System Settings
The following section describes the procedures for system settings:
- UI Settings
- Email Settings
- Image Server Settings
- Cluster Config
- Lookup Settings
- Kafka Settings
- Dashboard Slideshow Settings
- Dashboard Ownership
- PAYG Report
- Trusted Hosts
UI Settings
There are two locations where you can change UI settings in FortiSIEM. One location is in the user profile. The other is in the administrator settings.
User Profile UI Settings
The initial view of FortiSIEM UI after login can be configured using the UI settings including dashboard, logos, and theme.
Click the User Profile icon (![]() ) in the upper right corner of the UI. The dialog box contains three tabs:
) in the upper right corner of the UI. The dialog box contains three tabs:
Basic - Use the Basic tab to change your password into the system.
Contact - Use the Contact tab to enter your contact information.
UI Settings - Use the UI Settings tab to set the following:
| Settings | Guidelines |
|---|---|
| Home | Select the tab which opens when you log in to the FortiSIEM UI. |
| Incident Home | Select the Overview, List (by Time, by Device, by Incident), Risk, Explorer, or MITRE ATT&CK ICS or IT (Rule Coverage, Incident Coverage, Incident Explorer) display for the INCIDENTS tab. |
| Dashboard Home | Select the Dashboard to open by default under the DASHBOARD tab from this drop-down list. |
| Dashboard Settings | Select the type of dashboards to be visible/hidden using the left/right arrows. The up/down arrows can be used to sort the Dashboards. |
| Language | Specify which language will be used for the UI display. Many UI items have been translated into the languages in the drop-down list, including buttons, labels, top-level headings, and breadcrumbs. Items that are data-driven are not translated. |
| Theme | Select Dark or Light theme for FortiSIEM UI. Save and refresh the browser to view the change. |
| Date Format |
Select one of the following formats for displaying date and time information.
|
When done configuring, click Save.
Note: All of the above settings will take effect when you log in again or when you refresh the browser in the same login session.
Administrator UI Settings
Click ADMIN > Settings > System > UI to access the administrator UI settings.
|
|
FortiSIEM only accepts SVG format for logos. All other image formats must be converted to SVG format first. The image resolution is restricted to 160 x 40. The following site can be used to help convert PNG/JPG/GIF into SVG: https://onlineconvertfree.com/convert/svg/ |
|
Settings |
Guidelines |
|---|---|
| UI Logo | Click the edit icon to enter the path to the image file for the logo that will be used in the UI. |
| Report Logo | Click the edit icon to enter the path to the image file for the logo that will be used in reports. |
| Google Maps API Key | Click the edit icon to enter the API key to access Google Maps. |
| Lockout Users | In the number of days field, enter the number of inactive days required before a user is automatically locked out. |
| Login Banner | Administrators can choose a login banner to display to users after login. Click the Enabled checkbox to display a login banner. In the field below Login Banner, enter the text that you want to appear. Some simple BBCode tags are allowed in this message input: “b” - bold “i” - italic “u” - underline “url” - url HTML tags are not allowed. Nested tags are not allowed. When done, click Save. In addition to the banner, the user will see the following:
|
Email Settings
The system can be configured to send email as an incident notification action or send scheduled reports. Use these fields to specify outbound email server settings.
Complete these steps to customize email settings:
- Go to ADMIN > Settings > System > Email tab.
- Enter the following information under Email Settings:
Settings Guidelines Email Gateway Server [Required] Holds the gateway server used for email. Server Port Port used by the gateway server. Secure Connection (TLS) Protocol used by the gateway server. This can be Exchange or SMTP. Server Account ID [Required] The account name for the gateway. Default Email Sender Default email address of the sender. Authentication If Basic is selected, the following field must be configured.
Account password - Enter the password for the account.
If OAuth is selected, the following fields must be configured.
OAuth Provider - Select the OAuth Provider from the drop-down list.
Client ID - Enter the Client ID for OAuth.
Client Secret - Enter the Client Secret associated with the Client ID.
After OAuth configuration, click Re-authenticate to confirm authentication settings.
Enable S/MIME Add a check mark to enable Secure/Multipurpose Internet Mail Extensions (S/MIME) to encrypt your emails. To add a S/MIME certificate, go to CMDB > Users > Ungrouped, create or edit a user, select Contact Info, ensure the Email field is filled out, and upload the certificate in the Certificate field. Send Without Key If this option is selected, then email is sent to a user, even if no S/MIME certificate is defined for that user. The email is encrypted with a default certificate and the user cannot read this email. If this option is unselected, then email is not sent to the user without a S/MIME certificate. Therefore, to use the S/MIME option, certificates must be defined for all users configured to receive email. - Click Test Email button to test the new email settings.
- Click Save.
Customizing the Incident Email Template
Use the following procedure to customize the incident email template.
- Click New under the section Incident Email Template.
- Enter the Name of the template.
- Select the Organization from the list.
