Configuring Windows Agent
Starting with version 3.0, Windows Agents can be configured and managed from the FortiSIEM Supervisor node. Windows Agent Manager is not required.
Before proceeding, follow the instructions in the Windows Agent Installation Guide to complete these steps:
- Install the Windows Agent using the correct installation file.
- Make sure the Agent appears in the CMDB page of the FortiSIEM GUI, using the host name defined in the installation file.
- Configure the Windows Server to receive the types logs of interest (see Configuring Windows Servers for FortiSIEM Agents in the Windows Agent Installation Guide).
To receive logs from Windows Agent, you must complete the following steps:
Once these steps are completed, the Supervisor node will distribute monitoring policies to the Agents and you will be able to see events in FortiSIEM.
This section also covers these topics:
- Viewing Agent Status
- Enabling or Disabling an Agent
- Viewing Files in FortiSIEM
- Verifying Events in FortiSIEM
- Service Level Protection Properties
- Auto Restart Service Behavior
- Configuring Debug Trace Logging without Agent Service Restart
- Configuring the Agent Database Size
- Sample Windows Agent Logs
- Agent Troubleshooting Notes
Define the Windows Agent Monitor Templates
A Windows Monitoring Template consists of:
- Log Settings: Windows Event Logs and Log Files
- Change Settings: File Integrity Monitoring, Registry Changes, Installed Software Changes, Removable media
- Script Settings: WMI Classes and PowerShell Scripts
Complete these steps to add a Windows Agent Monitor Template:
- Go to ADMIN > Setup > Windows Agent tab.
- Click New under the section Windows Agent Monitor Templates.
- In the Windows Agent Monitor Template dialog box, enter the information under each tab with reference to the tables below.
- Configure the Generic settings with reference to the table below:
Generic settings Guidelines Name Enter the name of the Windows Agent Monitor Template. This name is used as a reference in Template associations.
Note: The template name cannot contain a space (" ") character.Description Enter a description of the Windows Agent Monitor Template. Configure the Monitor settings for Windows Agent using the table below. When done, click Save.
Monitor settings Guidelines Discover To configure Discover settings:
Click the Discover checkbox to enable Windows Agent discovery.
In the Hour(s) field, enter the frequency (in number of hours) that discovery will be done.
Monitor To configure Monitor settings: Click the appropriate Monitor checkboxes to enable specific monitoring performance of Windows Agents.
- Uptime - Select to monitor uptime of Windows Agent.
- CPU - Select to monitor CPU utilization.
- Memory - Select to monitor memory utilization.
- Disk - Select to monitor disk utilization.
- Network - Select to monitor network utilization.
- Running Applications - Select to monitoring running applications.
- Configure the Event settings with reference to the table below. Make sure you have completed these steps
from the Windows Agent Installation Guide:
- To enable DNS logging, follow the steps in Configuring Windows DNS.
- To enable DHCP logging, follow the steps in Configuring Windows DHCP.
- To enable IIS logging, follow the steps in Configuring Windows IIS.
- To get sysmon events, follow the steps in Configuring Windows Sysmon.
- To get print log events, follow the steps in Configuring Print Log.
- To get Windows Terminal Services events, follow the steps in Configuring Windows Terminal Services (RDP - Remote Desktop Protocol)
Event settings Guidelines Event Log To configure Event log settings:
- Select the Type of log from the drop-down:
- Application — Events that are logged by Windows Application. Select All, Exchange Server or SQL Server as Source.
- Security — Log that contains records of login/logout activity or other security-related events specified by the system's audit policy.
- System — Events that are logged by the operating system components.
- DFS — Logs to identify the users who accessed the Distributed File System.
- DNS — DNS Debug logs and Name Resolution Activity logs.
- Hardware Events — Events related to hardware.
- Key Management Service — Events related to creation and control of keys used to encrypt your data.
- Setup — Log files for all actions that occur during installation.
- Windows PowerShell — Logs related to Windows PowerShell.
- Other — Any other log type (specify the name under Event Name setting.)
- Enter the events to be included under Include Event and the ones to exclude under Exclude Event by entering each event ID followed by a semicolon as a separator.
- Select UEBA to turn on UEBA functionality for all hosts running Windows 4.0 or later that are permitted by the UEBA license. For example, if you have 10 UEBA licenses and you applied the template to 100 hosts, system will apply the UEBA license to 10 random hosts. You can turn on/off UEBA on hosts via CMDB.
- Configure the User Log settings with reference to the table below:
User Log settings Guidelines User Log Click New to add the custom log files that must be monitored:
- File—(Required) Enter the full file name.
- Log Prefix—(Required) Any prefix to the identify events from this file for better accessibility.
Example:
The contents of the file
C:\test\test.txtneeds to be brought into FortiSIEM for analysis. The log prefix FSMAGENT was chosen. To configure the Windows Agent template in FortiSIEM, from the User Log tab, you would take the following steps.In the Full file Name field, you would enter "C:\test\test.txt".
In the Log Prefix field, you would enter "FSMAGENT".

Suppose the contents of the file C:\test\test.txt looks like this.
User adds a comment
User adds a comment 1
User adds a comment 2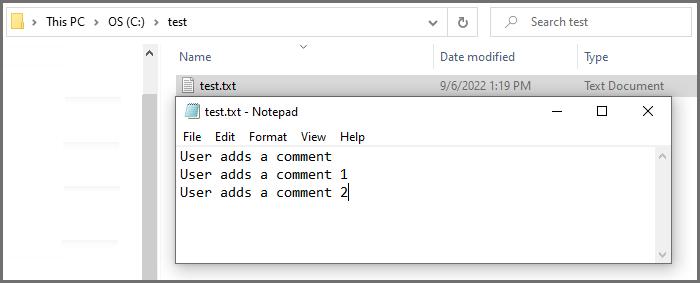
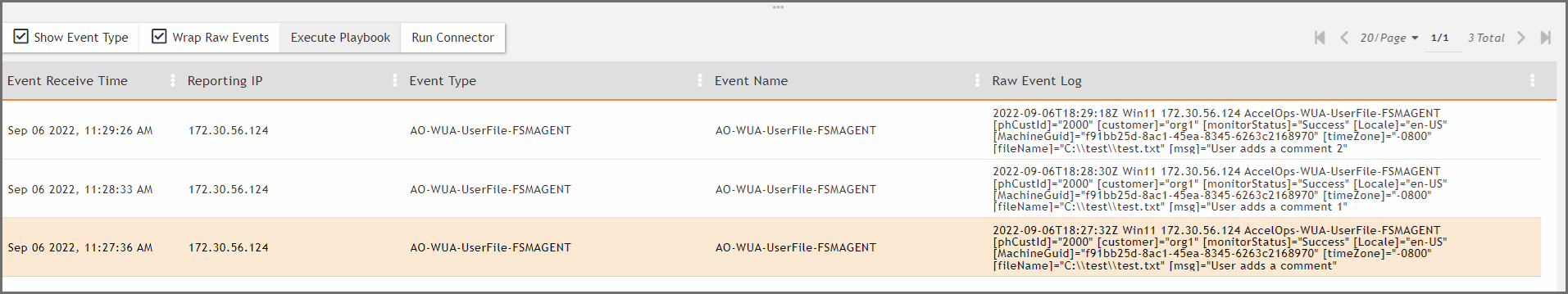
FortiSIEM agent will send each line in a separate event.
2022-09-06T17:16:27Z Win11 172.30.56.124 AccelOps-WUA-UserFile-FSMAGENT [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="f91bb25d-8ac1-45ea-8345-6263c2168970" [timeZone]="-0800" [fileName]="C:\\test\\test.txt" [msg]="User adds a comment" 2022-09-06T17:18:27Z Win11 172.30.56.124 AccelOps-WUA-UserFile-FSMAGENT [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="f91bb25d-8ac1-45ea-8345-6263c2168970" [timeZone]="-0800" [fileName]="C:\\test\\test.txt" [msg]="User adds a comment 1" 2022-09-06T17:20:27Z Win11 172.30.56.124 AccelOps-WUA-UserFile-FSMAGENT [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="f91bb25d-8ac1-45ea-8345-6263c2168970" [timeZone]="-0800" [fileName]="C:\\test\\test.txt" [msg]="User adds a comment 2"
The event type will be AO-WUA-UserFile-FSMAGENT.
-
Configure the FIM settings with reference to the table below. Make sure you have completed these steps
from the Windows Agent Installation Guide:
- To enable logging appropriately, follow the steps in Configure Security Audit Logging Policy.
- To get user meta data in the file auditing logs, follow the steps in Configure File Auditing Policy.
- To enable change events for permission and/or ownership changes to files and/or directories, follow the steps in Configure Audit File System Policy.
FIM settings Guidelines FIM To include the file directory details:
- Click New to add the file directory details:
- File/Directory— Enter the full path of the file directory:
- Include Subfolder(s) — Select if you must include the directory sub-folders.
- Exclude Subfolder(s) — Enter any sub-folders to exclude, if any.
- Include File Type — Enter the file types to include separated by a semi-colon.
- Exclude File Type — Enter the file types to exclude, if any, separated by a semi-colon.
