FortiEMS Endpoint Tagging
- Overview
- Updated Remediation Scripts
- Fortinet FortiEMS (Endpoint Management Server) Discovery Setup
- Best Practice Setup
- Scheduling Automatic Tagging Example
Overview
FortiSIEM now supports discovery of your FortiEMS servers using the FortiEMS Management Server API with basic authentication (username/password).
FortiSIEM will poll EMS, on a regular interval (default 5 min), and retrieve all vulnerabilities detected for managed FortiClient devices. FortiSIEM will send these as log events, which will create a CMDB entry for each device as unmanaged, if they don't already exist. You can then view vulnerability data about the FortiClient managed devices from the CMDB.
When FortiEMS discovery is done, FortiSIEM can tag or untag a host, using classification tags on FortiEMS server. In ZTNA, these tags are imported by member Fortinet devices, particularly FortiGate firewalls, and are referenced in ZTNA firewall rules.
A common use case would be tagging a host as suspicious, or potentially compromised, and having Firewall rules isolate or allow minimal network traffic for FortiClient managed devices that are assigned those tags.
Updated Remediation Scripts
FortiSIEM has updated several automated response (remediation) scripts to work with FortiEMS.
You can now, adhoc or via automation policy, execute a remediation script, via the Incidents page (From Incidents, select an incident and select Remediate Incident from the Actions drop-down list, and set/unset tag for the device in FortiEMS.) or Analytics > Investigation page.
This allows rules that have tags defined, to assign those tags to relevant hosts in the incident, that are also FortiClient managed devices.
The two primary remediation scripts are:
- Set tag for device in FortiEMS
- Unset tag for device in FortiEMS
Fortinet FortiEMS (Endpoint Management Server) Discovery Setup
To set up FortiEMS discovery, you will need to configure FortiEMS, then configure FortiSIEM.
Note: If you are just pulling in vulnerability data, you can just use a read only user role. If you'd like to use FortiSIEM remediation scripts to set/unset EMS tags of FortiClient host devices, some write permissions are required.
FortiEMS Configuration
Here, you will configure an admin role, and create an administrator user with the configured admin role. Take the following steps.
- Login to FortiEMS Server.
- Navigate to Administration > Admin Roles.
- Click Add.
- In the Name field, enter a name, such as "read_plus_tagging" (or your preferred role name).
- (Optional) In the Description field, enter a description, for example: "Used by FortiSIEM to ingest vulnerability data and create/set/unset EMS tags.".
- Under Endpoint permissions, select the following checkboxes.
- Block/Unblock/Quarantine/Unquarantine/Reregister endpoints
- View group assignment rules
- View endpoint filter bookmarks
- View quarantine management
- View software inventory
- Block/Unblock/Quarantine/Unquarantine/Reregister endpoints
- Under Policy permissions, select the following checkboxes.
- View endpoint policies
- View endpoint profiles
- View Zero Trust tagging rules
- View installers
- View CA certificates
- View on-fabric detection rules
- Under Settings permissions, select the following checkboxes.
- View EMS settings
- View Fortinet services settings
- View alert settings
- View custom message settings
- View features select settings
- Click Save.
- Navigate to Administration > Administrators.
- Click Add.
- In the Add user window, select Create a new user.
- In the Username field, enter a name, for example "fortisiem_user".
- From the Role drop-down list, select the role created, earlier - "read_plus_tagging".
- (optional) Toggle Restrict Login to Trusted Hosts on and add the IP of FortiSIEM component (IP of FortiSIEM node completing the discovery e.g. collector IP address).
- Click Next.
- In the Password and Confirm Password fields, enter a password that meets the FortiEMS requirements and click Finish.
FortiSIEM Configuration
With the FortiEMS admin user configured, you will set up FortiSIEM with the admin user credentials. Take the following steps.
- Login to the FortiSIEM GUI.
- Navigate to Admin > Setup > Credentials.
- Under Step 1: Enter Credentials, click New.
- In the Name field, enter a credential, for example, "EMS_Server" (or your arbitrary name for the credential).