- Enter the Email Subject. You can also choose the incident attribute variables from Insert Content drop-down as part of Email Subject.
- Enter the Email Body by selecting the attribute variables from Insert Content drop-down into your template, rather than typing.
If required, enable Support HTML for HTML content support.
Incident Attribute
Description
Affected Business Service
Comma separated list of all business services to which Incident Source, Incident Target or Reporting Device belongs
Device Annotation
Annotation for the device in Incident Target – set in CMDB
Device Description
Description for the device in Incident Target – set in CMDB
Device Location
Location for the device in Incident Target – set in CMDB
First Seen Time
First time the incident occurred
Host Name
Host Name from Incident Target. If not found then gathered from Incident Source
Identity
Identity and Location for Incident Source
Incident Category
Security, Performance, Availability or Change
Incident Cleared Reason
Value set by user when clearing a rule
Incident Comments Comments inputted by user for Incident Incident Count
Number of times the same incident has happened with the same group by parameters
Incident Detail
Any group by attribute in an Incident other than those in Incident Source and Incident Target
Incident ID
Incident ID – assigned by FortiSIEM and is unique – this attribute has an URL which takes user to this incident after login
Incident ID Without Link
Incident ID – assigned by FortiSIEM and is unique – this attribute does not have an URL
Incident Resolution
None, True Positive, False Positive
Incident Severity
A number from 0-10
Incident Severity Category
HIGH (9-10), MEDIUM (5-8) and LOW (1-4)
Incident Source
Source IP, Source Name in an Incident
Incident Sub Category
Specific for each category – as set in the Rule definition
Incident Tactics MITRE ATT&CK® tactic(s) involved with incident Incident Tag Rule tag linked to Incident Incident Target
Destination IP, Destination Host Name, Host IP, Host Name, User in an Incident
Incident Technique MITRE ATT&CK® technique involved with incident Incident Time Time incident occurred Incident Title A system default title or a user-defined title for an incident. Last Seen Time
Last time the incident occurred
Notify Policy ID
Automation Policy ID that triggered this email notification
Organization
Organization to which this Incident belongs.
Raw Events
Triggering events in raw format as sent by the device (up to 10)
Rule Description
Rule Description
Rule Name
Rule Name
Rule Remediation Note
Remediation note defined for each rule
Status
Incident Status – Active (0), Auto Cleared (1), Manually Cleared (2), System Cleared (3)
Triggering Attributes
List of attributes that trigger a rule – found in Rule > Sub pattern > Aggregate
- Click Preview to preview the email template.
- Click Save to apply the changes.
To set an email template as default, select the template in the list, and then click Set as Default. When you are creating an automation policy and must select an email template, if you leave the option blank, the default template will be used. For Service Provider deployments, to select a template as default for an Organization, first select the Organization, then set the default email template for that organization.
Example Registering FortiSIEM with Azure via OAUTH
Here is an example of registering FortiSIEM to use Azure email server via OAUTH.
- Login to Microsoft 365.
- Go to App registrations.
- Click + New registration.

- In the Name field, enter a name, such as "FortiSIEM", and choose an account type.
- Under Owned applications, select your FortiSIEM application.

- On the App registration page for your app, make note of the Application (client) ID for your FortiSIEM configuration. Then, at Client credentials, click Add a certificate or secret.

- Under Client secrets, click + New client secret.

- Copy the value from the Value column. This is your Client Secret for authentication.

- At Redirect URIs, click Add a Redirect URI.
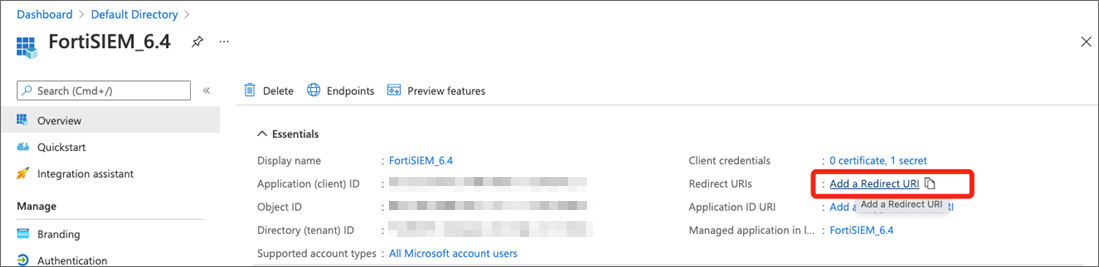
- Under Platform configurations, click + Add a platform.
- Click Web.
- In the Redirect URIs section, enter/paste the URI, which is your FortiSIEM Supervisor IP or host name.

