Configuring External Integrations
This section describes how to configure FortiSIEM to integrate with external CMDB and ticket management systems and threat entity reputation systems. Currently out-of-the-box supported external systems include ticket management systems such as ServiceNow, Connectwise, Salesforce and Jira, and reputation systems, such as VirusTotal, RiskIQ and FortiGuard IOC lookup.
Configuring Ticketing System Integrations
FortiSIEM integration helps to create a two-way linkage between external ticketing/work flow systems like ServiceNow, ConnectWise and Salesforce. The integration can be for Incidents and CMDB.
This involves two steps.
- Create an integration.
- Attach the integration to an Incident Notification Policy or run the integration on a schedule.
Four types of integrations are supported:
- Incident Outbound Integration: This integration creates a ticket in an external ticketing system from FortiSIEM incidents. When an incident triggers in FortiSIEM, a ticket is opened in the external ticketing system. Currently, this out-of-the-box integration is supported for ServiceNow, ConnectWise, Salesforce and Jira.
- Incident Inbound Integration: This integration updates FortiSIEM incident ticket state from external system ticket states. Specifically, when a ticket is closed in the external ticketing system, the incident is cleared in FortiSIEM and the ticket status is marked closed to synchronize with the external ticketing system. Currently, this out-of-the-box integration is supported for ServiceNow, ConnectWise, Salesforce and Jira.
- CMDB Outbound Integration: This integration populates an external CMDB from FortiSIEM CMDB. When a device is added or updated in FortiSIEM CMDB, a device can be created in the external ticketing system. Currently, this out-of-the-box integration is supported for ServiceNow, ConnectWise and Salesforce.
- CMDB Inbound Integration: This integration populates FortiSIEM CMDB from an external CMDB. It works for any external CMDB.
Integration with other systems can be built using the API.
- ServiceNow Integration
- Jira Integration
- ConnectWise Integration
- Salesforce Integration
- CMDB Inbound Integration
ServiceNow Integration
ServiceNow SOAP Based Integration
Configuring ServiceNow for FortiSIEM Integration
- Log in to ServiceNow.
- For Service Provider Configurations, create Companies by creating Company Name.
-
For the integrations to work, FortiSIEM needs to modify certain ServiceNow database tables.
-
If you are using default integration, make sure that the FortiSIEM user account has the permissions specified, see Required Permissions for ServiceNow SOAP Integration.
-
if you are using custom integration, then sure that the FortiSIEM user account has the read/write permissions on the specific ServicNow tables and columns.
-
FortiSIEM Incident Schema
The following FortiSIEM Incident fields are available for integration.
|
FortiSIEM Incident Field |
Type |
Description |
Required for Custom Integration |
|---|---|---|---|
|
Incident ID |
64bit Integer |
Incident Id in FortiSIEM database. |
Optional for outbound |
|
Incident Title |
String |
Incident Title is a formatted string to capture Incident details and actors . |
Optional for outbound |
|
Rule Name |
String |
The name of the rule that triggered the Incident. |
Optional for outbound |
|
Rule Description |
String |
The description of the rule that triggered the Incident. |
Optional for outbound |
|
First Seen Time |
64bit Integer |
The first time an incident triggered in FortiSIEM. Format: Unix epoch timestamp (number of seconds that have elapsed since 00:00:00 UTC on 1 January 1970) |
Optional for outbound |
|
Last Seen Time |
64bit Integer |
The last time an incident triggered in FortiSIEM. Format: Unix epoch timestamp (number of seconds that have elapsed since 00:00:00 UTC on 1 January 1970) |
Optional for outbound |
|
Incident Severity |
32bit integer – values 1-10 |
Severity of the Incident. Severities are increasing meaning 1 is lowest and 10 is highest. |
Optional for outbound |
|
Incident Severity Category |
String – takes 3 values: LOW, MEDIUM, HIGH |
Incident severity categorized into 3 levels: LOW, MEDIUM, HIGH |
Optional for outbound |
|
Incident Source |
String |
Incident source attributes in comma separated attribute:Value format. Following attributes are included: srcIpAddr |
Optional for outbound |
|
Incident Target |
String |
Incident destination in comma separated attribute:Value format. Following attributes are included: destIpAddr, destName, hostIpAddr, hostname, user, targetUser |
Optional for outbound |
|
Incident Detail |
String |
Incident details in comma separated attribute:Value format. All attributes not included in Incident Source and Incident target are included in this attribute. |
Optional for outbound |
|
Triggering Attributes |
String |
List of attributes present in the incident. |
Optional for outbound |
|
Incident Count |
32bit integer |
Number of times the incident triggered. |
Optional for outbound |
|
Host Name |
String |
Host Name in incident. This is also present in Incident Target. |
Optional for outbound |
|
Incident Comment |
String |
Comments added by user or by a notification script. |
Optional for outbound |
|
Status |
32bit integer |
Incident Status: 0 means Active, 1 means System Cleared, 2 means User Cleared.
|
Optional for outbound |
|
Incident Resolution |
String |
Four values: Open, InProgress, TruePostive and FalsePositive |
Optional for outbound |
|
Rule Remediation Note |
String |
|
Optional for outbound |
|
External Ticket Id |
String |
ServiceNow Ticket Id |
Required for both Inbound and Outbound |
|
External Ticket State |
String |
ServiceNow Ticket State |
Required for Inbound and must have a value mapping for “Closed” |
|
External User |
String |
User who closed the Ticket in ServiceNow. |
Optional for outbound |
|
External Cleared Time |
String |
Time at which Incident cleared in ServiceNow. |
Required for Inbound |
There are two main requirements for a successful custom integration.
-
Outbound and Inbound – must have a mapping for External Ticket Id.
-
Inbound - External Ticket State must have value “Closed”.
-
Inbound - must have a mapping for External Cleared Time.
Incident Outbound Integration (Default)
In this integration, you can create tickets in ServiceNow when an Incident triggers in FortiSIEM. In the Default integration, FortiSIEM Incidents are written to the ServiceNow incident table. FortiSIEM incident attributes are mapped to ServiceNow incident table columns as follows.
|
FortiSIEM Incident Attribute |
ServiceNow Incident Table Column |
|---|---|
|
Incident Status |
work_notes |
|
Incident Name |
short_description |
|
Incident Comments (generated string containing few Incident attributes – see Step 1.4.k.) |
comments |
|
Organization Name |
company |
|
Incident Severity |
impact |
|
Incident Severity |
urgency |
Step 1: Create an Integration
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click New.
-
From the Integration Policy window, take the following steps.
-
From the Type drop-down list, select Incident.
-
From the Direction drop-down list, select Outbound.
-
From the Vendor drop-down list, select ServiceNow. When you select a vendor, an instance is created, with a unique name for the policy. For example, if you had two ServiceNow installations, each would have different instance names.
-
For Plugin Type, select Ticket.
-
For Plugin Name, a default Plugin Name is populated. Leave it as is. This is the Java code that implements the integration, including connecting to the external help desk systems and synching the CMDB elements.