- From the Device Type drop-down list, enter/select Fortinet FortiClient EMS.
- Confirm Access Protocol is set to FORTIEMS_API. If not, select it.
- Leave the Pull Interval at 5 minutes, or optionally change it to 1 minute to 24 hours (1440 minutes). 5 minutes is recommended.
- Change the Port number if the admin port is different than the default 443.
- In the Serial Number field, enter your serial number of your EMS server.
Note: To get the EMS server serial number, login to your EMS server, navigate to Dashboard > Status. The serial number will appear next to Serial Number. The serial number is important for remediation script automation, discussed later. - In the User Name field, enter the FortiEMS admin username created earlier.
- In the Password and Confirm Password fields, enter the password associated with the FortiEMS admin username.
- Click Save.
- Under Step 2: Enter IP Range to Credential Associations, click New.
- In the IP/Host Name field, enter the IP address or hostname of the FortiEMS server.
- From the Credentials drop-down list, select the EMS credential you just defined ("EMS_Server").
- Click Save.
- Select the entry just created and click the Test drop-down list and select Test Connectivity without Ping. A pop up will appear and show the Test Connectivity results. Proceed to step 18 when connectivity succeeds.
- Navigate to ADMIN > Setup > Discovery and click New.
- Enter the Name of the discovery entry.
- Select Discovery Type.
- Enter IP address or hostname of the FortiEMS server in the Include entry.
- Click Save.
- Select the identified discovery, and click Discover.
- Click the Pull Events tab at the top of the screen. A yellow star should appear next to your EMS server.
- Wait approximately 5 minutes for the first job to start.
- The Pull Events page will eventually show a green checkbox next to the EMS server job.
- Navigate to Analytics, and confirm that EMS events are seen.
Best Practice Setup
The FortiEMS and the FortiGate firewall discoveries work in tandem to allow automatic tagging of devices via FortiSIEM triggering incidents.
The rough structure looks like this:
- You configure your FortiGate firewalls for API discovery, and user device store observed FortiClient managed devices will be imported into FortiSIEM.
Each of these devices is imported into FortiSIEM CMDB, each with a special attribute called the FortiEMS serial number, which is the EMS server identification that the device is registered to. - You configure your FortiEMS server credential in FortiSIEM. In the credential, you also hand define the FortiEMS serial number, along with the service user account to access FortiEMS.
- You define a number of tags in FortiSIEM by navigating to Admin > Settings > Analytics > Tags, and clicking New to create a tag.
- You edit any desired FortiSIEM rules by navigating to Resources > Rules > <selected rule>, and adding a tag by clicking Edit, navigating to Step 3: Define Action, selecting the tag from the Tag drop-down list, and clicking Save.
Note: For System rules, you may have to clone the rule, disable the old system rule, and edit the cloned rule. - You create an automation policy that includes a remediation action when the given rule is triggered, in our example, we will use "Set tag for device in FortiEMS".
- Navigate to Admin > Settings > General > Automation Policy, and click New.
- From Rules, select the individual rule you have that contains uses of the tag you defined.
- From Affected Orgs, select the affected organizations, if any.
- Next to Run Remediation / Script, click the Edit icon (pencil), then click New.
- For Type, select Remediation Script.
- From the Script drop-down list, select Fortinet FortiClient EMS - Set tag for device in FortiEMS.
- Leave Enforce On blank.
- From the Run On drop-down list, select the target collector that you would like to execute the script from. Remember that if you have IP restrictions on user accounts, you must make sure that the node calling the API is allowed.
- Leave the Tag Name drop-down list alone to allow auto selection, or select a tag to force a particular tag be used.
- Leave the FortiEMS Credential drop-down list alone to allow auto selection, or select which FortiEMS server to execute the script against.
- Click Save.
- Ensure that the Run Remediation/Script checkbox is now checked.
- Click Save.
You can tag FortiClient hosts by IP or Hostname using remediation scripts adhoc via the Incident s page, by taking the following steps.
- Navigate to Incidents.
- Select an incident.
- Click the Actions drop-down list and select Remediate Incident.