- On Modify:
- Push Files—Select this if you want Windows Agent to push files to FortiSIEM whenever there is a change. File/Directory must specify a specific file and not a directory. Also, the absolute file name, including the path, must be specified. For example
C:\temp\fileToBeMonitored.txt. The files are stored in SVN and are accessible from the Supervisor. These files are displayed in CMDB > Device > File. Send only important files, as this can fill up disk space. - Compare Baseline—Select this if you want to be alerted when the file changes from a baseline. File/Directory must specify a specific file and not a directory. Also, the absolute file name, including the path, must be specified. For example
C:\temp\fileToBeMonitored.txt. This is common for configuration files that rarely change. If you choose this option, you will be asked to provide a copy of the baseline file. Click Choose File and upload the file from your workstation. The Supervisor will compute the MD5 checksum and distribute the checksum to the agents for comparison.
- Push Files—Select this if you want Windows Agent to push files to FortiSIEM whenever there is a change. File/Directory must specify a specific file and not a directory. Also, the absolute file name, including the path, must be specified. For example
- Click Save.
Use the Edit/Delete buttons to modify/remove any file directory information.
- Configure the Change settings with reference to the table below:
Configure the Script settings with reference to the table below:Change settings Guidelines Registry Change Select the required key(s) to monitor:
- HKEY_CLASSES_ROOT—key that contains file extension association information, as well as a programmatic identifier, Class ID, and Interface ID data.
- HKEY_CURRENT_USER—key that contains configuration information for Windows and software specific to the currently logged in user.
- HKEY_LOCAL_MACHINE—hive that contains the majority of the configuration information for the software you have installed, as well as for the Windows Operating System.
- HKEY_USERS—key that contains user-specific configuration information of all currently active users on the computer.
- HKEY_CURRENT_CONFIG—key that acts as a shortcut to a registry key which keeps information about the hardware profile currently used.
Check Every Set the time period to check the Registry Change in Minute(s) or Hour(s). Installed Software Change Select to enable monitoring of any installed software change. Removable Drive Select the removable drive to track:
- USB drive(s)
- CD-DVD drive(s)
Script settings Guidelines WMI Classes To include a WMI Class:
- Click New to add a new WMI Class. Select the Name, WMI Class, and Attributes from the drop-down lists (Use ';' as the separator).
- Set the time period to monitor in Minute(s) or Hour(s) under Check Every setting.
Use the Edit/Delete buttons to modify/remove any WMI Classes.
PowerShell Script To include a PowerShell Script:
Click New to add a new PowerShell Script and enter the Name and Script.
Use the Edit/Delete buttons to modify/remove any PowerShell Script.
Configure the Certificate Monitoring settings with reference to the table below for each Certificate Folder:
Certificate Monitoring settings Guidelines Store Name Select the following to monitor:
Add - Event generated when certificate is added to store.
Delete - Event generated when certificate is removed from store.
Expired (Days) - From the drop-down list, select the number of days to receive notification when a certificate has expired.
Expiry (Days) - From the drop-down list, select the period of days to receive notification prior to when a certificate is about to expire.
Configure the Osquery settings with reference to the table below:
Osquery settings Guidelines osquery From the osquery drop-down list, select the osquery template to include in the Windows Agent Monitor Template.
Click + to add a new entry.
Select the osquery template to use.
Click - to remove an existing entry.
- Configure the Generic settings with reference to the table below:
- Click Save.
Use the Edit button to modify any template or Delete button to remove any Windows Agent Monitor template.
Associate Windows Agents to Templates
After defining the monitoring templates, you must associate hosts to templates. To scale to a large number of hosts, this is done via Policies. A Policy is a mapping from Organization and Host to Templates and Collectors. Policies are evaluated in order (lower order or rank is higher priority) and the policy that matches first is selected. Therefore, define the exceptions first followed by broad policies. Hosts are defined in terms of CMDB Device Groups or Business Services. Multiple templates can be used in one Policy and the system detects conflicts, if any.
Complete these steps to associate a Host to Template:
- Click New under the section Host To Template Associations.
- In the Host To Template Associations dialog box, enter the information below.
Settings Guidelines Name Name of the Host to Template Association. Organization Select the organization. Host Use the drop-down list to browse the folders and select the Devices or/and Business Services to monitor and click Save. Template Select one or more monitoring templates from the list or select All Templates to include all. You can also use the search bar to find any specific template. Collector Select the Collector from the list or select All Collectors to include all. Agents forward events to Collectors via HTTP(S). A Collector is chosen at random and if that Collector is not available or non-responsive, then another Collector in the list is chosen. - Click Save and Apply.
A Rank is automatically assigned to the association.
You can use the Edit button to modify or Delete button to remove any template association.
Viewing Agent Status
Complete these steps to view the Windows Agent status for any specific device:
- Go to CMDB > Devices and select the device.
The following fields display the information related to the Agent:- Agent Status: status of the Agent on the device
- Agent Policy: agent policy name
- Monitor Status: status of monitoring
The Agent Status indicates the following:
Status Description Registered Agent has completed registration but has not received the monitoring template. Running Active Agent has received a monitoring template and it is performing properly. Running Inactive Agent is running but does not have a monitoring template – the reasons can be (a) no license or (b) incomplete definition - no Collector or Template is defined for that host. Stopped Agent is stopped on the Linux Server. Disconnected Supervisor did not receive any status from the Agent for the last 10 minutes.
Enabling or Disabling an Agent
Complete these steps to enable or disable Agent for a specific device:
- Go to CMDB > Devices and select the required device.
- Select the Action drop-down menu and click Enable Agent to enable or Disable Agent to disable Agent monitoring for the selected device.
Viewing Files in FortiSIEM
If the FortiSIEM Agent is running on a Server and a FIM policy is enabled with Push Files On Modify, then the FortiSIEM Agent will send the files to FortiSIEM when a change is detected. FortiSIEM stores the files in SVN on the Supervisor.
- Go to the CMDB page. Make sure that AGENT is one of the Methods.
- Search for the device in CMDB by name.
Use the host name that you used in the
InstallSettings.xmlfile to install the Windows Agent. - Click File beneath the device table.
You will see all of the files that were changed since the monitoring template was applied.
- Select a file.
If you need to search for a file, set the From and To dates. The files which changed between those dates will be displayed.
- Click the file name on the left and its contents will be displayed in the right hand window.
Each file has a header containing file meta data followed by the actual file content.
FILEPATH: The full file name, including the path.
ARCHIVE: Set to true if ArchiveBit is set; set to false if it is not.
HASHCODE: The file hash.
HASHALGO: The algorithm used to compute file hash.
OWNER: The file owner.
USER, PERMIT, DENY: Permissions are specified as a (User, Permit, Deny) triple. This describes the actions that the user is allowed to perform.
MODIFIED_TIME: The time when the file was last modified.
- To see the differences between two files, select two files on left and click Diff.
Verifying Events in FortiSIEM
Follow the steps below to verify the events in FortiSIEM:
- Go to ANALYTICS tab.
- Click the Filters field.
- Create the following condition: Attribute= Raw Event Log, Operator = CONTAIN, Value = AccelOps-WUA and click Save & Run.
Note: All event types for all Windows Server generated logs are prefixed by AccelOps-WUA. - Select the following Group By:
- Reporting Device Name
- Reporting IP
- Select the following Display Fields:
- Reporting Device Name
- Reporting IP
- COUNT(Matched Events)
- Run the query for the last 15 minutes.
The query will return all hosts that reported events in the last 15 minutes.
Service Level Protection Properties
When Windows Agent is running, the FSMLogAgent is shown as part of your services on your Windows machine. The ability to Start, Stop, Pause, or Resume this service is disabled. This is intentional, to provide service level protection.
Auto Restart Service Behavior
In the event of a Windows Agent crash, Windows Agent will automatically restart itself after 60 seconds has passed.
Configuring Debug Trace Logging without Agent Service Restart
To enable/disable debug trace logging, you will need to modify the LogLevel entry in your Registry Editor. Take the following steps:
- Using the Registry Editor (Regedit), navigate to
HKEY_LOCAL_MACHINE\SOFTWARE\AccelOps\Agent. - Select
LogLevelto edit.
- Select Decimal for Base and change Value data to 2 to enable trace logging. Both "DBGTRACE" and "TRACE" information will be logged.
- Select Decimal for Base and change Value data to 1 to enable debug logging. Only "DBGTRACE" information will be logged.
Note: It will take about 2-3 minutes for your change to take effect.
Go to your log folder, typically C:\ProgramData\AccelOps\Agent\Logs, and examine your FSMLogAgent.log file with any text editor.
Configuring the Agent Database Size
The default size for your Agent Database is 1GB. If you wish to change this, you will need to modify the MaxDBSizeInMB entry in your Registry Editor. Take the following steps:
- Using the Registry Editor (Regedit), navigate to
HKEY_LOCAL_MACHINE\SOFTWARE\AccelOps\Agent. - Select
MaxDBSizeInMBto edit. - Select Decimal for Base and change Value data to the number of MB you wish to apply as the maximum capacity.
