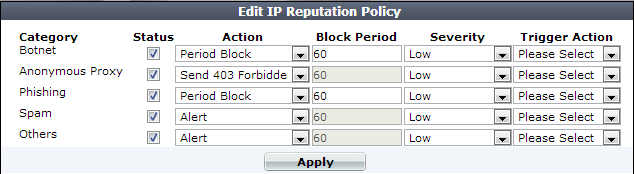
3. In the Status column, enable categories of disreputable clients that you want to block and/or log.
4. Similar to configuring attack signatures, also configure Action, Block Period, Severity, and Trigger Action.
5. Click Apply.
6. To apply your IP reputation policy, enable IP Reputation in a protection profile that is used by a policy (see Configuring a protection profile for inline topologies or Configuring a protection profile for an out-of-band topology or asynchronous mode of operation).
Attack log messages contain Anonymous Proxy : IP Reputation Violation or Botnet : IP Reputation Violation when this feature detects a possible attack.
While many web sites are truly global in nature, others are specific to a region. Government web applications that provide services only to its residents are one example.
In such cases, when requests appear to originate from other parts of the world, it may not be worth the security risk to accept them.
Blacklisting clients individually in this case would be time-consuming and difficult to maintain due to PPPoE or other dynamic allocations of public IP addresses, and IP blocks that are re-used by innocent clients.
FortiWeb allows you to block traffic from many IP addresses that are currently known to belong to networks in other regions. It uses a MaxMind GeoLite database of mappings between geographical regions and all public IP addresses that are known to originate from them.
You can also specify exceptions to the blacklist, which allows you to, for example, block a country or region but allow a geographic location within that country or region. If you enable Allow Known Search Engines,
|
|
Because network mappings may change as networks grow and shrink, if you use this feature, be sure to periodically update the geography-to-IP mapping database. To download the file, go to the Fortinet Technical Support web site. |
|
|
This scan is bypassed if the client’s source IP is a known search engine and you have enabled Allow Known Search Engines. |
|
|
Because geographical IP policies are evaluated before many other techniques, defining these IP addresses can be used to improve performance. For details, see Sequence of scans. |
1. Verify that client source IP addresses are visible to FortiWeb in either the X-headers or as the SRC field at the IP layer (see Defining your web servers & load balancers).
If FortiWeb is behind an external load balancer that applies SNAT, for example, you may need to configure it to append its and the client’s IP address to X‑Forwarded‑For: in the HTTP header so that FortiWeb can apply this feature. Otherwise, all traffic may appear to come from the same client, with a private network IP: the external load balancer.
2. If you want to use a trigger to create a log message and/or alert email when a geographically blacklisted client attempts to connect to your web servers, configure the trigger first. See Viewing log messages.
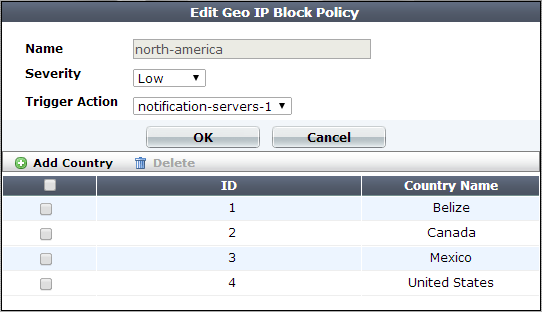
3. If you need to exempt some clients’ public IP addresses, configure Geo IP reputation exemptions first:
192.168.0.1) or IP ranges (for example, 192.168.0.1-192.168.0.255) to the exception item, as required.4. Go to Web Protection> Access > Geo IP.
5. Click Create New.
A dialog appears.
6. Configure these settings:
| Setting name | Description |
|---|---|
| Name | Type a name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters. |
| Severity |
When rule violations are recorded in the attack log, each log message contains a Severity Level (
|
| Trigger Action | Select which trigger, if any, that the FortiWeb appliance uses when it logs and/or sends an alert email about a blacklisted IP address’s attempt to connect to your web servers. See Viewing log messages. |
| Exception | Select the exceptions configuration you created in step 3, if required. |
7. Click OK.
8. Click Create New.
9. From the Country list on the left, select one or more geographical regions that you want to block, then click the right arrow to move them to the Selected Country list on the right.
In addition to countries, the Country list also includes distinct territories within a country, such as Puerto Rico and United States Minor Outlying Islands, and regions that are not associated with any country, such as Antarctica.