-
In the Host/URL field, enter the login URL, for example,
https://vendor123.service-now.com. -
In the User Name field, enter the ServiceNow username login credential.
-
In the Password field, enter the ServiceNow password login credential.
-
Leave the ServiceNow Table Name attribute alone.
-
In the Description field, enter a description as to what the integration does. This is for display purposes only.
-
For Incident Comment, you can keep the default format shown in Step 1.k.i, or create your own, shown in Step 1.k.ii.
-
Default format :
[FortiSIEM]Incident Id:<val>;First seen time:<val>;Target IP:<val>;Incident Details:<val>;Mitre TechniqueId:<val>;Mitre Tactics:<val>; Description:<Rule Name> -
To create your own, click the Edit icon, and form a string by combining your own text and incident attributes by choosing from the Insert Content drop-down list. When done, click Save.
-
-
For Organization Mapping, click the Edit icon to create mappings between the Organizations in your FortiSIEM deployment and Company names in ServiceNow (created in Configuring ServiceNow for FortiSIEM Integration, Step 2).
-
For Run For, click the Edit icon, and choose the organizations for whom tickets will be created.
-
In the Max Incidents field, enter the maximum number of incidents you want to record.
-
Click Save.
-
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
Incident Inbound Integration (Default)
Using this integration, a FortiSIEM Incident can be programmatically cleared when a user closes the corresponding ticket in ServiceNow. In the default integration, the following fields from ServiceNow incident table are mapped to FortiSIEM incident fields.
|
ServiceNow Incident Table Column |
FortiSIEM Incident Field |
|---|---|
|
incident_state |
Incident Status |
|
Closed_code |
Incident Resolution |
|
Closed_by |
External User |
|
number |
External Ticket Id |
|
incident_state |
External Ticket Status |
Step 1: Create an Incident Inbound Integration
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click New.
-
From the Integration Policy window, take the following steps.
-
From the Type drop-down list, select Incident.
-
From the Direction drop-down list, select Inbound.
-
From the Vendor drop-down list, select ServiceNow. When you select a vendor, an instance is created, with a unique name for the policy. For example, if you had two ServiceNow installations, each would have different instance names.
-
For Plugin Type, select Ticket.
-
For Plugin Name, a default Plugin Name is populated. Leave it as is. This is the Java code that implements the integration, including connecting to the external help desk systems and synching the CMDB elements.
-
In the Host/URL field, enter the login URL, for example,
https://vendor123.service-now.com. -
In the User Name field, enter the ServiceNow username login credential.
-
In the Password field, enter the ServiceNow password login credential.
-
Leave the ServiceNow Table Name attribute alone.
-
In the Description field, enter a description as to what the integration does. This is for display purposes only.
-
For Content Mapping, do not make any edits. Keep the system defined one.
-
In the Time Window field, enter/select the number of hours for which incident states will be synched from ServiceNow. For example, if time window is set to 10 hours, then the states of incidents that occurred in the last 10 hours will be synched.
-
When done, click Save.
-
Step 2: Create an Incident Inbound Integration Schedule
This determines the schedule on which the inbound integration policy defined in Step 1: Create an Incident Inbound Integration will be run.
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click Schedule.
-
Click + to open the Integration Policy Schedules window.
-
From the Integration Policy column, select your integration policy and move it to the Selected column.
-
Under Time Range, configure your schedule by taking the following steps.
-
In the Start Time field, enter the start time of your schedule.
-
From the Local/UTC Timeand Region drop-down lists, configure the start time of the schedule.
-
-
Under Recurrence Pattern, configure the frequency.
-
Select Once, Minutely, Hourly, Daily, Weekly, or Monthly for the schedule's recurrence pattern. Depending on what is selected, configure the related date/time schedule attributes.
-
In the Start From field, enter the date which the schedule starts.
-
-
When done, click Save.
-
Incident Outbound Integration (Custom)
In this integration, you can create tickets in ServiceNow when an Incident triggers in FortiSIEM. You can choose your own ServiceNow table to map FortiSIEM Incidents to. Take the following steps to create a custom outbound integration.
Step 1: Create an Integration
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click New.
-
From the Integration Policy window, take the following steps.
-
From the Type drop-down list, select Incident.
-
From the Direction drop-down list, select Outbound.
-
From the Vendor drop-down list, select ServiceNow. When you select a vendor, an instance is created, with a unique name for the policy. For example, if you had two ServiceNow installations, each would have different instance names.
-
For Plugin Type, select Ticket.
-
For Plugin Name, a default Plugin Name is populated. Leave it as is. This is the Java code that implements the integration, including connecting to the external help desk systems and synching the CMDB elements. For other vendors, you must create your own plugin and enter the plugin name here.
-
In the Host/URL field, enter the login URL, for example,
https://vendor123.service-now.com. -
In the User Name field, enter the ServiceNow username login credential.
-
In the Password field, enter the ServiceNow password login credential.
-
In the ServiceNow Table Name field, enter the custom ServiceNow table
-
In the Description field, enter a description as to what the integration does. This is for display purposes only.
-
For Incident Comment, you can keep the default format shown in Step 1.k.i, or create your own, shown in Step 1.k.ii.
-
Default format :
[FortiSIEM]Incident Id:<val>;First seen time:<val>;Target IP:<val>;Incident Details:<val>;Mitre TechniqueId:<val>;Mitre Tactics:<val>; Description:<Rule Name> -
To create your own, click the Edit icon, and form a string by combining your own text and incident attributes by choosing from the Insert Content drop-down list. When done, click Save.
-
-
For Organization Mapping, click the Edit icon to create mappings between the Organizations in your FortiSIEM deployment and Company names in ServiceNow (created in Configuring ServiceNow for FortiSIEM Integration, Step 2).
-
For Run For, click the Edit icon, and choose the organizations for whom tickets will be created.
-
For Content Mapping, click the Edit icon to define mappings between FortiSIEM Incident fields and ServiceNow custom table columns.
-
Select the Field Mappings dialog box and click +.
Note: To delete a Field Mapping, select the entry and click -. To edit a Field Mapping, click the Edit icon.
-
From the FortiSIEM Incident Field drop-down list, select a FortiSIEM Incident field.
-
From the ServiceNow Field drop-down list, select a mapped ServiceNow field. Note that the menu is populated from the table in step 4.i.
-
Select the Value Mappings dialog box and click + to enter Value Mappings if you want the values for a specific field to be transformed. A standard example is Severity, where FortiSIEM Incident Severity 1-> 4 may be mapped to Low, 5-8 as Medium and 9-10 as High.
-
From Field, select the ServiceNow Field whose values need to be transformed.
-
In the From field, select the value that FortiSIEM generates.
-
In the To field, select the value that you want ServiceNow to store.
-
When done, click Save.
-
-
In the Max Incidents field, enter the maximum number of incidents you want to record.
-
Click Save.