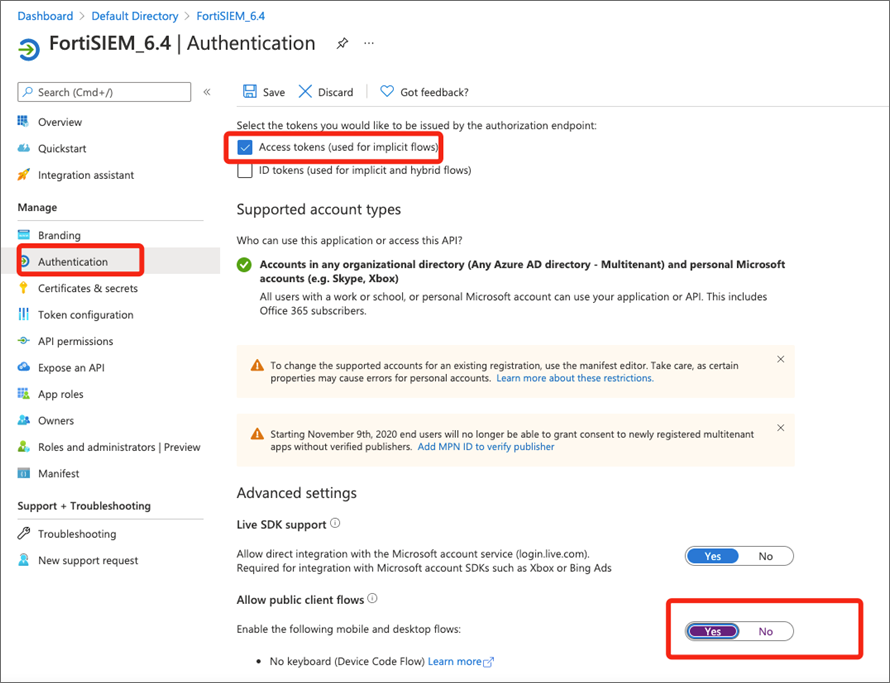
- In the left pane, navigate to Manage > Authentication.
- Configure the two following Authentication settings:
- Access tokens (used for implicit flows) checkbox must be checked.
- Under Advanced settings, Allow public client flows must be set to Yes.
- Navigate to Manage > API permissions.
- Under Configured permissions, click + Add a permission.
- From the Request API permissions pane, select the Microsoft APIs tab, and click Microsoft Graph.

- Under What type of permissions does your application require? select Application permissions.
- In the Select permissions search field, enter "mail".
- From the Permission column, expand Mail, and configure Mail.Send (Send mail as any user) so Admin consent required is set to Yes.

- Now, under Microsoft Graph > What type of permissions does your application require? select Delegated permissions.
- Under the Permission column, expand OpenId permissions.
- Click the offline_access checkbox so that offline_access is checked.

- Under Configured permissions, click Grant admin consent for Default Directory.

Check the Status column. The following permissions should be granted.
- Mail.Send
- offline_access
- User.Read

On FortiSIEM, take the following steps:
- Navigate to Admin > Settings > System > Email.
- In the Email Gateway Server field, enter the IP address/host name of your email gateway server.
- In the Server Port field, enter the Server Port number.
- In the Server Account ID field, enter the server account ID.
- For Authentication, select OAuth.
- In the OAuth drop-down list, select Microsoft.
- In the Client ID field, enter/paste the Application (Client) ID of the App from Step 6 in Example Registering FortiSIEM with Azure via OAUTH.
- In the Client Secret field, enter/paste the value from Step 8 in Example Registering FortiSIEM with Azure via OAUTH.
- Click Re-authenticate, Test Email then Save.
Your OAuth settings should look similar to the following in FortiSIEM.

If you still receive a “SendAs” in “SendAsDeniedException” error, you may need to go to your Office365 account and configure “Send email on behalf of another user”. This error occurs if the email address used for authentication is different than the FROM email address. The solution is to update your Office365 account settings to allow for sending on behalf of the FROM email address.
Image Server Settings
This section allows you to set up the Supervisor as an Image Server for upgrading Collectors and Agents. This mechanism provides an easy way to upgrade a large number of Collectors and Agents from one place.
Upgrading Collectors
Step 1: Download the Correct Collector Image from the Fortinet Support Site into your Workstation
As an example, Collector 6.4.0 image file name is FSM_Upgrade_All_6.4.0_build1412.zip and matches the hash in the support site to the locally computed hash. This ensures that the file has not been corrupted in transit.
Step 2: Upload the Image to the Supervisor Node
Note: In this step, you will upload the image to the Supervisor, which will then internally create a URL for the Collectors to download the image. It is critical to set the host name in the URL correctly so that a Collector can resolve the host name. Otherwise, the image download in Step 3 will fail.