Sample Windows Agent Logs
FortiSIEM Windows Agent Manager generates Windows logs in an easy way to analyze "attribute=value" style without losing any information.
- Certificate Monitoring Logs
- System Logs
- Sysmon Logs
- Powershell Logs
- Application Logs
- Security Logs
- DNS Logs
- DHCP Logs
- IIS Logs
- DFS Logs
- File Content Monitoring Logs
- File Integrity Monitoring Logs
- Installed Software Logs
- Registry change Logs
- Removeable Media Logs
- WMI Logs
- Agent Troubleshooting Notes
Certificate Monitoring Logs
Certificate Added
2023-10-25T19:45:14Z DESKTOP-3NKROF5 192.0.2.0 AccelOps-WUA-Certificate [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="72f70ae7-1111-4dc0-1111-0c953f46f87e" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [certAction]="Added" [authority_key_id]="F4B6E1201DFE29AED2E461A5B2A225B2C817356E" [ca]="0" [common_name]="DigiCert Timestamp 2021" [issuer]="US, DigiCert Inc, www.digicert.com, DigiCert SHA2 Assured ID Timestamping CA" [key_algorithm]="RSA" [key_strength]="2160" [key_usage]="CERT_DIGITAL_SIGNATURE_KEY_USAGE" [not_valid_after]="1925424000" [not_valid_before]="1609459200" [path]="LocalMachine\Trusted Publishers" [self_signed]="0" [serial]="0D424AE0BE3A88F1111021CE1400F0DD" [sha1]="E1D782A8E191BEEF6BCA1691B5AAB494A6249BF3" [sid]="" [signing_algorithm]="sha256RSA" [store]="Trusted Publishers" [store_id]="" [store_location]="LocalMachine" [subject]="US, \"DigiCert, Inc.\", DigiCert Timestamp 2021" [subject_key_id]="3644868EA4BAB066BEBC2821111436DDE36A7ABC" [user]=""
Certificate Removed
2023-10-25T19:52:31Z DESKTOP-3NKROF5 192.0.2.0 AccelOps-WUA-Certificate [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="72f70ae7-1111-4dc0-1111-0c953f46f87e" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [certAction]="Removed" [authority_key_id]="" [ca]="0" [common_name]="expiring913" [issuer]="expiring913" [key_algorithm]="RSA" [key_strength]="2160" [key_usage]="CERT_KEY_ENCIPHERMENT_KEY_USAGE,CERT_DIGITAL_SIGNATURE_KEY_USAGE" [not_valid_after]="1694630930" [not_valid_before]="1694457530" [path]="LocalMachine\Trusted People" [self_signed]="1" [serial]="347CD406C649FDA94507BFA863904500" [sha1]="8E3D8330748D4FB01848E6663E6E209735893199" [sid]="" [signing_algorithm]="sha256RSA" [store]="Trusted People" [store_id]="" [store_location]="LocalMachine" [subject]="expiring913" [subject_key_id]="35EF93076396C311112C51BF121247284686090A" [user]=""
Certificate Expired
2023-10-25T19:46:48Z DESKTOP-3NKROF5 192.0.2.0 AccelOps-WUA-Certificate [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="72f70ae7-1111-4dc0-1111-0c953f46f87e" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [certAction]="Expired" [authority_key_id]="" [ca]="-1" [common_name]="expiring1021" [issuer]="expiring1021" [key_algorithm]="RSA" [key_strength]="2160" [key_usage]="CERT_KEY_ENCIPHERMENT_KEY_USAGE,CERT_DIGITAL_SIGNATURE_KEY_USAGE" [not_valid_after]="1697911109" [not_valid_before]="1697478510" [path]="LocalMachine\Trusted People" [self_signed]="1" [serial]="1F3EB6C111E7478E4DEE1F13EDF3935B" [sha1]="946499B4B192D27682D86F9F93522B11BF0F1AE0" [sid]="" [signing_algorithm]="sha256RSA" [store]="Trusted People" [store_id]="" [store_location]="LocalMachine" [subject]="expiring1021" [subject_key_id]="4DC106FF2111117C13B5E5C62F4C106D12C44C63" [user]=""
Certificate Expiring
2023-10-25T21:40:51Z DESKTOP-3NKROF5 192.0.2.0 AccelOps-WUA-Certificate [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="72f70ae7-1111-4dc0-1111-0c953f46f87e" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [certAction]="Expiring" [authority_key_id]="" [ca]="-1" [common_name]="expiring1029" [issuer]="expiring1029" [key_algorithm]="RSA" [key_strength]="2160" [key_usage]="CERT_KEY_ENCIPHERMENT_KEY_USAGE,CERT_DIGITAL_SIGNATURE_KEY_USAGE" [not_valid_after]="1698596479" [expiry_in_days]="3" [not_valid_before]="1698163880" [path]="LocalMachine\Preview Build Roots" [self_signed]="1" [serial]="2085D79E2DE08A9A4FE011108525F91D" [sha1]="8DA053FCEFE792FC2E57F3A218751F6070E91B78" [sid]="" [signing_algorithm]="sha256RSA" [store]="Preview Build Roots" [store_id]="" [store_location]="LocalMachine" [subject]="expiring1029" [subject_key_id]="362A38630797FF2C78B1A9AE1E1116927C633FA0" [user]=""
System Logs
- System Logs generated by pre-7.1.4 Windows Agent
- System Logs generated by 7.1.4 and later Windows Agent
System Logs generated by pre-7.1.4 Windows Agent
2024-02-20T23:24:58Z FSM-GFU-Windows2019-WIN2019-172-30-56-129 172.30.56.129 AccelOps-WUA-WinLog-System [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="1e749ab9-bf6e-4052-806b-02068b2d4465" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [eventName]="System" [eventSource]="Service Control Manager" [eventId]="7036" [eventType]="Information" [domain]="" [computer]="FSM-GFU-Windows2019-WIN2019-172-30-56-129" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="Feb 20 2024 23:24:57" [deviceTime]="Feb 20 2024 23:24:57" [msg]="The Microsoft Store Install Service service entered the stopped state."
System Logs generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-26T22:22:42Z FSM-GFU-Windows2019-WIN2019-172-30-56-129 172.30.56.129 FSM-WUA-WinLog-System [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="1e749ab9-bf6e-4052-806b-02068b2d4465" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Service Control Manager' Guid='{555908d1-a6d7-4695-8e1e-26931d2012f4}' EventSourceName='Service Control Manager'/><EventID Qualifiers='16384'>7036</EventID><Version>0</Version><Level>4</Level><Task>0</Task><Opcode>0</Opcode><Keywords>0x8080000000000000</Keywords><TimeCreated SystemTime='2024-02-26T22:22:41.078643000Z'/><EventRecordID>168290</EventRecordID><Correlation/><Execution ProcessID='744' ThreadID='3880'/><Channel>System</Channel><Computer>FSM-GFU-Windows2019-WIN2019-172-30-56-129</Computer><Security/></System><EventData><Data Name='param1'>Network Setup Service</Data><Data Name='param2'>stopped</Data><Binary>4E0065007400530065007400750070005300760063002F0031000000</Binary></EventData><RenderingInfo Culture='en-US'><Message>The Network Setup Service service entered the stopped state.</Message><Level>Information</Level><Task></Task><Opcode></Opcode><Channel></Channel><Provider>Microsoft-Windows-Service Control Manager</Provider><Keywords><Keyword>Classic</Keyword></Keywords></RenderingInfo></Event>
Sysmon Logs
- Sysmon Logs generated by pre-7.1.4 Windows Agent
- Sysmon Logs generated by 7.1.4 and later Windows Agent
Sysmon Logs generated by pre-7.1.4 Windows Agent
2024-02-27T23:06:35Z FSM-GFU-Windows2019-WIN2019-172-30-56-129 172.30.56.129 AccelOps-WUA-WinLog-Microsoft-Windows-Sysmon/Operational [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="1e749ab9-bf6e-4052-806b-02068b2d4465" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [eventName]="Microsoft-Windows-Sysmon/Operational" [eventSource]="Microsoft-Windows-Sysmon" [eventId]="1" [eventType]="Information" [domain]="NT AUTHORITY" [computer]="FSM-GFU-Windows2019-WIN2019-172-30-56-129" [user]="SYSTEM" [userSID]="S-1-5-18" [userSIDAcctType]="User" [eventTime]="Feb 27 2024 23:06:35" [deviceTime]="Feb 27 2024 23:06:35" [msg]="Process Create:
RuleName: -
UtcTime: 2024-02-27 23:06:35.046
ProcessGuid: {1e749ab9-6afb-65de-c644-000000001600}
ProcessId: 2068
Image: C:\\Windows\\System32\\HOSTNAME.EXE
FileVersion: 10.0.17763.1 (WinBuild.160101.0800)
Description: Hostname APP
Product: Microsoft® Windows® Operating System
Company: Microsoft Corporation
OriginalFileName: hostname.exe
CommandLine: \"C:\\Windows\\system32\\HOSTNAME.EXE\"
CurrentDirectory: C:\\Windows\\system32\\
User: NT AUTHORITY\\SYSTEM
LogonGuid: {1e749ab9-4516-65c0-e703-000000000000}
LogonId: 0x3E7
TerminalSessionId: 0
IntegrityLevel: System
Hashes: MD5=7F95220A65A5A5D4A98873E86EF2E549,SHA256=1BFF2907C456F99277F45F9B2A21B1B3F11F6C01587D9E6D6F0B2B5F1472FE92,IMPHASH=5CD891320C666621E9783444DB8CBA78
ParentProcessGuid: {1e749ab9-6775-65de-7344-000000001600}
ParentProcessId: 6884
ParentImage: C:\\Program Files\\Fortinet\\FortiSIEM\\FSMLogAgent.exe
ParentCommandLine: \"C:\\Program Files\\Fortinet\\FortiSIEM\\FSMLogAgent.exe\"
ParentUser: NT AUTHORITY\\SYSTEM"
Sysmon Logs generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-27T22:18:54Z FSM-GFU-Windows2019-WIN2019-172-30-56-129 172.30.56.129 FSM-WUA-WinLog-Microsoft-Windows-Sysmon/Operational [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="1e749ab9-bf6e-4052-806b-02068b2d4465" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Microsoft-Windows-Sysmon' Guid='{5770385f-c22a-43e0-bf4c-06f5698ffbd9}'/><EventID>13</EventID><Version>2</Version><Level>4</Level><Task>13</Task><Opcode>0</Opcode><Keywords>0x8000000000000000</Keywords><TimeCreated SystemTime='2024-02-27T22:18:53.386292600Z'/><EventRecordID>42662</EventRecordID><Correlation/><Execution ProcessID='3196' ThreadID='5432'/><Channel>Microsoft-Windows-Sysmon/Operational</Channel><Computer>FSM-GFU-Windows2019-WIN2019-172-30-56-129</Computer><Security UserID='S-1-5-18'/></System><EventData><Data Name='RuleName'>InvDB-Path</Data><Data Name='EventType'>SetValue</Data><Data Name='UtcTime'>2024-02-27 22:18:53.373</Data><Data Name='ProcessGuid'>{1e749ab9-5fc0-65de-a843-000000001600}</Data><Data Name='ProcessId'>4372</Data><Data Name='Image'>C:\\Windows\\system32\\CompatTelRunner.exe</Data><Data Name='TargetObject'>\\REGISTRY\\A\\{41ae3209-e80b-5fb1-d81b-7b9b2464bf78}\\Root\\InventoryApplicationFile\\osquery.exe|7bec5ef138bedfec\\LowerCaseLongPath</Data><Data Name='Details'>c:\\program files\\fortinet\\fortisiem\\osquery.exe</Data><Data Name='User'>NT AUTHORITY\\SYSTEM</Data></EventData><RenderingInfo Culture='en-US'><Message>Registry value set:
RuleName: InvDB-Path
EventType: SetValue
UtcTime: 2024-02-27 22:18:53.373
ProcessGuid: {1e749ab9-5fc0-65de-a843-000000001600}
ProcessId: 4372
Image: C:\\Windows\\system32\\CompatTelRunner.exe
TargetObject: \\REGISTRY\\A\\{41ae3209-e80b-5fb1-d81b-7b9b2464bf78}\\Root\\InventoryApplicationFile\\osquery.exe|7bec5ef138bedfec\\LowerCaseLongPath
Details: c:\\program files\\fortinet\\fortisiem\\osquery.exe
User: NT AUTHORITY\\SYSTEM</Message><Level>Information</Level><Task>Registry value set (rule: RegistryEvent)</Task><Opcode>Info</Opcode><Channel></Channel><Provider></Provider><Keywords></Keywords></RenderingInfo></Event>
Powershell Logs
- Powershell Logs generated by pre-7.1.4 Windows Agent
- Powershell Logs generated by 7.1.4 and later Windows Agent
Powershell Logs generated by pre-7.1.4 Windows Agent
"2024-02-27T23:36:35Z FSM-GFU-Windows2019-WIN2019-172-30-56-129 172.30.56.129 AccelOps-WUA-WinLog-Windows PowerShell [phCustId]=""2000"" [customer]=""org1"" [monitorStatus]=""Success"" [Locale]=""en-US"" [MachineGuid]=""1e749ab9-bf6e-4052-806b-02068b2d4465"" [timeZone]=""-0800"" [extEventRecvProto]=""Windows Agent"" [eventName]=""Windows PowerShell"" [eventSource]=""PowerShell"" [eventId]=""600"" [eventType]=""Information"" [domain]="""" [computer]=""FSM-GFU-Windows2019-WIN2019-172-30-56-129"" [user]="""" [userSID]="""" [userSIDAcctType]="""" [eventTime]=""Feb 27 2024 23:36:35"" [deviceTime]=""Feb 27 2024 23:36:35"" [msg]=""Provider \""WSMan\"" is Started. Details:
ProviderName=WSMan
NewProviderState=Started
SequenceNumber=55
HostName=Default Host
HostVersion=5.1.17763.1432
HostId=98d60fba-a813-4b20-9052-b56a1d052bc8
HostApplication=C:\\Program Files\\Fortinet\\FortiSIEM\\FSMLogAgent.exe
EngineVersion=
RunspaceId=
PipelineId=
CommandName=
CommandType=
ScriptName=
CommandPath=
CommandLine="""
Powershell Logs generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-27T23:16:39Z GFU-Win11.getest.com 172.30.56.124 FSM-WUA-WinLog-Windows PowerShell [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="f91bb25d-8ac1-45ea-8345-6263c2168970" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='PowerShell'/><EventID Qualifiers='0'>403</EventID><Version>0</Version><Level>4</Level><Task>4</Task><Opcode>0</Opcode><Keywords>0x80000000000000</Keywords><TimeCreated SystemTime='2024-02-27T23:16:39.7709133Z'/><EventRecordID>416398</EventRecordID><Correlation/><Execution ProcessID='6064' ThreadID='0'/><Channel>Windows PowerShell</Channel><Computer>GFU-Win11.getest.com</Computer><Security/></System><EventData><Data>Stopped</Data><Data>Available</Data><Data> NewEngineState=Stopped
PreviousEngineState=Available
SequenceNumber=2219
HostName=Default Host
HostVersion=5.1.22000.2538
HostId=b0f192dd-bf79-4fed-9740-8f556f9f63d8
HostApplication=C:\\Program Files\\Fortinet\\FortiSIEM\\FSMLogAgent.exe
EngineVersion=5.1.22000.2538
RunspaceId=0812ae9a-0717-469e-a4de-1103ff4404b3
PipelineId=
CommandName=
CommandType=
ScriptName=
CommandPath=
CommandLine=</Data></EventData><RenderingInfo Culture='en-US'><Message>Engine state is changed from Available to Stopped.
Details:
NewEngineState=Stopped
PreviousEngineState=Available
SequenceNumber=2219
HostName=Default Host
HostVersion=5.1.22000.2538
HostId=b0f192dd-bf79-4fed-9740-8f556f9f63d8
HostApplication=C:\\Program Files\\Fortinet\\FortiSIEM\\FSMLogAgent.exe
EngineVersion=5.1.22000.2538
RunspaceId=0812ae9a-0717-469e-a4de-1103ff4404b3
PipelineId=
CommandName=
CommandType=
ScriptName=
CommandPath=
CommandLine=</Message><Level>Information</Level><Task>Engine Lifecycle</Task><Opcode>Info</Opcode><Channel></Channel><Provider></Provider><Keywords><Keyword>Classic</Keyword></Keywords></RenderingInfo></Event>
Application Logs
- Application Logs generated by pre-7.1.4 Windows Agent
- Application Logs generated by 7.1.4 and later Windows Agent
Application Logs generated by pre-7.1.4 Windows Agent
2024-02-27T17:32:20Z FSM-GFU-Windows8-George-172-30-56-122 172.30.56.122 AccelOps-WUA-WinLog-Application [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="69c490e4-9c32-49cb-aefa-3ff10bcfc98a" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [eventName]="Application" [eventSource]="Microsoft-Windows-Security-SPP" [eventId]="16384" [eventType]="Information" [domain]="" [computer]="FSM-GFU-Windows8-George-172-30-56-122" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="Feb 27 2024 17:32:20" [deviceTime]="Feb 27 2024 17:32:20" [msg]="Successfully scheduled Software Protection service for re-start at 2024-02-28T00:55:20Z. Reason: RulesEngine."