- Set/Unset the tag for the device in FortiEMS.

When tagged, the laptop from the screenshot example above now has the additional classification tag in the FortiEMS server below, as shown in the below screenshot:
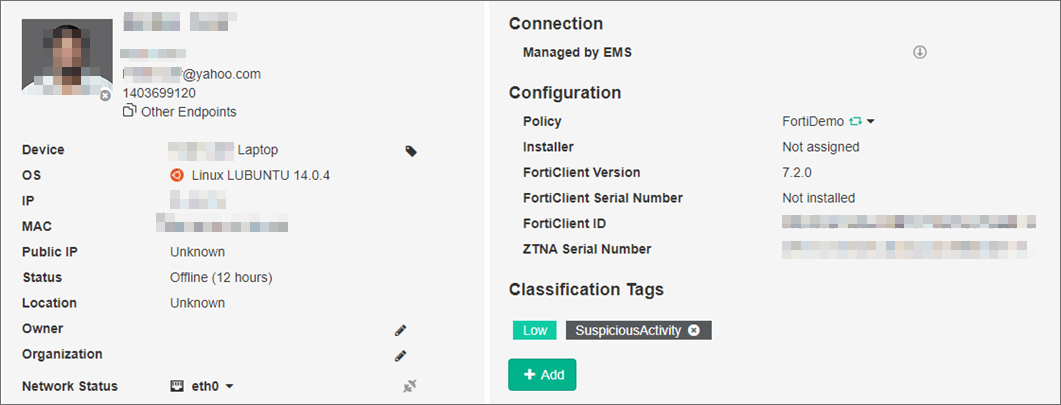
Additional Information on Automatically Tagging a Host
When an incident triggers, and a matching automation policy action exists (in our case, Run Remediation Script), FortiSIEM must dynamically determine what to do.
In the context of tagging a host running FortiClient with a new tag in FortiEMS, it must determine the following based on the incident data.
- Which host to tag
- What tag to use
- Which FortiEMS credential (which EMS server and authentication) to use.
FortiSIEM can only automatically do all 3 if you've followed the best practices above.
- Which host to tag
FortiSIEM looks at the incident source (either hostname or IP address), and if a value can be found, it checks if this device exists in the CMDB.
If it exists in CMDB, it looks at the device's FortiEMS serial number attribute.
If incident source is not found, it looks at incident destination (either hostname or IP address). It also checks if the device exists in CMDB and whether it has a FortiEMS serial number attribute. - What tag to use
If the rule contains a tag value, it will read this.
If the remediation script is executed adhoc by user, you can override this with your own. - Which FortiEMS credential (which FortiEMS server and authentication) to use.
FortiSIEM lists all available FortiEMS Server credentials. Each has an associated serial number attribute.
If the matching CMDB device found in the incident has a FortiEMS serial number match (This indicates the FortiEMS server it is registered to), it will use the associated credential.
Note: If a user is adhoc executing a FortiEMS remediation script (not automatically), then you can forcefully override the automatically detected host, tag, and credential to use.
Example Scenario
The rule "Traffic to FortiGuard Malware IP List" triggered for a given source device. This source is a Windows machine running FortiClient. This device was previously shallow discovered as unmanaged via a FortiGate firewall. Using this method, we know the FortiEMS serial number of the FortiEMS server it is registered to.
We can assign a tag, either within the rule, or during adhoc execution, such as "suspicious_activity", which will be assigned to the host in FortiEMS. Devices such as Firewalls that implement ZTNA policies based on this tag will take action according to how they are defined.
Action overview: FortiSIEM (tag a host) -> FortiEMS server -> Feed hosts and tag data -> FortiGate firewalls -> Implement ZTNA rules based on certain tags -> Take action if matching devices pass through Firewall.
Scheduling Automatic Tagging Example
You can schedule tagging for certain rules via Automation Policy, see here for more information. Two example screenshots below provide an illustration of the following:
If any of the 3 rules selected trigger, FortiSIEM will automatically check the incident source or incident target and if the device exists in the FortiEMS server, it will be tagged with the tag "SuspiciousActivity".