There are two solutions.
| Solution 1 |
By default, the Supervisor's host name in ADMIN > License > Nodes is used to create the URL. If the host name is a Fully Qualified domain name and is resolvable by the Collectors, then there is nothing to do. For example, a host name like /etc/hosts file in the following format: <ip> <host name>For example: 10.0.1.21 2-52-35-20-68.us-west-2.compute |
| Solution 2 |
If there is a load balancer in front of the Supervisors, or you want to override the Supervisor host name in the default image download URL, then you can enter the appropriate host name or IP after going to ADMIN > Settings > Systems > Image Server > Custom Update and then clicking Save. If you have entered a host name here, make sure that it is a Fully Qualified domain name and is resolvable by Collectors. Do this step first before proceeding to the remaining of Step 2. Note that if you create an entry in Custom Update, then it applies to ALL Collectors and Agents. This means that every Collector and Agent will the get the URL with the Custom Update entry. |
- Go to ADMIN > Settings > Systems > Image Server.
- Under Collector, in the Version field, enter the version you downloaded in Step 1. The format is #.#.#. Example: 6.4.0.
- Under Collector, click Select File and select the Collector upgrade image you downloaded in Step 1.
- Under Collector, click Upload File to upload the Collector upgrade image to the Supervisor. This may take a while depending on the network connection between your workstation and Supervisor node. FortiSIEM will validate the image hash and upload the image to Supervisor if the hash matches.
- Run the following SQL and make sure ImageSetup task is completed.
# psql phoenixdb phoenix -c "select type, progress from ph_task where type = 'ImageSetup'" type | progress ------------+---------- ImageSetup | 100 ImageSetup | 100 ImageSetup | 100 (3 rows)
Step 3: Download the Image to the Collector
- Go to ADMIN > Health > Collector Health.
- From the Columns drop-down list, ensure Download Status is selected. If not, select it so the Download Status column is displayed.
- Select the Collector(s) you wish to download the image to.
Note: Starting with release 6.4.0, you can choose multiple Collectors for downloading images. - From the Action drop-down list, select Download Image.
- Check that the Download Status column shows finished to confirm that the download has been completed for the selected Collectors.
Step 4: Upgrade the Collector
- Go to ADMIN > Health > Collector Health.
- From the Columns drop-down list, ensure Version is selected. If not, select it so the Version column is displayed.
- Select the Collector(s) you wish to upgrade.
Note: Starting with release 6.4.0, you can choose multiple Collectors for installing images. - From the Action drop-down list, select Install Image.
- Check that the Version columns shows the correct version number, in this example 6.4.0, to confirm that the Collector(s) have upgraded successfully.
Upgrading Linux Agents
Step 1: Download the Correct Linux Agent Image from the Fortinet Support Site into your Workstation.
As an example, a Linux Agents 6.4.0 image file name is fortisiem-linux-agent-installer-6.4.0.1412.sh and matches the hash in the support site to the locally computed hash. This ensures that the file has not been corrupted in transit.
Step 2: Upload the Image to the Supervisor Node
Note: In this step, you will upload the image to the Supervisor, which will then internally create a URL for the Agents to download the image. It is critical to set the host name in the URL correctly, so that an Agent can resolve the host name. Otherwise, the image download in Step 3 will fail.
There are two solutions.
| Solution 1 |
By default, the Supervisor host name in ADMIN > License > Nodes is used to create the URL. If the host name is a Fully Qualified domain name and is resolvable by the Agents, then there is nothing to do. For example, a host name like |
| Solution 2 |
If there is a load balancer in front of the Supervisors, or you want to override the Supervisor host name in the default image download URL, then you can enter the appropriate host name or IP after navigating to ADMIN > Settings > Systems > Image Server > Custom Update, and then clicking Save. If you have entered a host name here, make sure that it is a Fully Qualified domain name and is resolvable by Agent. Do this step first before proceeding to the remaining of Step 2. Note that if you create an entry in Custom Update, then it applies to ALL Collectors and Agents. This means that every Collector and Agent will the get the URL with the Custom Update entry. |
- Go to ADMIN > Settings > Systems > Image Server.
- Under Linux Agent, in the Version field, enter the version you downloaded in Step 1. The format is #.#.#. Example: 6.4.0.
- Under Linux Agent, click Select File and select the Linux Agent upgrade image you downloaded in Step 1.
- Under Linux Agent, click Upload File to upload the Linux Agent upgrade image to the Supervisor. This may take a while depending on the network connection between your workstation and Supervisor node. FortiSIEM will validate the image hash and upload the image to Supervisor if the hash matches.
Step 3: Download the Image to the Linux Agent
- Go to ADMIN > Health > Agent Health.
- From the Columns drop-down list, ensure Upgrade Status is selected. If not, select it so the Upgrade Status column is displayed.
- Select the Linux Agent(s) you wish to download the image to.
Note: Starting with release 6.4.0, you can choose multiple Linux Agents for downloading images. - From the Action drop-down list, select Download Image.
- Check that the Upgrade Status column shows Download Succeeded to confirm that the download has been completed for the selected Linux Agents.
Step 4: Upgrade the Linux Agents
- Go to ADMIN > Health > Agent Health.