Application Logs generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-27T20:07:07Z GFU-Win11.getest.com 172.30.56.124 FSM-WUA-WinLog-Application [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="f91bb25d-8ac1-45ea-8345-6263c2168970" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Microsoft-Windows-Security-SPP' Guid='{E23B33B0-C8C9-472C-A5F9-F2BDFEA0F156}' EventSourceName='Software Protection Platform Service'/><EventID Qualifiers='16384'>16384</EventID><Version>0</Version><Level>4</Level><Task>0</Task><Opcode>0</Opcode><Keywords>0x80000000000000</Keywords><TimeCreated SystemTime='2024-02-27T20:07:07.0902766Z'/><EventRecordID>75607</EventRecordID><Correlation/><Execution ProcessID='5284' ThreadID='0'/><Channel>Application</Channel><Computer>GFU-Win11.getest.com</Computer><Security/></System><EventData><Data>2024-02-28T19:25:07Z</Data><Data>RulesEngine</Data></EventData><RenderingInfo Culture='en-US'><Message>Successfully scheduled Software Protection service for re-start at 2024-02-28T19:25:07Z. Reason: RulesEngine.</Message><Level>Information</Level><Task></Task><Opcode></Opcode><Channel></Channel><Provider>Microsoft-Windows-Security-SPP</Provider><Keywords><Keyword>Classic</Keyword></Keywords></RenderingInfo></Event>
Security Logs
- Security Logs generated by pre-7.1.4 Windows Agent
- Security Logs generated by 7.1.4 and later Windows Agent
- Security Logs in French Windows generated by pre-7.1.4 Windows Agent
- Security Logs in French Windows generated by 7.1.4 and later Windows Agent
Security Logs generated by pre-7.1.4 Windows Agent
2024-02-22T01:07:51Z GFU-Win10.gfu.com 172.30.56.127 AccelOps-WUA-WinLog-Security [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="72f70ae7-fedf-4dc0-92e7-0c953f46f87e" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [eventName]="Security" [eventSource]="Microsoft-Windows-Security-Auditing" [eventId]="4703" [eventType]="Information" [domain]="" [computer]="GFU-Win10.gfu.com" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="Feb 22 2024 01:07:51" [deviceTime]="Feb 22 2024 01:07:51" [msg]="A token right was adjusted." [[Subject]][Security ID]="S-1-5-18" [Account Name]="GFU-WIN10$" [Account Domain]="GFU" [Logon ID]="0x3E7" [[Target Account]][Security ID]="S-1-5-18" [Account Name]="GFU-WIN10$" [Account Domain]="GFU" [Logon ID]="0x3E7" [[Process Information]][Process ID]="0x3348" [Process Name]="C:\\Windows\\System32\\msiexec.exe" [Enabled Privileges]="" [Disabled Privileges]="SeRestorePrivilege,SeTakeOwnershipPrivilege"
Security Logs generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-27T21:19:33Z FSM-GFU-Windows2019-WIN2019-172-30-56-129 172.30.56.129 FSM-WUA-WinLog-Security [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="1e749ab9-bf6e-4052-806b-02068b2d4465" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Microsoft-Windows-Security-Auditing' Guid='{54849625-5478-4994-a5ba-3e3b0328c30d}'/><EventID>4703</EventID><Version>0</Version><Level>0</Level><Task>13317</Task><Opcode>0</Opcode><Keywords>0x8020000000000000</Keywords><TimeCreated SystemTime='2024-02-27T21:19:32.430796700Z'/><EventRecordID>9064813051</EventRecordID><Correlation/><Execution ProcessID='4' ThreadID='5944'/><Channel>Security</Channel><Computer>FSM-GFU-Windows2019-WIN2019-172-30-56-129</Computer><Security/></System><EventData><Data Name='SubjectUserSid'>S-1-5-18</Data><Data Name='SubjectUserName'>FSM-GFU-WINDOWS$</Data><Data Name='SubjectDomainName'>WORKGROUP</Data><Data Name='SubjectLogonId'>0x3e7</Data><Data Name='TargetUserSid'>S-1-0-0</Data><Data Name='TargetUserName'>FSM-GFU-WINDOWS$</Data><Data Name='TargetDomainName'>WORKGROUP</Data><Data Name='TargetLogonId'>0x3e7</Data><Data Name='ProcessName'>C:\\Windows\\System32\\svchost.exe</Data><Data Name='ProcessId'>0xbdc</Data><Data Name='EnabledPrivilegeList'>SeAssignPrimaryTokenPrivilege
SeIncreaseQuotaPrivilege
SeSecurityPrivilege
SeTakeOwnershipPrivilege
SeLoadDriverPrivilege
SeSystemtimePrivilege
SeBackupPrivilege
SeRestorePrivilege
SeShutdownPrivilege
SeSystemEnvironmentPrivilege
SeUndockPrivilege
SeManageVolumePrivilege</Data><Data Name='DisabledPrivilegeList'>-</Data></EventData></Event>
Security Logs in French Windows generated by pre-7.1.4 Windows Agent
2024-02-27T21:59:31Z WIN-H8PJIB0G6QJ 172.30.56.128 AccelOps-WUA-WinLog-Security [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="fr-FR" [MachineGuid]="d1a2dfa9-a8a3-4d5d-b151-2264a07678b4" [timeZone]="+0100" [extEventRecvProto]="Windows Agent" [eventName]="Security" [eventSource]="Microsoft-Windows-Security-Auditing" [eventId]="4798" [eventType]="Information" [domain]="" [computer]="WIN-H8PJIB0G6QJ" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="Feb 27 2024 21:59:31" [deviceTime]="Feb 27 2024 21:59:31" [msg]="Une adhésion au groupe local d'un utilisateur a été énumérée." [[Objet]][ID de sécurité]="S-1-5-18" [Nom du compte]="WIN-H8PJIB0G6QJ$" [Domaine du compte]="WORKGROUP" [ID d'ouverture de session]="0x3E7" [[Utilisateur]][ID de sécurité]="S-1-5-21-1726319904-1389896535-1900308177-500" [Nom du compte]="Administrateur" [Domaine du compte]="WIN-H8PJIB0G6QJ" [[Informations sur le processus]][ID du processus]="0x1270" [Nom du processus]="C:\\Program Files\\Fortinet\\FortiSIEM\\osquery.exe"
Security Logs in French Windows generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-27T21:50:49Z WIN-H8PJIB0G6QJ 172.30.56.128 FSM-WUA-WinLog-Security [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="fr-FR" [MachineGuid]="d1a2dfa9-a8a3-4d5d-b151-2264a07678b4" [timeZone]="+0100" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Microsoft-Windows-Security-Auditing' Guid='{54849625-5478-4994-a5ba-3e3b0328c30d}'/><EventID>4798</EventID><Version>0</Version><Level>0</Level><Task>13824</Task><Opcode>0</Opcode><Keywords>0x8020000000000000</Keywords><TimeCreated SystemTime='2024-02-27T21:50:49.478751700Z'/><EventRecordID>217951</EventRecordID><Correlation ActivityID='{dc36aa0a-69c4-0001-58aa-36dcc469da01}'/><Execution ProcessID='612' ThreadID='4748'/><Channel>Security</Channel><Computer>WIN-H8PJIB0G6QJ</Computer><Security/></System><EventData><Data Name='TargetUserName'>WDAGUtilityAccount</Data><Data Name='TargetDomainName'>WIN-H8PJIB0G6QJ</Data><Data Name='TargetSid'>S-1-5-21-1726319904-1389896535-1900308177-504</Data><Data Name='SubjectUserSid'>S-1-5-18</Data><Data Name='SubjectUserName'>WIN-H8PJIB0G6QJ$</Data><Data Name='SubjectDomainName'>WORKGROUP</Data><Data Name='SubjectLogonId'>0x3e7</Data><Data Name='CallerProcessId'>0x128</Data><Data Name='CallerProcessName'>C:\\Program Files\\Fortinet\\FortiSIEM\\osquery.exe</Data></EventData></Event>
DNS Logs
- DNS System Logs generated by pre-7.1.4 Windows Agent
- DNS System Logs generated by 7.1.4 and later Windows Agent
DNS System Logs generated by pre-7.1.4 Windows Agent
2024-02-28T00:05:04Z GFU-WIN2016.getest.com 172.30.56.121 AccelOps-WUA-WinLog-DNS Server [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="4a2804f4-e1b6-4e28-ac76-de5aa103d255" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [eventName]="DNS Server" [eventSource]="Microsoft-Windows-DNS-Server-Service" [eventId]="2" [eventType]="Information" [domain]="NT AUTHORITY" [computer]="GFU-WIN2016.getest.com" [user]="SYSTEM" [userSID]="S-1-5-18" [userSIDAcctType]="User" [eventTime]="Feb 28 2024 00:05:03" [deviceTime]="Feb 28 2024 00:05:03" [msg]="The DNS server has started."
DNS System Logs generated by 7.1.4 and later Windows Agent
The events are generated in XML format.