-
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Note: In the default Outbound integration, Incident updates are recorded in the comments field. However, in the custom integration, Incident updates are not reflected in ServiceNow.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
Incident Inbound Integration (Custom)
In this integration, you can clear tickets in FortiSIEM when a user closes the corresponding ServiceNow ticket. You can choose your own ServiceNow table to update the following FortiSIEM Incident fields:
-
External Ticket Id
-
Incident Status
-
Incident Resolution
-
External User
-
External Ticket State
Step 1: Create an Incident Inbound Integration
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click New.
-
From the Integration Policy window, take the following steps.
-
From the Type drop-down list, select Incident.
-
From the Direction drop-down list, select Inbound.
-
From the Vendor drop-down list, select ServiceNow. When you select a vendor, an instance is created, with a unique name for the policy. For example, if you had two ServiceNow installations, each would have different instance names.
-
For Plugin Type, select Ticket.
-
For Plugin Name, a default Plugin Name is populated. Leave it as is. This is the Java code that implements the integration, including connecting to the external help desk systems and synching the CMDB elements.
-
In the Host/URL field, enter the login URL, for example,
https://vendor123.service-now.com. -
In the User Name field, enter the ServiceNow username login credential.
-
In the Password field, enter the ServiceNow password login credential.
-
For the ServiceNow Table Name, choose your custom ServiceNow table.
-
In the Description field, enter a description as to what the integration does. This is for display purposes only.
-
For Content Mapping, click the Edit icon to define mappings between FortiSIEM Incident fields and ServiceNow custom table columns.
-
Select the Field Mappings dialog box and click +.
Note: To delete a Field Mapping, select the entry and click -. To edit a Field Mapping, click the Edit icon.
-
From the FortiSIEM Incident Field drop-down list, select a FortiSIEM Incident field.
-
From the ServiceNow Field drop-down list, select a mapped ServiceNow field. Note that the menu is populated from the table in step 4.i.
-
Select the Value Mappings dialog box and click + to enter Value Mappings if you want the values for a specific field to be transformed. For the Incident Inbound Integration to function, we need a mapping to the “Closed” value of FortiSIEM Incident Status field. This allows FortiSIEM to close an Incident.
-
From Field, select the ServiceNow Field whose values need to be transformed.
-
In the From field, select the value that FortiSIEM generates.
-
In the To field, select the value that you want ServiceNow to store.
-
When done, click Save.
-
-
In the Time Window field, enter/select the number of hours for which incident states will be synched from ServiceNow. For example, if time window is set to 10 hours, then the states of incidents that occurred in the last 10 hours will be synched.
-
When done, click Save.
Step 2: Create an Incident Inbound Integration Schedule
This determines the schedule on which the inbound integration policy defined in Step 1: Create an Incident Inbound Integration will be run.
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click Schedule.
-
Click + to open the Integration Policy Schedules window.
-
From the Integration Policy column, select your integration policy and move it to the Selected column.
-
Under Time Range, configure your schedule by taking the following steps.
-
In the Start Time field, enter the start time of your schedule.
-
From the Local/UTC Timeand Region drop-down lists, configure the start time of the schedule.
-
-
Under Recurrence Pattern, configure the frequency.
-
Select Once, Minutely, Hourly, Daily, Weekly, or Monthly for the schedule's recurrence pattern. Depending on what is selected, configure the related date/time schedule attributes.
-
In the Start From field, enter the date which the schedule starts.
-
-
When done, click Save.
-
-
CMDB Outbound Integration (Default)
CMDB Outbound Integration populates an external CMDB from FortiSIEM’s own CMDB. Built in integrations are available for ServiceNow.
Step 1: Create a CMDB Outbound integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Device.
- For Direction, select Outbound.
- For Vendor, select the vendor of the system you want to connect to. ServiceNow is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had 2 ServiceNow installations, each would have different Instance names.
- A default Plugin Name is populated - this is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for ServiceNow. For other vendors, you have to create your own plugin and type in the plugin name here.
- For Host/URL, enter the host name or URL of the external system. For ServiceNow, select the login URL
- For User Name and Password, enter a user name and password that the system can use to authenticate with the external system. For ServiceNow, select the login credentials.
- In Attribute Mapping, specify the mapping of attributes to resources.
- For Organization Mapping, click Edit to create mappings between the organizations in your FortiSIEM deployment and the names of the organization in the external system. For ServiceNow, select the Company names as in Configuring ServiceNow for FortiSIEM Integration, Step 2.
- For Run For, choose the organizations for whom tickets will be created.
- For Groups, select the FortiSIEM CMDB Groups whose member devices would be synched to external CMDB.
- Select Run after Discovery if you want this export to take place after you have run discovery in your system. This is the only way to push automatic changes from FortiSIEM to the external system.
- Enter the Maximum number of devices to send to the external system.
- Click Save.
Step 2: Create a CMDB Outbound integration schedule
Updating external CMDB automatically after FortiSIEM discovery:
- Create an integration policy.
- Make sure Run after Discovery is checked.
- Click Save.
Updating external CMDB on a schedule:
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click Schedule and then click +.
- Select the integration policies.
- Select a schedule.
Updating external CMDB on-demand (one-time):
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Select a specific integration policy and click Run.
Example Custom Integration
This section provides a sample integration.
There are a few main requirements for a successful custom integration
-
Outbound and Inbound – must have a mapping for External Ticket Id
-
Inbound - External Ticket State must have value “Closed”
-
Inbound - must have a mapping for External Cleared Time
Follow these steps:
Step 1. From ServiceNow, take the following steps to create a ServiceNow Table.
-
Login to ServiceNow.
-
From the left pane, navigate to System Definitions > Tables.
-
Next to the heading Tables, click New to create a table.
-
In the Label field, enter a label. Here, we can use "fsm demo". The Name field will be automatically populated. Keep this name recorded, as it will be needed later.
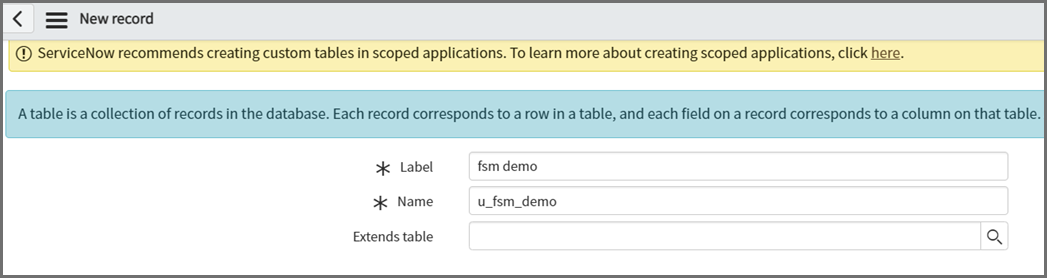
-
Under Controls, check the Auto-number checkbox. This is required to map the External Ticket Id.
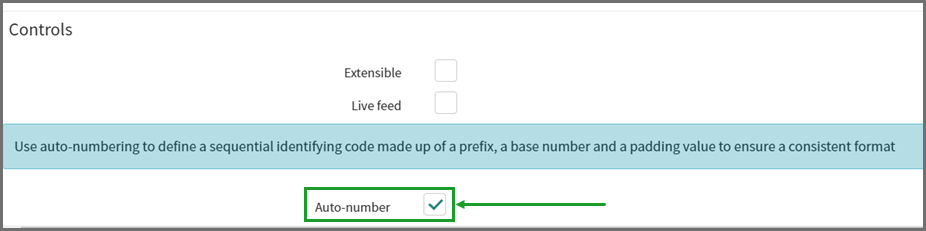
-
Under Application Access, check the following checkboxes.