- From the Columns drop-down list, ensure Version is selected. If not, select it so the Version column is displayed.
- Select the Linux Agent(s) you wish to upgrade.
Note: Starting with release 6.4.0, you can choose multiple Linux Agents for installing images. - From the Action drop-down list, select Install Image.
- Check that the Upgrade Status column shows Upgrade Succeeded to confirm that the Linux Agent(s) have upgraded successfully. Check that the Version column shows the correct version number, in this example 6.4.0, to confirm that the Linux Agent(s) have upgraded to the correct version.
Upgrading Windows Agents
Step 1: Download the Correct Windows Agent Images from the Fortinet Support Site into your Workstation.
- Download the image file into your desktop. It is a .zip file, e.g.
FSMLogAgent-v4.2.1-build0225.zip. - Compute the MD5 checksum and make sure that locally, the computed checksum matches the checksum in the Support Site. This ensures that the file is not corrupted in transit.
- Unzip the file. You will see that there are two files –
AutoUpdate.exeandFSMLogAgent.exe. You will need to upload these files in Step 2.3 and Step 2.4 below.
Step 2: Upload the Image to the Supervisor Node
Note: In this step, you will upload the image to the Supervisor, which will then internally create a URL for the Agents to download the image. It is critical to set the host name in the URL correctly, so that an Agent can resolve the host name. Otherwise, the image download in Step 3 will fail.
There are two solutions.
| Solution 1 |
By default, the Supervisor host name in ADMIN > License > Nodes is used to create the URL. If the host name is a Fully Qualified domain name and is resolvable by the Agents, then there is nothing to do. For example, a host name like |
| Solution 2 |
If there is a load balancer in front of the Supervisors or you want to override the Supervisor host name in the default image download URL, then you can enter the appropriate host name or IP after going to ADMIN > Settings > Systems > Image Server > Custom Update, then clicking Save. If you have entered a host name here, make sure that it is a Fully Qualified domain name and is resolvable by Agent. Do this step first before proceeding to the remaining of Step 2. Note that if you create an entry in Custom Update, then it applies to ALL Collectors and Agents. This means that every Collector and Agent will the get the URL with the Custom Update entry. |
- Go to ADMIN > Settings > Systems > Image Server.
- Under Windows Agent, in the Version field, enter the version you downloaded in Step 1. The format is #.#.#. Example: 4.2.1.
Note: For Windows Agent, two files are required, the FSMLogAgent executable (FSMLogAgent.exe) and an AutoUpdate executable (AutoUpdate.exe, or AutoUpdate32.exe). - Under Windows Agent, click Select File and select one of the two Windows Agent upgrade image you downloaded in Step 1.
- Under Windows Agent, click Select File and select the second Windows Agent upgrade image you downloaded in Step 1.
- Under Windows Agent, click Upload File to upload the Windows Agent upgrade images to the Supervisor. This may take a while depending on the network connection between your workstation and Supervisor node. FortiSIEM will validate the image hash and upload the image to Supervisor if the hash matches.
Step 3: Download the Images to the Windows Agent
- Go to ADMIN > Health > Agent Health.
- From the Columns drop-down list, ensure Upgrade Status is selected. If not, select it so the Upgrade Status column is displayed.
- Select the Windows Agent(s) you wish to download the image to.
Note: Starting with release 6.4.0, you can choose multiple Windows Agents for downloading images. - From the Action drop-down list, select Download Image.
- Check that the Upgrade Status column shows Download Succeeded to confirm that the download has been completed for the selected Windows Agents.
Step 4: Upgrade the Windows Agents
- Go to ADMIN > Health > Agent Health.
- From the Columns drop-down list, ensure Version is selected. If not, select it so the Version column is displayed.
- Select the Windows Agent(s) you wish to upgrade.
Note: Starting with release 6.4.0, you can choose multiple Windows Agents for installing images. - From the Action drop-down list, select Install Image.
- Check that the Upgrade Status column shows Upgrade Succeeded to confirm that the Windows Agent(s) have upgraded successfully. Check that the Version column shows the correct version number, in this example 4.2.1, to confirm that the Windows Agent(s) have upgraded to the correct version.
Custom Update
To allow Load Balancers in front of the Supervisor to work, Fortinet allows you to perform a custom upgrade through a configured IP/Host Name.
Note: The current upgrade URL for Collectors and Agents were auto generated by the App Server based on the Supervisor host name.
To perform a custom update, take the following steps.
- Navigate to ADMIN > Settings > System > Image Server.
- Under Custom Update, in the IP/Host Name field, enter the IP address or host name to use as the public download URL. Note: Make sure the Collector or Agent can either ping the new IP address or host name.
- Click Save.
- Upload the secure image file. (Following the steps from the appropriate instructions: Upgrading Collectors, Upgrading Linux Agents, Upgrading Windows Agents.)