2024-02-27T23:50:52Z GFU-WIN2016-126.gfu.com 172.30.56.126 FSM-WUA-WinLog-DNS Server [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="967fcbac-7d74-445f-99de-c5a1f0acf59d" [timeZone]="-0800" [extEventRecvProto]="Windows Agent" [level]="Information" [xml]=<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name='Microsoft-Windows-DNS-Server-Service' Guid='{71A551F5-C893-4849-886B-B5EC8502641E}'/><EventID>2</EventID><Version>0</Version><Level>4</Level><Task>0</Task><Opcode>0</Opcode><Keywords>0x8000000000001000</Keywords><TimeCreated SystemTime='2024-02-27T23:50:51.965038300Z'/><EventRecordID>330</EventRecordID><Correlation/><Execution ProcessID='6448' ThreadID='6892'/><Channel>DNS Server</Channel><Computer>GFU-WIN2016-126.gfu.com</Computer><Security UserID='S-1-5-18'/></System><EventData Name='DNS_EVENT_STARTUP_OK'></EventData><RenderingInfo Culture='en-US'><Message>The DNS server has started.</Message><Level>Information</Level><Task></Task><Opcode>Info</Opcode><Channel></Channel><Provider>Microsoft-Windows-DNS-Server-Service</Provider><Keywords></Keywords></RenderingInfo></Event>
DHCP Logs
AccelOps-WUA-DHCP-Generic Thu May 07 05:44:44 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-DHCP [monitorStatus]="Success" [ID]="00" [Date]="05/07/15" [Time]="13:44:08" [Description]="Started" [IP Address]="" [Host Name]="" [MAC Address]="" [User Name]="" [ TransactionID]="0" [ QResult]="6" [Probationtime]="" [ CorrelationID]="" [Dhcid.]=""
#AccelOps-WUA-DHCP-IP-ASSIGN Thu May 07 05:56:41 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-DHCP [monitorStatus]="Success" [ID]="10" [Date]="05/07/15" [Time]="13:56:37" [Description]="Assign" [IP Address]="10.1.2.124" [Host Name]="Agent-247.yj" [MAC Address]="000C2922118E" [User Name]="" [ TransactionID]="2987030242" [ QResult]="0" [Probationtime]="" [ CorrelationID]="" [Dhcid.]=""
#AccelOps-WUA-DHCP-Generic(Release) Thu May 07 05:56:41 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-DHCP [monitorStatus]="Success" [ID]="12" [Date]="05/07/15" [Time]="13:56:33" [Description]="Release" [IP Address]="10.1.2.124" [Host Name]="Agent-247.yj" [MAC Address]="000C2922118E" [User Name]="" [ TransactionID]="2179405838" [ QResult]="0" [Probationtime]="" [ CorrelationID]="" [Dhcid.]=""
#AccelOps-WUA-DHCP-IP-LEASE-RENEW Wed Feb 25 02:53:28 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-DHCP [monitorStatus]="Success" [ID]="11" [Date]="02/25/15" [Time]="10:53:19" [Description]="Renew" [IP Address]="10.1.2.123" [Host Name]="WIN-2008-249.yj" [MAC Address]="0050568F1B5D" [User Name]="" [ TransactionID]="1136957584" [ QResult]="0" [Probationtime]="" [ CorrelationID]="" [Dhcid.]=""
IIS Logs
#AccelOps-WUA-IIS-Web-Request-Success Thu May 07 03:49:23 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-IIS [monitorStatus]="Success" [date]="2015-05-07" [time]="03:44:28" [s-sitename]="W3SVC1" [s-computername]="WIN-2008-LAW-AG" [s-ip]="10.1.2.242" [cs-method]="GET" [cs-uri-stem]="/welcome.png" [cs-uri-query]="-" [s-port]="80" [cs-username]="-" [c-ip]="10.1.20.232" [cs-version]="HTTP/1.1" [cs(User-Agent)]="Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/42.0.2311.135+Safari/537.36" [cs(Cookie)]="-" [cs(Referer)]="http://10.1.2.242/" [cs-host]="10.1.2.242" [sc-status]="200" [sc-substatus]="0" [sc-win32-status]="0" [sc-bytes]="185173" [cs-bytes]="324" [time-taken]="78" [site]="Default Web Site" [format]="W3C"
#AccelOps-WUA-IIS-Web-Client-Error Thu May 07 03:49:23 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-IIS [monitorStatus]="Success" [date]="2015-05-07" [time]="03:44:37" [s-sitename]="W3SVC1" [s-computername]="WIN-2008-LAW-AG" [s-ip]="10.1.2.242" [cs-method]="GET" [cs-uri-stem]="/wrongpage" [cs-uri-query]="-" [s-port]="80" [cs-username]="-" [c-ip]="10.1.20.232" [cs-version]="HTTP/1.1" [cs(User-Agent)]="Mozilla/5.0+(Windows+NT+6.1;+WOW64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/42.0.2311.135+Safari/537.36" [cs(Cookie)]="-" [cs(Referer)]="-" [cs-host]="10.1.2.242" [sc-status]="404" [sc-substatus]="0" [sc-win32-status]="2" [sc-bytes]="1382" [cs-bytes]="347" [time-taken]="0" [site]="Default Web Site" [format]="W3C"
#AccelOps-WUA-IIS-Web-Forbidden-Access-Denied Thu May 07 03:30:39 2015 WIN-2008-249.ersijiu.com 10.1.2.249 AccelOps-WUA-IIS [monitorStatus]="Success" [date]="2015-05-07" [time]="03:30:15" [s-ip]="10.1.2.249" [cs-method]="POST" [cs-uri-stem]="/AOCACWS/AOCACWS.svc" [cs-uri-query]="-" [s-port]="80" [cs-username]="-" [c-ip]="10.1.2.42" [cs(User-Agent)]="-" [sc-status]="403" [sc-substatus]="4" [sc-win32-status]="5" [time-taken]="1" [site]="Default Web Site" [format]="W3C"
DFS Logs
#Win-App-DFSR-1002 Thu May 07 03:01:12 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-WinLog [monitorStatus]="Success" [eventName]="DFS Replication" [eventSource]="DFSR" [eventId]="1002" [eventType]="Information" [domain]="" [computer]="WIN-2008-LAW-agent" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="May 07 2015 11:01:12" [deviceTime]="May 07 2015 11:01:12" [msg]="The DFS Replication service is starting."
#Win-App-DFSR-1004 Thu May 07 03:01:12 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-WinLog [monitorStatus]="Success" [eventName]="DFS Replication" [eventSource]="DFSR" [eventId]="1004" [eventType]="Information" [domain]="" [computer]="WIN-2008-LAW-agent" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="May 07 2015 11:01:12" [deviceTime]="May 07 2015 11:01:12" [msg]="The DFS Replication service has started."
#Win-App-DFSR-1006 Thu May 07 03:01:10 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-WinLog [monitorStatus]="Success" [eventName]="DFS Replication" [eventSource]="DFSR" [eventId]="1006" [eventType]="Information" [domain]="" [computer]="WIN-2008-LAW-agent" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="May 07 2015 11:01:10" [deviceTime]="May 07 2015 11:01:10" [msg]="The DFS Replication service is stopping."
#Win-App-DFSR-1008 Thu May 07 03:01:11 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-WinLog [monitorStatus]="Success" [eventName]="DFS Replication" [eventSource]="DFSR" [eventId]="1008" [eventType]="Information" [domain]="" [computer]="WIN-2008-LAW-agent" [user]="" [userSID]="" [userSIDAcctType]="" [eventTime]="May 07 2015 11:01:11" [deviceTime]="May 07 2015 11:01:11" [msg]="The DFS Replication service has stopped."
File Content Monitoring Logs
#AccelOps-WUA-UserFile Thu May 07 05:40:08 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-UserFile [monitorStatus]="Success" [fileName]="C:\test\i.txt" [msg]="another newline adddedddddd"
File Integrity Monitoring Logs
The following sections describe various use cases that can be detected by File Integrity Monitoring Logs.
- Use Case 1: File or Directory Created
- Use Case 2: File or Directory Deleted
- Use Case 3: File Content Modified
- Use Case 4: File Content Modified and Upload is Selected
- Use Case 5: File Renamed
- Use Case 6: File Permission Changed
- Use Case 7: File Ownership Changed
- Use Case 8: File Archive Bit Changed
- Use Case 9: File Baseline Changed
Use Case 1: File or Directory Created
Event Type
AO-WUA-FileMon-Added
Important Event Attributes
userId: The ID of the user who added the file.domain: The user’s domain for a Domain computer.osObjType- Can be either File or Directory.fileName: The name of the file or directory that was added.hashCode, hashAlgo: The file hash obtained by using the specified algorithm.procName: The name of the Windows process that was used to create the file.fileOwner: The owner of the file.targetUserType, targetUser: The user or group to whom the permission applies.targetFilePermit: The permitted file operations.targetFileDeny: The denied file operations.archiveSet: Istrueif the Archive bit is set for this file;falseotherwise.
Reports
Agent FIM: Windows File/Directory Created/Deleted/Renamed
Rules
Agent FIM - Windows File or Directory Created
Sample Log
2020-03-25T07:30:50Z Win-167 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="jdoe" [domain]="ACME" [eventTime]="Mar 25 2020 07:30:48" [fileName]="C:\\test\\New Text Document.txt" [osObjAction]="Added" [objectType]="File" [hashCode]="e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855" [hashAlgo]="SHA256" [procName]="C:\\Windows\\explorer.exe" [msg]="" [archiveSet]="true" [fileOwner]=""
Use Case 2: File or Directory Deleted
Event Type
AO-WUA-FileMon-Removed
Important Event Attributes
userId: The ID of the user who removed the file.domain: The user’s domain for a Domain computer.fileName: The name of the file that was removed.procName: The Windows process that was used to remove the file.