-
Can read
-
Can create
-
Can update
-
Can delete
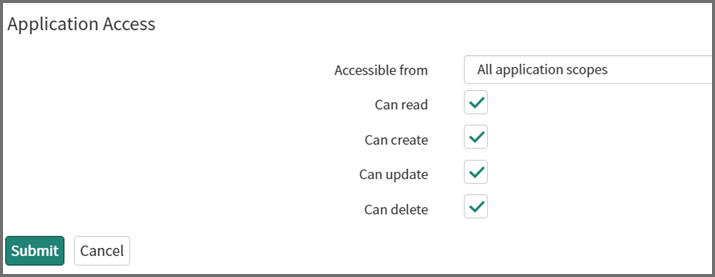
-
-
Click Submit.
A ServiceNow table has now been created.
-
-
Next to the heading Table Columns, click New to create a table column.
-
Create your column/mappings and ensure that Type is set correctly (See FortiSIEM Incident Schema for the correct Types). For this example, we use the following:
Type: String
Column label: ticketnumber
Note: For External Ticket ID
Max length: 256
-
Type: String
Column label: externalcleartime
Note: For External Cleared Time
Max length: 256
-
Type: String
-
Column label: incident_status
Note: For Ticket Status
-
Max length: 256
-
Configure any additional mappings necessary for your ServiceNow table.
To create a drop-down list, navigate to Choice List Specification, and from the Choice drop-down list, make a selection. To configure what will appear in your drop-down list, click the Advanced view link, and under Choices, click New to add items to appear in your drop-down list.
-
-
When done, click Submit.
Step 2. From FortiSIEM, take the following steps to create Incident Outbound Integration Policy.
-
Login to FortiSIEM.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click New to create an Integration Policy, and take the following steps.
-
From the Type drop-down list, select Incident.
-
From the Direction drop-down list, select Outbound.
-
From the Vendor drop-down list, select ServiceNow.
-
In the Host/URL field, enter the ServiceNow URL being used.
-
In the User Name field, enter the ServiceNow username credential.
-
In the Password and Confirm Password field, enter the password associated with the ServiceNow User Name account.
-
In the ServiceNow Table Name field, enter the name of the ServiceNow table that was set up during the ServiceNow table creation.
-
In the Content Mapping row, click the Edit icon.
-
In the Integration Policy > Incident Outbound Content Mapping window, take the following steps.
-
From the FortiSIEM Incident Field drop-down list, select External Ticket Id.
-
From the ServiceNow Field drop-down list, select the "ticketnumber" mapping.
-
From the FortiSIEM Incident Field drop-down list, select External Ticket State.
-
From the ServiceNow Field drop-down list, select the "externalcleartime" mapping.
A more complicated custom mapping is provided in the following screenshot.
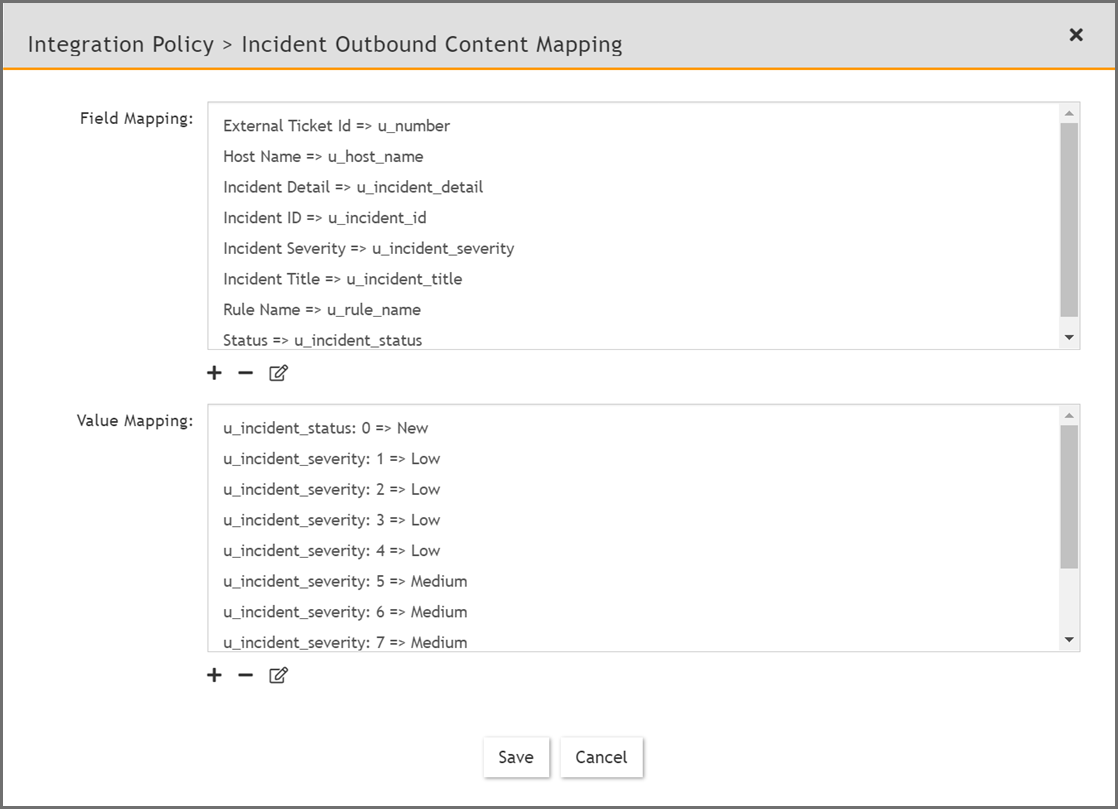
-
Click Save.
-
-
Click Save.
Your Outbound Integration Policy has been created.
-
Step 3. From FortiSIEM, take the following steps to create Incident Inbound Integration Policy.
-
Click New to create an Integration Policy, and take the following steps.
-
From the Type drop-down list, select Incident.
-
From the Direction drop-down list, select Inbound.
-
From the Vendor drop-down list, select ServiceNow.
-
In the Host/URL field, enter the ServiceNow URL being used.
-
In the User Name field, enter the ServiceNow username credential.
-
In the Password and Confirm Password field, enter the password associated with the ServiceNow User Name account.
-
In the ServiceNow Table Name field, enter the name of the ServiceNow table that was set up during the ServiceNow table creation.
-
In the Content Mapping row, click the Edit icon.
-
In the Integration Policy > Incident Outbound Content Mapping window, take the following steps.
-
From the FortiSIEM Incident Field drop-down list, select from External Cleared Time, External Ticket Id, External Ticket State, External User, or Incident Resolution.
Note: External Ticket ID and External Ticket State are required.
