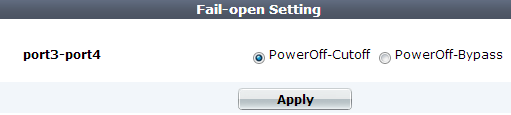
Fail-open is supported only:
- in true transparent proxy mode or transparent inspection operation mode
- in standalone mode (not HA)
- for a bridge (V‑zone) between ports wired to a CP7 processor or other hardware which provides support for fail-to-wire
FortiWeb-400B/400C, FortiWeb HA clusters, and ports not wired to a CP7/fail-open chip do not support fail-to-wire.