Note: If you re-update to a new URL/host name, the secure image must be re-uploaded, otherwise downloading the image will fail because the previously uploaded image retains the old IP/Hostname. - Download Image file. (Following the steps from the appropriate instructions: Upgrading Collectors, Upgrading Linux Agents, Upgrading Windows Agents.)
- Install Image. (Following the steps from the appropriate instructions: Upgrading Collectors, Upgrading Linux Agents, Upgrading Windows Agents.)
Cluster Config
A Load Balancer or Supervisors, and Collectors can be added into a cluster configuration here. For more information on Supervisor Cluster, see Configuring and Maintaining Active-Active Supervisor Cluster.
- Supervisor / Load Balancer Configuration
- Event Upload Workers Configuration
- Collector High Availability Configuration
Supervisor / Load Balancer Configuration
For Supervisors or Load Balancer configuration, take the following steps:
- Navigate to ADMIN > Settings > System > Cluster Config.
- Under Supervisors, in the Address field, enter the Supervisor or Load Balancer Host Name or IP address.
- (Optional) Click + to add a Supervisor, or - to remove one, and repeat step 2 to configure any additional Supervisor or Load Balancer.
- Click Save when done.
Event Upload Workers Configuration
Collectors upload events and configurations to Worker nodes.
There are three cases:
- Explicit list of Worker IP addresses or host names - Collector forwards to this list in a round robin manner.
- If you are not using Workers and using only a Supervisor and Collector(s) – specify the Supervisor IP addresses or host name. The Collectors will upload directly to the Supervisor node.
- Host name of a load balancer - Collector forwards this to the load balancer which must be configured to distribute events to the workers.
Any Hostnames specified in the Worker Upload must be resolvable by the Collector and similarly, any specified IP addresses must have connectivity from the Collector.
Complete these steps to configure Worker upload settings:
- Navigate to ADMIN > Settings > System > Cluster Config.
- Under Event Upload Workers, in the Address field, enter the Worker Host Name or IP address.
- (Optional) Click + to add a Worker, or - to remove one, and repeat step 2 to configure any additional Workers.
- Click Save when done.
Note: Virtual IP should be done here, not through Host To Template Associations under Admin > Setup > Windows Agent or Admin > Setup > Linux Agent.
Lookup Settings
Lookup setting can be used to find any IP or domain by providing the link.
Complete these steps for lookup:
- Go to ADMIN > Settings > System > Lookup tab.
- Enter the Name.
- Select the Client Type to IP or Domain.
- Enter the Link for look-up.
You must enter "
<ip>” in the link. FortiSIEM will replace "<ip>” with a proper IP during lookup.For example, to lookup the following URL:
http://whois.domaintools.com/8.8.8.8Enter the following link in FortiSIEM:
http://whois.domaintools.com/<ip> - Click Save.
Kafka Settings
FortiSIEM events found in system event database can be exported to an external system via Kafka message bus.
FortiSIEM supports both forwarding events to an external system via Kafka message bus as a 'Producer' and receiving events from a third-party system to FortiSIEM via Kafka message bus as a 'Consumer'.
As a Producer:
- Make sure you have set up a Kafka Cloud (here) with a specific Topic for FortiSIEM events.
- Make sure you have identified a set of Kafka brokers that FortiSIEM is going to send events to.
- Make sure you have configured Kafka receivers which can parse FortiSIEM events and store in a database. An example would be Logstash receiver (see here) that can store in an Elastic Search database.
- Configure event forwarding in order for FortiSIEM to send events to an external Kafka consumer.
- Supported Kafka version: 0.8
As a Consumer:
- Make sure you have set up a Kafka Cloud (here) with a specific Topic, Consumer Group and a Consumer for sending third party events to FortiSIEM.
- Make sure you have identified a set of Kafka brokers that FortiSIEM will receive events from.
- Supported Kafka version: 0.8
Setting up Consumer
Complete these steps to configure Kafka for authentication.
Note: Tested with
- kafka_2.13-3.4.0.tgz
- Download the source code tarball.
https://archive.apache.org/dist/kafka/3.4.0/kafka_2.13-3.4.0.tgz - Generate SSL key
# sudo mkdir /opt/kafka # chown -R admin.admin /opt/kafka # cd /opt/kafka # wget https://github.com/confluentinc/librdkafka/raw/master/tests/gen-ssl-certs.sh # bash gen-ssl-certs.sh ca ca-cert CA_CN # bash gen-ssl-certs.sh -k server ca-cert broker_ $(hostname) # bash gen-ssl-certs.sh -k client ca-cert client_ client # bash gen-ssl-certs.sh client ca-cert client_ client
- Uncompress the files and enter the "config" folder.