-
From the ServiceNow Field drop-down list, select the corresponding column.
-
Click Save.
-
Repeat i.-iii. for any additional mappings. Proceed to v. when done with incident mapping.
-
In Value Mapping, click + .
-
In the Field drop-down list, select the ServiceNow "external ticket state".
-
In the From field, enter "Closed".
The value mapping should appear similar to the following example:
u_incident_status: Closed => closed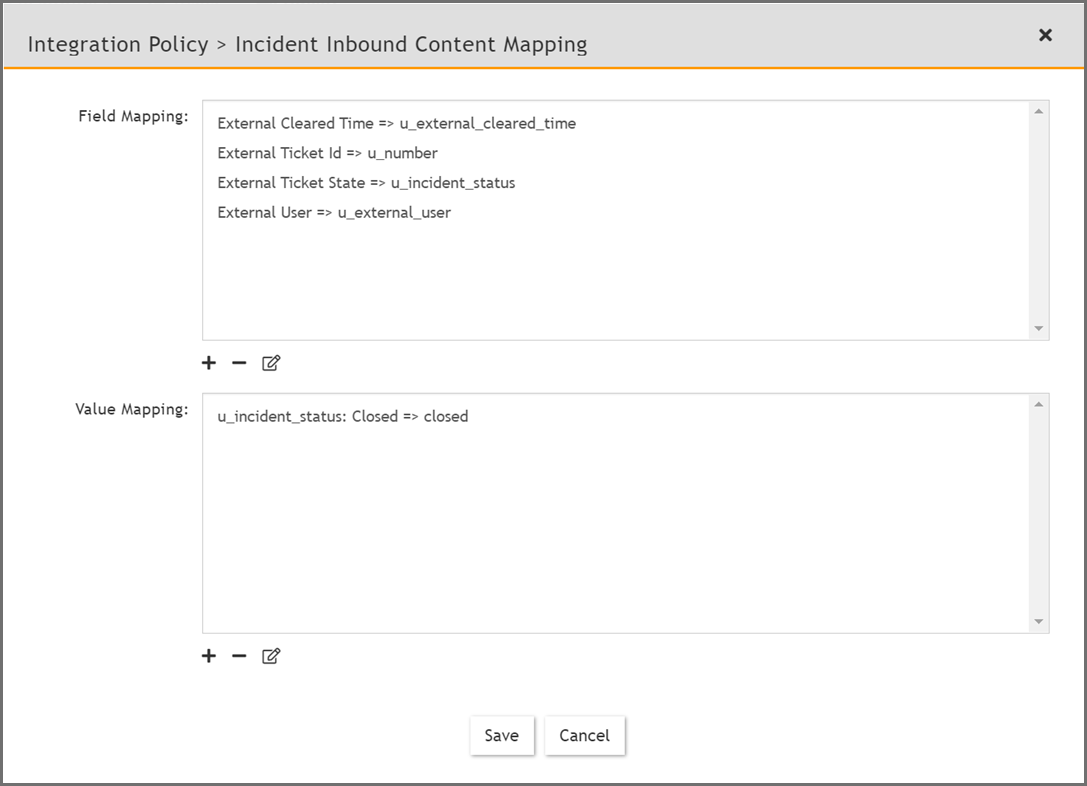
-
Click Save.
-
-
Click Save.
Your Inbound Integration Policy has been created. Now, if you close an incident/ticket in ServiceNow, and run the inbound integration in FortiSIEM, the incident/ticket will also be closed.
-
Step 4. Run Outbound Integration
-
Confirm you are on the External Integration page. (ADMIN > Settings > General > External Integration)
-
Select the Outbound Integration you created.
-
Click Run.
Note: The maximum number of incidents can be configured by changing the value of the Max Incidents field in your Outbound Integration Notification policy .
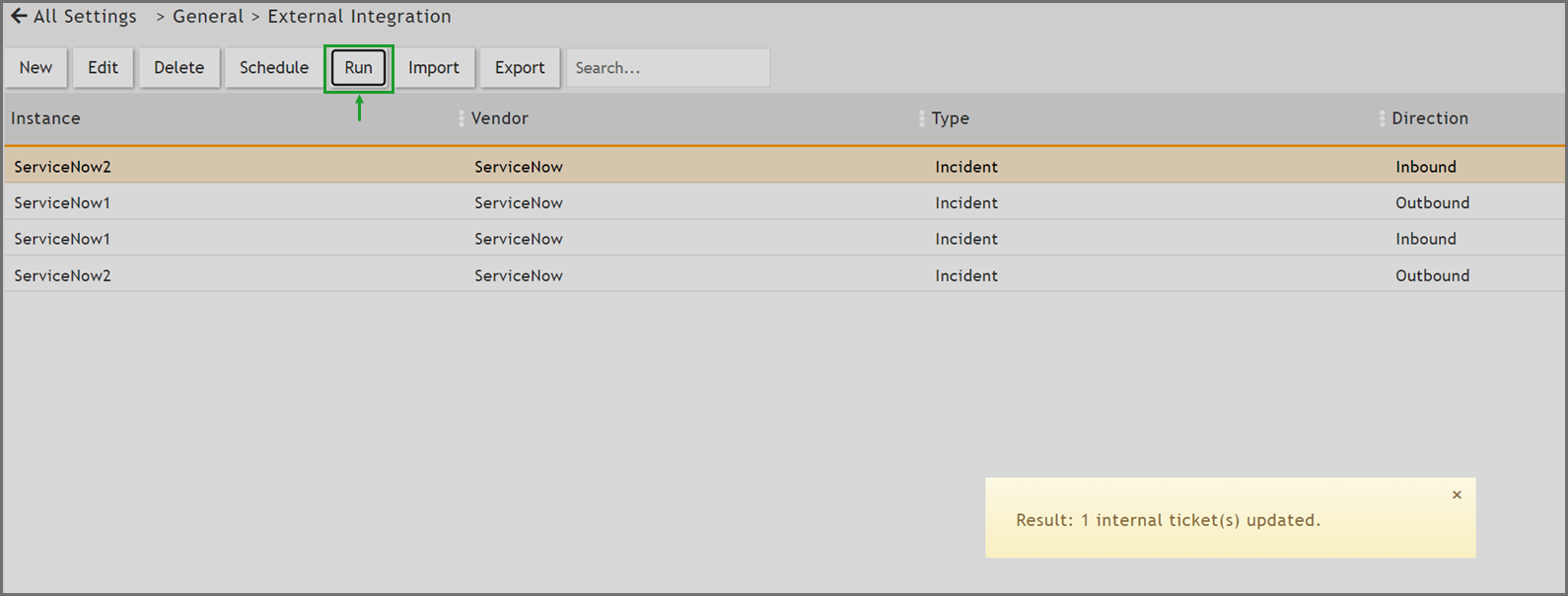
-
Click Yes to confirm.
Step 5. Run Inbound Integration
-
Confirm you are on the External Integration page. (ADMIN > Settings > General > External Integration)
-
Select the Inbound Integration you created.
-
Click Run.