Report
Agent FIM: Windows File/Directory Creation/Deletion/Rename
Rule
Agent FIM - Windows File or Directory Deleted
Sample Log
2020-03-25T07:43:24Z Win-167 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="jdoe" [domain]="ACME" [eventTime]="Mar 25 2020 07:43:21" [fileName]="C:\\test\\test1.txt" [osObjAction]="Removed" [objectType]="Unknown" [hashCode]="" [hashAlgo]="SHA256" [procName]="C:\\Windows\\explorer.exe" [msg]="" [archiveSet]="false" [fileOwner]=""
Use Case 3: File Content Modified
Event Type
AO-WUA-FileMon-Modified
Important Event Attributes
userId: The user who modified the file.domain: The user’s domain for a Domain computer.fileName: The name of the file that was modified.procName: The Windows process that was used to modify the file.hashCode, hashAlgo: The file hash after modification and the algorithm used to calculate the hash.
Report
Agent FIM: Windows File Content Modified
Rule
Agent FIM - Windows File Content Modified
Sample Log
2020-03-25T10:50:40Z WIN-167.fortinet.wulei.com 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="jdoe" [domain]="ACME" [eventTime]="Mar 25 2020 10:50:37" [fileName]="C:\\test\\test.txt" [osObjAction]="Modified" [objectType]="File" [hashCode]="6396e3c19b155770f3ae25afa5f29832d6f35b315407ed88820339b705fd2bcc" [hashAlgo]="SHA256" [procName]="C:\\Windows\\System32\<br/>otepad.exe" [msg]="" [archiveSet]="true" [fileOwner]=""
Use Case 4: File Content Modified and Upload is Selected
Event Type
PH_DEV_MON_FILE_CONTENT_CHANGE
Important Event Attributes
userId: The ID of the user who modified the file.domain: The user’s domain for a Domain computer.fileName: The name of the file that was modified.procName: The Windows process that was used to modify the file.hashCode, hashAlgo: The file hash after modification and the algorithm used to calculate the hash.oldSVNVersion: The SVN revision number of file before the change.newSVNVersion: The SVN revision number of file after the change.addedItem: The lines that were added to the file.deletedItem: The lines that were removed from the file.
Report
Agent FIM: Windows File Content Modified in SVN
Rule
Audited file or directory content modified in SVN
Sample Log
<14>Mar 25 20:30:44 sp3 phPerfMonitor[17521]: [PH_DEV_MON_FILE_CONTENT_CHANGE]:[eventSeverity]=PHL_INFO,[procName]=phPerfMonitor,[fileName]=phSvnUpdate.cpp,[lineNumber]=306,[phCustId]=2000,[hostName]=Win-169,[hostIpAddr]=10.30.3.169,[fileName]=/C:/test/test.txt,[hashCode]=08998b2cce90ee6695bd8dae82d43137,[oldSVNVersion]=50,[newSVNVersion]=51,[deletedItem]=(none),[addedItem]=333;,[user]=Administrator,[hashAlgo]=SHA256,[phLogDetail]=
Use Case 5: File Renamed
Event Type
AO-WUA-FileMon-Renamed-New-Name
Important Event Attributes
userId: The ID of the user who renamed the file.domain: The user’s domain for a Domain computer.fileName: The new name of the file.procName: The Windows process that was used to rename the file.hashCode, hashAlgo: The new file hash using the specified algorithm.
Report
Agent FIM: Windows File/Directory Creation/Deletion/Rename
Rule
None
Sample Log
2020-03-25T09:59:34Z WIN-167.fortinet.wulei.com 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="jdoe" [domain]="ACME" [eventTime]="Mar 25 2020 09:59:32" [fileName]="C:\\test\\test5.txt" [osObjAction]="Renamed [New Name]" [objectType]="File" [hashCode]="2b64c6d9afd8a34ed0dbf35f7de171a8825a50d9f42f05e98fe2b1addf00ab44" [hashAlgo]="SHA256" [procName]="C:\\Windows\\explorer.exe" [msg]="" [archiveSet]="true" [fileOwner]=""
Event Type
AO-WUA-FileMon-Renamed-Old-Name
Important Event Attributes
userId: The ID of the user who modified the file.
domain: The user’s domain for a Domain computer.
fileName: The old name of the file before renaming.
procName: The Windows process that was used to remove the file.
Report
Agent FIM: Windows File/Directory Creation/Deletion/Rename
Rule
None
Sample Log
None
Use Case 6: File Permission Changed
Event Type
AO-WUA-FileMon-PermissionChange
Important Event Attributes
userId: The ID of the user who modified the file permission.domain: The user’s domain for a Domain computer.objectType: The type of object. Can beFileorDirectory.fileName: The name of the file or directory whose permission was changed.procName: The Windows process that was used to change the permission.hashCode, hashAlgo: The file hash using the specified algorithm.fileOwner: The name of the owner of the file.targetUserType, targetUser: The name of the user or group to whom the permission below applies.targetFilePermit: The permitted file operations after change.targetFileDeny: The denied file operations after change.archiveSet: Istrueif theArchivebit is set for this file;falseotherwise.
Report
Agent FIM: Windows File/Directory Permission Changes
Rule
Agent FIM - Windows File Permission Changed
Sample Log
2020-03-25T10:21:00Z WIN-167.fortinet.wulei.com 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="jdoe" [domain]="ACME" [eventTime]="Mar 25 2020 10:20:58" [fileName]="C:\\test\\test.txt" [osObjAction]="PermissionChange" [objectType]="File" [hashCode]="7936d255ef43706a93fdd15f4bbfde45e3b2d2b9a0d4cc7c39184cf745ab78c5" [hashAlgo]="SHA256" [procName]="C:\\Windows\\System32\\dllhost.exe" [msg]="" [archiveSet]="true" [fileOwner]=“Joe” [targetUserType]="USER" [targetUser]="BUILTIN\Administrators" [targetFilePermit]="ALL" [targetFileDeny]="WRITE"
Use Case 7: File Ownership Changed
Event Type
AO-WUA-FileMon-OwnershipChange
Important Event Attributes
userId: The ID of the user who modified the file ownership.domain: The user’s domain for a Domain computer.objectType: The type of object whose ownership was changed:FileorDirectory.fileName: The name of the file or directory whose ownership was changed.procName: The Windows process that was used to change ownership.hashCode, hashAlgo: The file hash using the specified algorithm.fileOwner: The name of the new file owner.archiveSet: Istrueif theArchivebit is set for this file;falseotherwise.
Report
Agent FIM: Windows File/Directory Ownership Changes
Rule
Agent FIM - Windows File Ownership Changed
Sample Log
2020-03-06T07:08:56Z Win-167 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="1" [customer]="super" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="Administrator" [domain]="WIN-167" [eventTime]="Mar 06 2020 07:08:53" [fileName]="C:\\test\\test1.txt" [osObjAction]="OwnershipChange" [objectType]="File" [hashCode]="d17f25ecfbcc7857f7bebea469308be0b2580943e96d13a3ad98a13675c4bfc2" [hashAlgo]="SHA256" [procName]="C:\\Windows\\System32\\dllhost.exe" [msg]="" [archiveSet]="true" [fileOwner]=“Joe”
Use Case 8: File Archive Bit Changed
Event Type
AO-WUA-FileMon-ArchivedBitChange
Important Event Attributes
userId: The ID of the user who modified the file.domain: The user’s domain for a Domain computer.objectType: The type of object whoseArchivebit was changed:FileorDirectory.fileName: The name of the file whose archive bit was changed.procName: The Windows process that was used to change archive bit.hashCode, hashAlgo: The file hash using the specified algorithm.archiveSet: Istrueif theArchivebit is set for this file;falseotherwise.
Report
Agent FIM: Windows File/Directory Archive Bit Changes
Rule
Agent FIM - Windows File/Directory Archive Bit Changed
Sample Log
2020-03-25T10:02:38Z WIN-167.fortinet.wulei.com 10.30.2.167 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="e892a6e4-bbfa-4ba6-bc8c-00d2c31812b4" [timeZone]="+0800" [userId]="jdoe" [domain]="ACME" [eventTime]="Mar 25 2020 10:02:35" [fileName]="C:\\test\\test.txt" [osObjAction]="ArchivedBitChange" [objectType]="File" [hashCode]="7936d255ef43706a93fdd15f4bbfde45e3b2d2b9a0d4cc7c39184cf745ab78c5" [hashAlgo]="SHA256" [procName]="C:\\Windows\\System32\\attrib.exe" [msg]="" [archiveSet]="false" [fileOwner]=""
Use Case 9: File Baseline Changed
Event Type
AO-WUA-FileMon-BaselineChange
Important Event Attributes
userId: The ID of the user who modified the file.domain: The user’s domain for a Domain computer.fileName: The name of the file that was changed.procName: The Windows process that was used to remove the file.hashCode, hashAlgo: The file hash using the specified algorithm.targetHashCode: The hash of the target file (defined in the GUI).