- Modify the configuration files by appending the following to the end of the files:
Note: In the following example, the following is used:
username=alicepassword=alice-secretSSL password=abcdefghRemember to replace
<Kafka Server IP Address>with your actual Kafka Server IP address.# zookeeper.properties authProvider.1=org.apache.zookeeper.server.auth.SASLAuthenticationProvider requireClientAuthScheme=sasl # zookeeper_jaas.conf Server { org.apache.zookeeper.server.auth.DigestLoginModule required user_super="zookeeper" user_alice="alice-secret"; }; # server.properties listeners=SASL_SSL://<Kafka Server IP Address>:9092 advertised.listeners=SASL_SSL://<Kafka Server IP Address>:9092 sasl.enabled.mechanisms=SCRAM-SHA-512 sasl.mechanism.inter.broker.protocol=SCRAM-SHA-512 security.inter.broker.protocol=SASL_SSL ssl.endpoint.identification.algorithm= authorizer.class.name=kafka.security.authorizer.AclAuthorizer allow.everyone.if.no.acl.found=true auto.create.topics.enable=true ssl.client.auth=none ssl.protocol = TLS ssl.enabled.protocols=TLSv1.3,TLSv1.2 ssl.keystore.type=JKS ssl.truststore.type=JKS ssl.secure.random.implementation=SHA1PRNG ssl.keystore.location=/opt/kafka/broker_server.keystore.jks ssl.keystore.password=abcdefgh ssl.key.password=abcdefgh ssl.truststore.location=/opt/kafka/broker_server.truststore.jks ssl.truststore.password=abcdefgh # kafka_server_jaas.conf KafkaServer { org.apache.kafka.common.security.scram.ScramLoginModule required username="alice" password="alice-secret" user_alice="alice-secret"; }; Client { org.apache.zookeeper.server.auth.DigestLoginModule required username="alice" password="alice-secret"; }; # consumer.properties security.protocol=SASL_SSL sasl.mechanism=SCRAM-SHA-512 sasl.jaas.config=org.apache.kafka.common.security.scram.ScramLoginModule required username="alice" password="alice-secret"; ssl.truststore.location=/opt/kafka/client_client.truststore.jks ssl.truststore.password=abcdefgh ssl.endpoint.identification.algorithm= # producer.properties security.protocol=SASL_SSL sasl.mechanism=SCRAM-SHA-512 sasl.jaas.config=org.apache.kafka.common.security.scram.ScramLoginModule required username="alice" password="alice-secret"; ssl.truststore.location=/opt/kafka/client_client.truststore.jks ssl.truststore.password=abcdefgh ssl.endpoint.identification.algorithm= # kafka_client_jaas.conf KafkaClient { org.apache.kafka.common.security.scram.ScramLoginModule required username="alice" password="alice-secret" user_alice="alice-secret"; }; Client { org.apache.zookeeper.server.auth.DigestLoginModule required username="alice" password="alice-secret"; }; # topic.conf sasl.jaas.config=org.apache.kafka.common.security.scram.ScramLoginModule required username="alice" password="alice-secret"; security.protocol=SASL_SSL sasl.mechanism=SCRAM-SHA-512 ssl.truststore.location=/opt/kafka/client_client.truststore.jks ssl.truststore.password=abcdefgh ssl.endpoint.identification.algorithm=
# zookeeper.properties authProvider.1=org.apache.zookeeper.server.auth.SASLAuthenticationProvider requireClientAuthScheme=sasl jaasLoginRenew=3600000 - Start zookeeper.
cd .. export KAFKA_OPTS="-Djava.security.auth.login.config=$(\pwd)/config/zookeeper_jaas.conf" bin/zookeeper-server-start.sh config/zookeeper.properties
(In another shell window)
bin/kafka-configs.sh --zookeeper localhost:2181 --alter --add-config 'SCRAM-SHA-512=[password=alice-secret]' --entity-type users --entity-name alice - Start the server (In another shell window)
export KAFKA_OPTS="-Djava.security.auth.login.config=$(\pwd)/config/kafka_server_jaas.conf" bin/kafka-server-start.sh config/server.properties
- Create topic (name=test1) (In another shell window)
bin/kafka-topics.sh --create --topic test1 --bootstrap-server <Kafka Server IP Address>:9092 --partitions 3 --replication-factor 1 --command-config config/topic.conf
- Start consumer.
export KAFKA_OPTS="-Djava.security.auth.login.config=$(\pwd)/config/kafka_client_jaas.conf" bin/kafka-console-consumer.sh --topic test1 --bootstrap-server=<Kafka Server IP Address>:9092 --consumer.config=config/consumer.properties
At this point, when FortiSIEM forwards events to this client, contents can be seen in the consumer window.
-
(Optional) Start producer.
export KAFKA_OPTS="-Djava.security.auth.login.config=$(\pwd)/config/kafka_client_jaas.conf" bin/kafka-console-producer.sh --topic test1 --broker-list <Kafka Server IP Address>:9092 --producer.config config/producer.properties
On FortiSIEM, take the following actions.