Note: You can verify the closing of an incident/ticket by checking the External Ticket State column.
Jira Integration
- Configuring Jira for FortiSIEM Integration
- Jira Incident Outbound Integration
- Jira Incident Inbound Integration
Configuring Jira for FortiSIEM Integration
Before configuring Jira, you must log in to your Jira account and create an API Key. Follow these steps.
- Log in to your Jira account.
- Create an API Key.
- Use the GUI user name and API Key in FortiSIEM.
Jira Incident Outbound Integration
Jira outbound integration allows a user to map FortiSIEM fields to Jira ticket fields and to create incidents in Jira. When the integration runs, FortiSIEM looks for incidents that match the mappings and creates a ticket in the Jira system.
To create an outbound integration, follow these steps.
Step 1: Create an Integration
- Go to Admin > Settings > General > External Integration.
- Click New to create a new integration or Edit to modify an existing integration.
- In the Integration Policy dialog box, provide the following values:
- Type: select Incident.
- Direction: select Outbound.
- Vendor: select Jira.
- Instance: enter an instance name or accept the default.
- Plugin Name: is pre-populated with the name of the Jira integration class:
com.accelops.phoenix.jira.JiraTicketIntegration. - Host/URL, enter the URL of the Jira provider, for example,
https://<customer>.atlassian.net. - Username and Password, enter your Jira user name and password.
- Click the edit icon next to Field Mapping.
- In the Field Mapping dialog box, provide the following values:
- Project: enter a name for the project
- Issue Type: select Event.
- The Summary: field is pre-populated with the Incident Rule Name (
$ruleName). - For Description: click the edit icon to build the expression for the Jira issue description. The drop-down list contains FortiSIEM fields that can be mapped to.
- The Priority: field is pre-populated with Incident Severity Category (
$incident_severityCat).
- Create mappings between Jira fields and FortiSIEM fields by clicking New.
Select Jira fields from the upper drop-down list and match them with corresponding FortiSIEM fields in the lower drop-down list. - Click Save when you are finished mapping fileds. The mappings are reflected in the table in the Field Mapping dialog box.
Note: Click Cancel to dismiss the Mapping Fields dialog box.
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
Jira Incident Inbound Integration
Jira inbound integration allows a user to close a ticket in FortiSIEM if the ticket is closed in Jira.
To create an inbound integration, follow these steps.
Step 1: Create an Integration
- Go to Admin > Settings > General > External Integration.
- Click New to create a new integration or Edit to modify an existing integration.
- In the Integration Policy dialog box, provide the following values:
- Type: select Incident.
- Direction: select Inbound.
- Vendor: select Jira.
- Instance: enter an instance name or accept the default.
- Plugin Name: is pre-populated with the name of the Jira integration class:
com.accelops.phoenix.jira.JiraTicketIntegration. - Host/URL, enter the URL of the Jira provider, for example,
https://<customer>.atlassian.net. - Username and Password, enter your Jira user name and password.
- Description: enter an optional description of the integration.
- Time Window: enter the number of hours for which incident states will be synched. For example, if time windows is set to 10 hours, the states of incidents that occurred in the last 10 hours will be synched.
- Click the edit icon next to Field Mapping.
- In the Field Mapping dialog box, provide the following values:
- Project: enter a name for the project.
- Issue Type: select Event.
- The Summary: field is pre-populated with the Incident Rule Name (
$ruleName). - For Description: click the edit icon to build the expression for the Jira issue description. The drop-down list contains FortiSIEM fields that can be mapped to.
- The Priority: field is pre-populated with Incident Severity Category (
$incident_severityCat).
- Create mappings between Jira fields and FortiSIEM fields by clicking New.
Select Jira fields from the upper drop-down list and match them with corresponding FortiSIEM fields in the lower drop-down list.
-
Click Save when you are finished mapping fileds. The mappings are reflected in the table in the Field Mapping dialog box.
Note: Click Cancel to dismiss the Mapping Fields dialog box.
Step 2: Create an Incident Inbound Integration Schedule
This determines the schedule on which the inbound integration policy defined in Step 1: Create an Incident Inbound Integration will be run.
-
Log into your Supervisor node with administrator credentials.
-
Navigate to ADMIN > Settings > General > External Integration.
-
Click Schedule.
-
Click + to open the Integration Policy Schedules window.
-
From the Integration Policy column, select your integration policy and move it to the Selected column.
-
Under Time Range, configure your schedule by taking the following steps.
-
In the Start Time field, enter the start time of your schedule.
-
From the Local/UTC Timeand Region drop-down lists, configure the start time of the schedule.
-
-
Under Recurrence Pattern, configure the frequency.
-
Select Once, Minutely, Hourly, Daily, Weekly, or Monthly for the schedule's recurrence pattern. Depending on what is selected, configure the related date/time schedule attributes.
-
In the Start From field, enter the date which the schedule starts.
-
-
When done, click Save.
-
ConnectWise Integration
- Adding a Client ID for ConnectWise Integration
- Configuring ConnectWise for FortiSIEM Integration
- ConnectWise Incident Outbound Integration
- ConnectWise Incident Inbound Integration
- ConnectWise CMDB Outbound Integration
Adding a Client ID for ConnectWise Integration
ConnectWise has recently changed their policy and requires that vendors create a client ID in order to integrate with FortiSIEM. Due to this change and restriction from ConnectWise, Fortinet has published a public client ID in order to allow clients to integrate with ConnectWise. This Client ID is 1a7ed749-47a1-4d3e-94b0-696288a1140f.
Note: A ConnectWise working account is required before integration can occur.
To add this client ID for ConnectWise, take the following steps.
- Go to ADMIN > Settings >General > External Integration.
- Click New to create a new Integration Policy or select an existing Integration Policy and click Edit.
- From the Vendor drop-down list, select ConnectWise.
- In the Client ID field, paste the following Client ID:
1a7ed749-47a1-4d3e-94b0-696288a1140f - Make any necessary configuration changes.
- Click Save.
Configuring ConnectWise for FortiSIEM Integration
- Log in to ConnectWise MANAGE.
- Go to Setup Tables > Integrator Login List.
- Create a new Integrator Login for FortiSIEM:
- Enter Username.
- Enter Password.
- Set Access Level to Records created by integrator.
- Enable Service Ticket API for Incident Integration.
- Enable Configure API for CMDB Integration.
- For Service Provider Configurations, create Companies by creating:
- Company Name
- Company ID
ConnectWise Incident Outbound Integration
Step 1: Create an Integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Incident.
- For Direction, select Outbound.
- For Vendor, select the vendor of the system you want to connect to. ConnectWise is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had two ConnectWise installations, each would have different Instance names.
- Choose whether the Plugin Type is SOAP or REST.
Note: The SOAP method is deprecated, so you should select REST. - A default Plugin Name is populated - this is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for ConnectWise. For other vendors, you must create your own plugin and enter the plugin name here.
- For Host/URL, enter the host name or URL of the external system. For ConnectWise, enter the login URL of the ConnectWise instance. Make sure to include the https:// prefix.