Report
Agent FIM: Windows File Change from Baseline
Rule
Agent FIM - Windows File Changed From Baseline
Sample Log
2020-03-25T12:52:42Z Win-169 10.30.3.169 AccelOps-WUA-FileMon [phCustId]="2000" [customer]="org1" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="5c83ec12-73fd-4e06-a396-1f128564f09e" [timeZone]="+0800" [userId]="Administrator" [domain]="WINSRV2012-169" [fileName]="C:\\test\\test.txt" [osObjAction]="BaselineChange" [hashCode]="c1f79ea2bbfb77bf30446a4c9be762eb" [hashAlgo]="MD5" [targetHashCode]="74DE7651DFC55294CC59240AE514A676" [msg]="
Installed Software Logs
#AccelOps-WUA-InstSw-Added Thu May 07 05:28:17 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-InstSw [monitorStatus]="Success" [osObjAction]="Added" [appName]="7-Zip 9.20 (x64 edition)" [vendor]="Igor Pavlov" [appVersion]="9.20.00.0"
#AccelOps-WUA-InstSw-Removed Thu May 07 05:28:30 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-InstSw [monitorStatus]="Success" [osObjAction]="Removed" [appName]="7-Zip 9.20 (x64 edition)" [vendor]="Igor Pavlov" [appVersion]="9.20.00.0"
Registry Change Logs
#AccelOps-WUA-Registry-Modified
Thu May 07 04:01:58 2015 WIN-2008-249.ersijiu.com 10.1.2.249 AccelOps-WUA-Registry [monitorStatus]="Success" [regKeyPath]="HKLM\\SOFTWARE\\Microsoft\\ExchangeServer\\v14\\ContentIndex\\CatalogHealth\\{0d2a342a-0b15-4995-93db-d18c3df5860d}" [regValueName]="TimeStamp" [regValueType]="1" [osObjAction]="Modified" [oldRegValue]="MgAwADEANQAtADAANQAtADAANwAgADAAMwA6ADQAOQA6ADQANwBaAAAA"
[newRegValue]="MgAwADEANQAtADAANQAtADAANwAgADAANAA6ADAAMQA6ADQAOABaAAAA" #AccelOps-WUA-Registry-Removed Thu May 07 05:25:09 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-Registry [monitorStatus]="Success" [regKeyPath]="HKLM\\SOFTWARE\\RegisteredApplications" [regValueName]="Skype" [regValueType]="1" [osObjAction]="Removed" [oldRegValue]="UwBPAEYAVABXAEEAUgBFAFwAQwBsAGkAZQBuAHQAcwBcAEkAbgB0AGUAcgBuAGUAdAAgAEMAYQBsAGwAXABTAGsAeQBwAGUAXABDAGEAcABhAGIAaQBsAGkAdABpAGUAcwBkAGgAZABoAGQAaABkAGgAZABoAGQAAAA=" [newRegValue]=""
Removeable Media Monitoring Logs
AO-WUA-RemovableMedia-Insert
2022-06-24T19:06:55Z CD-DESK-S 0.0.0.0 AccelOps-WUA-RemovableMedia-Insert [phCustId]="1" [customer]="super" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="38ba7825-34a2-41b8-8e3d-0548878bef5b" [timeZone]="-0500" [user]="" [domain]="" [eventTime]="Jun 24 2022 19:06:55" [fileName]="" [diskName]="D:" [isMediaEncrypted]="false" [osObjAction]="" [diskType]="USB" [diskDisplayName]="Samsung USB" [diskVendor]="samsung" [hwDiskModel]="flash_drive_fit 1100" [msg]="Storage media inserted."
AO-WUA-RemovableMedia-Write-ModifyFile
2022-06-24T19:25:06Z CD-DESK-S 192.168.1.147 AccelOps-WUA-RemovableMedia-Write [phCustId]="1" [customer]="super" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="38ba7825-34a2-41b8-8e3d-0548878bef5b" [timeZone]="-0500" [user]="" [domain]="" [eventTime]="Jun 24 2022 19:25:02" [fileName]="D:\\agenttest\\Wireshark-win64-3.6.6.exe" [diskName]="D:" [isMediaEncrypted]="false" [osObjAction]="Modified" [diskType]="USB" [diskDisplayName]="Samsung USB" [diskVendor]="samsung" [hwDiskModel]="flash_drive_fit 1100" [msg]=""
AO-WUA-RemovableMedia-Write-AddFile
2022-06-24T19:25:01Z CD-DESK-S 192.168.1.147 AccelOps-WUA-RemovableMedia-Write [phCustId]="1" [customer]="super" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="38ba7825-34a2-41b8-8e3d-0548878bef5b" [timeZone]="-0500" [user]="" [domain]="" [eventTime]="Jun 24 2022 19:25:00" [fileName]="D:\\agenttest\\Wireshark-win64-3.6.6.exe" [diskName]="D:" [isMediaEncrypted]="false" [osObjAction]="Added" [diskType]="USB" [diskDisplayName]="Samsung USB" [diskVendor]="samsung" [hwDiskModel]="flash_drive_fit 1100" [msg]=""
AO-WUA-RemovableMedia-Write-RemoveFile
2022-06-24T19:24:01Z CD-DESK-S 192.168.1.147 AccelOps-WUA-RemovableMedia-Write [phCustId]="1" [customer]="super" [monitorStatus]="Success" [Locale]="en-US" [MachineGuid]="38ba7825-34a2-41b8-8e3d-0548878bef5b" [timeZone]="-0500" [user]="" [domain]="" [eventTime]="Jun 24 2022 19:23:56" [fileName]="D:\\agenttest\\WinSCP-5.17.8-Setup.zip" [diskName]="D:" [isMediaEncrypted]="false" [osObjAction]="Removed" [diskType]="USB" [diskDisplayName]="Samsung USB" [diskVendor]="samsung" [hwDiskModel]="flash_drive_fit 1100" [msg]=""
WMI logs
#AccelOps-WUA-WMI-Win32_Processor Thu May 07 03:53:33 2015 WIN-2008-LAW-agent 10.1.2.242 AccelOps-WUA-WMI [monitorStatus]="Success" [__CLASS]="Win32_Processor" [AddressWidth]="64" [Architecture]="9" [Availability]="3" [Caption]="Intel64 Family 6 Model 26 Stepping 5" [ConfigManagerErrorCode]="" [ConfigManagerUserConfig]="" [CpuStatus]="1" [CreationClassName]="Win32_Processor" [CurrentClockSpeed]="2266" [CurrentVoltage]="33" [DataWidth]="64" [Description]="Intel64 Family 6 Model 26 Stepping 5" [DeviceID]="CPU0" [ErrorCleared]="" [ErrorDescription]="" [ExtClock]="" [Family]="12" [InstallDate]="" [L2CacheSize]="0" [L2CacheSpeed]="" [L3CacheSize]="0" [L3CacheSpeed]="0" [LastErrorCode]="" [Level]="6" [LoadPercentage]="8" [Manufacturer]="GenuineIntel" [MaxClockSpeed]="2266" [Name]="Intel(R) Xeon(R) CPU E5520 @ 2.27GHz" [NumberOfCores]="1" [NumberOfLogicalProcessors]="1" [OtherFamilyDescription]="" [PNPDeviceID]="" [PowerManagementCapabilities]="" [PowerManagementSupported]="0" [ProcessorId]="0FEBFBFF000106A5" [ProcessorType]="3" [Revision]="6661" [Role]="CPU" [SocketDesignation]="CPU socket #0" [Status]="OK" [StatusInfo]="3" [Stepping]="" [SystemCreationClassName]="Win32_ComputerSystem" [SystemName]="WIN-2008-LAW-AG" UniqueId]="" [UpgradeMethod]="4" [Version]="" [VoltageCaps]="2"
Agent Troubleshooting Notes
A Windows Agent can be in following states (shown in CMDB):
- Registered
- Running Inactive
- Running Active
- Disabled
- Disconnected
When an Agent is installed and registered, then it is in Registered state. The following audit event is generated: PH_AUDIT_AGENT_INSTALLED.
When a monitoring template is assigned to the device, then the state moves to Running Inactive. When the agent receives the template and starts monitoring, then the state moves to Running Active. In both cases, the following audit event is generated: PH_AUDIT_AGENT_RUNNING.
Agent periodically sends heartbeat messages. When a heartbeat not received for 10 minutes, the state moves to Disconnected and the audit event PH_AUDIT_AGENT_NOTRESPONDING is generated. Status is checked every 1 hour. At that time, if we heard from the Agent in the last 15 minutes, the state moves back to Running Inactive and a PH_AUDIT_AGENT_RUNNING audit event is generated.
If the Agent is disabled from the GUI, the state moves to Disabled and PH_AUDIT_AGENT_DISABLED audit event is generated.
If the Agent is uninstalled or the service is stopped, then the state moves to Disconnected and the audit event PH_AUDIT_AGENT_NOTRESPONDING is generated.
Audit events are generated at state transitions, however, the event PH_AUDIT_AGENT_NOTRESPONDING is generated every hour to identify all agents that are currently disconnected. A nested query can be run to detect Agents that did not report in the last N hours. Note that PH_AUDIT events must be queried with System Event Category = 2. Rules do not need this condition.