- Copy the following files to
/etc/pki/kafkato your FortiSIEM Supervisor and to every FortiSIEM Collector.- ca-cert
- client_client.pem
- client_client.key
- On the FortiSIEM Supervisor and Collector, make sure to set up the value properly in
/opt/phoenix/config/phoenix_config.txtfor the path of the above files, so FortiSIEM can query the Simple Authentication and Security Layer (SASL) with correct results for the Supervisor and each Collector.grep sasl /opt/phoenix/config/phoenix_config.txtsasl_ssl_ca_cert=/etc/pki/kafka/ca-certsasl_ssl_cert_file=/etc/pki/kafka/client_client.pemsasl_ssl_key_file=/etc/pki/kafka/client_client.keysasl_ssl_password=abcdefghsasl_ssl_verify=false
Setting Up FortiSIEM
Complete these steps for configuring Kafka settings in FortiSIEM:
- Go to ADMIN > Settings > System > Kafka tab.
- Click New.
- Enter the Name and Topic.
- Select or search the Organization from the drop-down.
- Add Brokers by clicking + icon.
- Enter IP address or Host name of the broker.
- Enter Broker port (default 9092).
- Click Save.
- Select the Client Type to Producer or Consumer.
- If the Consumer is selected in step 7, enter the Consumer Name and Group Name fields.
- Enable Authentication if you want to apply Kafka authentication by adding a checkmark to the Authentication checkbox, then take the following steps:
- Select your Protocol: SASL_PLAINTEXT, SASL_SSL.
- Select your authentication mechanism: PLAIN, SCRAM-SHA-256, or SCRAM-SHA-512.
- In the User Name field, enter the user name to authenticate for the Kafka servers.
- In the Password field, enter the password associated with the user name to authenticate for the Kafka servers.
- In the Confirm Password field, re-enter the password associated with the user name to authenticate for the Kafka servers.
- Click Save.
Dashboard Slideshow Settings
Dashboard Slideshow settings are used to select a set of dashboards and display them in a slideshow mode on big monitors to cover the entire display. This is useful for Network and Security Operation Centers.
Complete these steps to create a Dashboard Slideshow:
- Go to ADMIN > Settings > System > Dashboard Slideshow tab.
- Click New to create a slideshow.
- Enter a Name for the slideshow.
- Select the Interval for switching between dashboards.
- Select the Dashboards from the list and move to the Selected list.
These dashboards will be displayed in a slideshow mode. - Click Save.
For all the above System settings, use the Edit button to modify or Delete button to remove any setting from the list.
Dashboard Ownership
Dashboard Ownership settings are used to transfer editing rights from the current owner of a shared dashboard to another person. It requires that the owner to whom the rights are being transferred to, to have the same exact role permissions as the current owner. This feature can be useful if the current owner is no longer available, and another person is required to handle the shared dashboard of that individual.
Complete these steps to transfer Dashboard Ownership:
- Go to ADMIN > Settings > System > Dashboard Ownership tab.
- Select the Dashboard you wish to transfer ownership of.
- Click Transfer.
- In the Transfer Ownership window, select the new owner from the To: drop-down list.
- Click Save.
You can verify the transfer by looking at the user in the User column.
PAYG Report
If applicable, you can generate a daily or monthly Pay as you Go (PAYG) report.
Complete these steps to generate a daily or monthly PAYG report:
- Go to ADMIN > Settings > System > PAYG Report tab.
- In the Partner ID field, enter the Partner ID.
- Take the following steps to enable Daily Reports.
- Check the Daily Report checkbox.
- In the Email field, enter the email address for a person to whom a daily report should be sent.
- Click + to add another Email field entry.
- Repeat steps b and c to input additional entries.
- Take the following steps to enable Monthly Reports.
- Check the Monthly Report checkbox.
- In the Email field, enter the email address for a person to whom a monthly report should be sent.
- Click + to add another Email field entry.
- Repeat steps b and c to input additional entries.
- When done, click Test to verify your email address distribution.
- Click Save.
- To enable Month Reports, click the Monthly Report checkbox.
- In the Transfer Ownership window, select the new owner from the To: drop-down list.
- Click Save to finish.
Trusted Hosts
You can restrict GUI Login by defining a set of IP addresses here. If the field is empty, then GUI login from any IP addresses are allowed. However once defined, new logins are disallowed from IP addresses outside of the defined range. Existing logins are not affected. To force a logout, click on![]() in the GUI, select a user, and click Log Out or Log Out and Lock Out.
in the GUI, select a user, and click Log Out or Log Out and Lock Out.
Note: If you have defined Trusted Hosts, then remember to include the Collectors and the Agents, else they will not be able to register.
Take the following steps to configure:
- Navigate to ADMIN > Settings > System > Trusted Hosts.
- In the Trusted Hosts field, enter a single IP address or CIDR range, for example 172.0.20.1/24.
- Click + to add another Trusted Hosts field to configure if needed.
Note: Click - to remove an existing Trusted Hosts field. - Click Save when done.