Example:https://my.login.test - For Company, enter the company name that you use when logging in to ConnectWise Manage. Do not use the company name from within ConnectWise.

- If you chose SOAP as Plugin Type, enter a User Name, Password, and Client ID that the system can use to authenticate with the external system. For ConnectWise, select the credentials created in Configuring ConnectWise for FortiSIEM Integration, Step 3. If you chose REST, enter the Public Key and the Private Key and Client ID.
Note: The Client ID is 1a7ed749-47a1-4d3e-94b0-696288a1140f. See Adding a Client ID for ConnectWise Integration for more information.
To get your Public Key and Private Key from ConnectWise, login and take the following steps.- In the upper right part of the window, click your account name to open a drop-down list, and select My Account.
- Click the API Keys tab, and create your private and public keys, keeping a record of what they are so you can enter them in the FortiSIEM configuration in the Private Key and Public Key fields.
- For Incidents Comments Template, specify the formatting using the incident fields.
- For Organization Mapping, click Edit to create mappings between the organizations in your FortiSIEM deployment and the names of the organization in the external system. In ConnectWise, locate and use the Company ID field under Company Details in ConnectWise for the FortiSIEM Organization Mapping, NOT the company name.
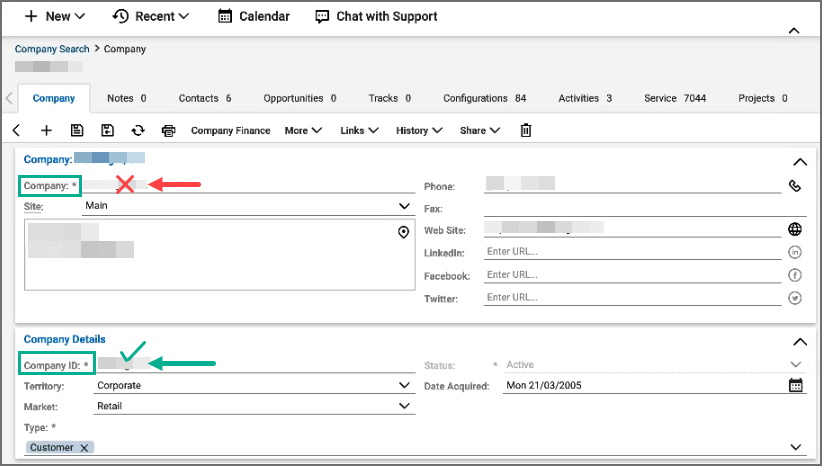
- For Run For, choose the organizations for whom tickets will be created.
- Enter the Max Incidents to be recorded.
Note: The default number for Max Incidents is 50. When running this the first time with the default number, you may encounter a 502 proxy error due to the initial volume of incidents being requested. In this situation, you can change the Max Incidents value to 5 or 10 initially, then change it after running the ConnectWise integration once. - Click Save.
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
ConnectWise Incident Inbound Integration
This updates the FortiSIEM incident state and clears the incident when the incident is cleared in the external help desk system. Built-in integrations are available for ConnectWise.
The steps are:
- Create an Incident Inbound integration schedule.
- Create a schedule for automatically running the Incident Inbound integration.
This will update the FortiSIEM incident inbound integration schedule and clears the incident when the incident is cleared in the external help desk system.
Step 1: Create an Incident Inbound integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Incident.
- For Direction, select Inbound.
- For Vendor, select the vendor of the system you want to connect to. ConnectWise is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had two ConnectWise installations, each would have different Instance names.
- Choose whether the Plugin Type is SOAP or REST.
- A default Plugin Name is populated. This is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for ConnectWise. For other vendors, you must create your own plugin and enter the plugin name here.
- For Host/URL, enter the host name or URL of the external system (see section Configuring external helpdesk systems). For ConnectWise, select the login URL.
- If you chose SOAP as Plugin Type, enter a User Name, Password, and Client ID that the system can use to authenticate with the external system. For ConnectWise, select the credentials created in Configuring ConnectWise for FortiSIEM Integration, Step 3. If you chose REST, enter the Public Key, the Private Key, and Client ID.
- For Time Window, select the number of hours for which incident states will be synched. For example, if time windows is set to 10 hours, the states of incidents that occurred in the last 10 hours will be synched.
- Click Save.
Step 2: Create an Incident Inbound integration schedule
This will update FortiSIEM following incident fields when ticket state is updated in the external ticketing system.
- External Ticket State
- Ticket State
- External Cleared Time
- External Resolve Time
Note: FortiSIEM does not support custom mapping, only "new" and "closed", and the incident resolution is not updated.
Follow these steps.
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click Schedule and then click +.
- Select the integration policy.
- Select a schedule.
ConnectWise CMDB Outbound Integration
CMDB Outbound Integration populates an external CMDB from FortiSIEM’s own CMDB. Built in integrations are available for ServiceNow, ConnectWise and Salesforce.
Step 1: Create a CMDB Outbound integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Device.
- For Direction, select Outbound.
- For Vendor, select the vendor of the system you want to connect to. ConnectWise is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had two ConnectWise installations, each would have different Instance names.
- Choose whether the Plugin Type is SOAP or REST.
- A default Plugin Name is populated - this is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for ConnectWise. For other vendors, you have to create your own plugin and type in the plugin name here.
- For Host/URL, enter the host name or URL of the external system. For ConnectWise, select the login URL.
- If you chose SOAP as Plugin Type, enter a User Name, Password, and Client ID that the system can use to authenticate with the external system. For ConnectWise, select the credentials created in Configuring ConnectWise for FortiSIEM Integration, Step 3. If you chose REST, enter the Public Key and the Private Key in addition to the User Name, Password, and Client ID.
- For Organization Mapping, click Edit to create mappings between the organizations in your FortiSIEM deployment and the names of the organization in the external system. For ConnectWise, select the Company name in Configuring ConnectWise for FortiSIEM Integration, Step 4.
- For Run For, choose the organizations for whom tickets will be created.
- For ConnectWise, it is possible to define a Content Mapping.
- Enter Column Mapping values:
- To add a new mapping, click the + button.
- Choose FortiSIEM CMDB attribute as the Source Column.
- Enter external (ConnectWise) attribute as the Destination Column.
- Specify Default Mapped Value as the value assigned to the Destination Column if the Source Column is not found in Data Mapping definitions.
- Select Put to a Question is the Destination Column is a custom column in ConnectWise.
- Enter Data Mapping values:
- Choose the (Destination) Column Name.
- Enter From as the value in FortiSIEM.
- Enter To as the value in ConnectWise.
- Enter Column Mapping values:
- For Groups, select the FortiSIEM CMDB Groups whose member devices would be synched to external CMDB.
- Select Run after Discovery if you want this export to take place after you have run discovery in your system. This is the only way to push automatic changes from FortiSIEM to the external system.
- Enter the Max Devices: the number of devices to send to the external system.
- Click Save.
Step 2: Create a CMDB Outbound integration schedule
Updating external CMDB automatically after FortiSIEM discovery:
- Create an integration policy.