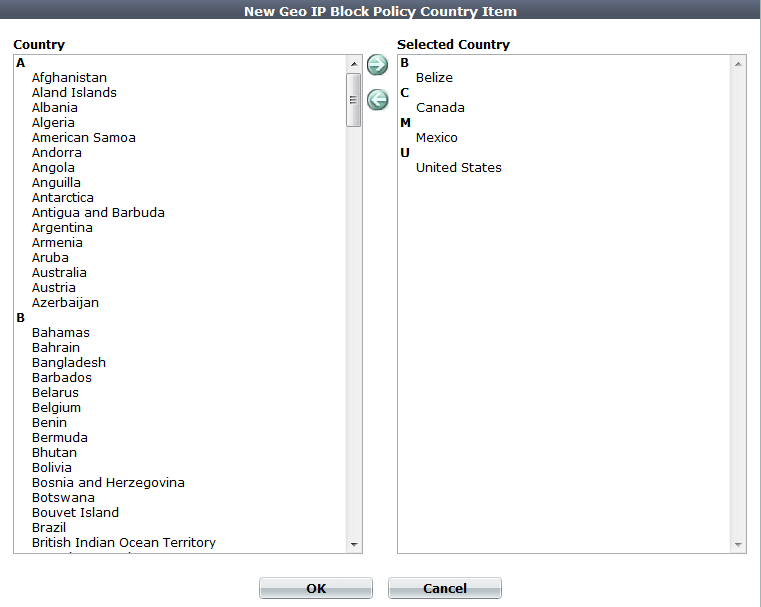
10. Click OK.
The web UI returns to the initial dialog. The countries that you are blocking will appear as individual entries.
11. Click OK.
12. To apply your geographical blocking rule, select it in a protection profile (see Configuring a protection profile for inline topologies or Configuring a protection profile for an out-of-band topology or asynchronous mode of operation) that is being used by a server policy.
You can define which source IP addresses are trusted clients, undetermined, or distrusted.
If a source IP address is neither explicitly blacklisted or trusted by an IP list policy, the client can access your web servers, unless it is blocked by any of your other configured, subsequent web protection scan techniques (see Sequence of scans).
Because many businesses, universities, and even now home networks use NAT, a packet’s source IP address may not necessarily match that of the client. Keep in mind that if you black list or white list an individual source IP, it may therefore inadvertently affect other clients that share the same IP.
|
|
X-header-derived client source IPs (see Defining your proxies, clients, & X-headers) do not support this feature in this release. If FortiWeb is deployed behind a load balancer or other web proxy that applies source NAT, this feature will not work. |
|
|
Because trusted and blacklisted IP policies are evaluated before many other techniques, defining these IP addresses can be used to improve performance. For details, see Sequence of scans. |
1. If you want to use a trigger to create a log message and/or alert email when a blacklisted client attempts to connect to your web servers, configure the trigger first. See Viewing log messages.
2. Go to Web Protection> Access > IP List.
To access this part of the web UI, your administrator’s account access profile must have Read and Write permission to items in the Web Protection Configuration category. For details, see Permissions.
3. Click Create New.
A dialog appears.
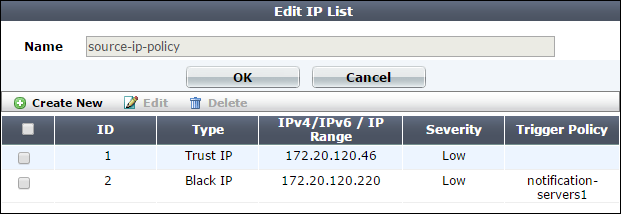
4. In Name, type a unique name that can be referenced by other parts of the configuration. Do not use spaces or special characters. The maximum length is 35 characters.
5. Click OK.
6. Click Create New to add an entry to the set.
A dialog appears.
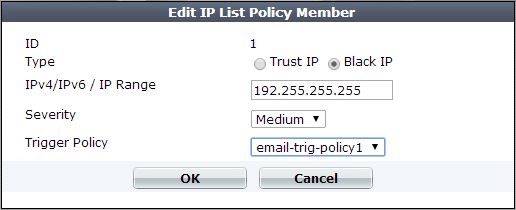
7. Configure these settings:
| Setting name | Description |
|---|---|
| Type |
Select either:
Note: If multiple clients share the same source IP address, such as when a group of clients is behind a firewall or router performing network address translation (NAT), blacklisting the source IP address could block innocent clients that share the same source IP address with an offending client. |
| IPv4/IPv6 / IP Range |
Type the client’s source IP address. You can enter either a single IP address or a range of addresses (e.g., |
| Severity |
When rule violations are recorded in the attack log, each log message contains a Severity Level (
|
| Trigger Action | Select which trigger, if any, that the FortiWeb appliance will use when it logs and/or sends an alert email about a blacklisted IP address’s attempt to connect to your web servers. See Viewing log messages. |
8. Click OK.
9. Repeat the previous steps for each individual IP list member that you want to add to the IP list.
10. To apply the IP list, select it in an inline or offline protection profile (see Configuring a protection profile for inline topologies or Configuring a protection profile for an out-of-band topology or asynchronous mode of operation).
Attack log messages contain Blacklisted IP blocked when this feature detects a blacklisted source IP address.
You can use FortiWeb features to control access by Internet robots such as:
FortiWeb keeps up-to-date the predefined signatures for malicious robots and source IPs if you have subscribed to FortiGuard Security Service.
To block typically unwanted automated tools, use Bad Robot.
To control which search engine crawlers are allowed to access your sites, go to Server Objects > Global > Known Search Engines; also configure Allow Known Search Engines.