- Make sure Run after Discovery is checked.
- Click Save.
Updating external CMDB on a schedule:
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click Schedule and then click +.
- Select the integration policies.
- Select a schedule.
Updating external CMDB on-demand (one-time):
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Select a specific integration policy and click Run.
Salesforce Integration
- Configuring Salesforce for FortiSIEM Integration
- Salesforce Incident Outbound Integration
- Salesforce Incident Inbound Integration
- Salesforce CMDB Outbound Integration
Configuring Salesforce for FortiSIEM Integration
- Log in to Salesforce.
- Create a custom domain.
- For Service Provider Configurations, create Service App > Accounts.
FortiSIEM will use the Account Name.
Salesforce Incident Outbound Integration
Step 1: Create an Integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Incident.
- For Direction, select Outbound.
- For Vendor, select the vendor of the system you want to connect to. Salesforce is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had two Salesforce installations, each would have different Instance names.
- A default Plugin Name is populated - this is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for Salesforce. For other vendors, you must create your own plugin and enter the plugin name here.
- For Host/URL, enter the host name or URL of the external system. For Salesforce:
- Log in to Salesforce.
- Go to Setup > Settings.
- Use the Custom URL under My Domain, typically it is
xyz.my.salesforce.com
- For User Name and Password, enter a user name and password that the system can use to authenticate with the external system.
- For Salesforce, enter the login credentials.
- For Security Token, enter the security token from Salesforce. If you do not have your security token information, you can get this by taking the following steps.
- Log in to Salesforce.
- At <your name>, click the drop-down list and navigate to Setup > Personal Setup > My Personal Information.
- Click Reset My Security Token to get Salesforce to email your security token.
- For Incidents Comments Template, specify the formatting of the incident fields.
- For Organization Mapping, click the Edit icon to take you to the Integration Policy > Org Mapping window. Here, you can create mappings between the organizations in your FortiSIEM deployment and the names of the organization in the external system. For Salesforce, to get your account name, take the following steps in Salesforce:
Go to Service App > Accounts.
- Use Account Name.
- In FortiSIEM, at the Integration Policy > Org Mapping window, enter the Account Name in the Default field.
Note: You can choose to provide an organization name from FortiSIEM in the Default field.
- For Run For, choose the organizations for whom tickets will be created.
- In the Max Incidents field, enter the maximum number of incidents you want recorded.
- Click Save.
- Click Run to confirm the integration. If you receive an "...unable to find valid certification path to requested target", you need to upload a certificate to FortiSIEM.
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
Salesforce Incident Inbound Integration
This updates the FortiSIEM incident state and clears the incident when the incident is cleared in the external help desk system. Built-in integrations are available for Salesforce.
The steps are:
- Create an Incident Inbound integration schedule.
- Create a schedule for automatically running the Incident Inbound integration.
This will update the FortiSIEM incident inbound integration schedule and clears the incident when the incident is cleared in the external help desk system.
Step 1: Create an Incident Inbound integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Incident.
- For Direction, select Inbound.
- For Vendor, select the vendor of the system you want to connect to. Salesforce is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had two Salesforce installations, each would have different Instance names.
- A default Plugin Name is populated. This is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for Salesforce. For other vendors, you must create your own plugin and enter the plugin name here.
- For Host/URL, enter the host name or URL of the external system. For Salesforce:
Log in to Salesforce.
- Go to Setup > Settings.
- Use the custom URL under My Domain – typically it is
xyz.my.salesforce.com.
- For User Name and Password, enter a user name and password that the system can use to authenticate with the external system. For Salesforce, select the login credentials.
- For Time Window, select the number of hours for which incident states will be synched. For example, if time windows is set to 10 hours, the states of incidents that occurred in the last 10 hours will be synched.
- Click Save.
Step 2: Create an Incident Inbound integration schedule
This will update FortiSIEM following incident fields when ticket state is updated in the external ticketing system.
- External Ticket State
- Ticket State
- External Cleared Time
- External Resolve Time
Follow these steps.
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click Schedule and then click +.
- Select the integration policy.
- Select a schedule.
Salesforce CMDB Outbound Integration
CMDB Outbound Integration populates an external CMDB from FortiSIEM’s own CMDB. Built in integrations are available for Salesforce.
Step 1: Create a CMDB Outbound integration
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Device.
- For Direction, select Outbound.
- For Vendor, select the vendor of the system you want to connect to. Salesforce is supported out of the box.
When you select the Vendor:- An Instance is created - this is the unique name for this policy. For example if you had 2 Salesforce installations, each would have different Instance names.
- A default Plugin Name is populated - this is the Java code that implements the integration including connecting to the external help desk systems and synching the CMDB elements. The plugin is automatically populated for Salesforce . For other vendors, you have to create your own plugin and type in the plugin name here.
- For Host/URL, enter the host name or URL of the external system. For Salesforce:
- Log in to Salesforce.
- Go to Setup > Settings.
- Use the Custom URL under My Domain, typically it is
xyz.my.salesforce.com.
- For User Name and Password, enter a user name and password that the system can use to authenticate with the external system. For Salesforce, select the login credentials.
- Enter the Maximum number of devices to send to the external system.
- For Organization Mapping, click Edit to create mappings between the organizations in your FortiSIEM deployment and the names of the organization in the external system. For Salesforce:
Go to Service App > Accounts.
- Use Account Name.
- For Run For, choose the organizations for whom tickets will be created.
- For Groups, select the FortiSIEM CMDB Groups whose member devices would be synched to external CMDB.
- Select Run after Discovery if you want this export to take place after you have run discovery in your system. This is the only way to push automatic changes from FortiSIEM to the external system.
- Click Save.
Step 2: Create a CMDB Outbound integration schedule
Updating external CMDB automatically after FortiSIEM discovery:
- Create an integration policy.
- Make sure Run after Discovery is checked.
- Click Save.
Updating external CMDB on a schedule:
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click Schedule and then click +.
- Select the integration policies.
- Select a schedule.
Updating external CMDB on-demand (one-time):
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Select a specific integration policy and click Run.
CMDB Inbound Integration
CMDB Inbound Integration populates FortiSIEM CMDB from an external CMDB.
Step 1: Create a CMDB Inbound integration
You must create a CSV file for mapping the contents of the external database to a location on your FortiSIEM Supervisor, which will be periodically updated based on the schedule you set.
- Log into your Supervisor node with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click New.
- For Type, select Device.
- For Direction, select Inbound.
- Enter the File Path to the CSV file.
- For Content Mapping, click the edit icon.
- For Column Mapping, click + and enter the mapping between columns in the Source CSV file and the Destination CMDB.
- Enter Source CSV column Name for Source Column
- Check Create Property if it Does not Exist to create the new attribute in FortiSIEM if it does not exist
- Enter a name for the Destination Column of the property from the drop-down list.
- Select Overwrite Existing Value if the property exists in the CMDB, but you want to overwrite it's current value.
- If the property exists in the CMDB, select FortiSIEM CMDB attribute for Destination Column.
- Select Overwrite Existing Value if the property exists in the CMDB, but you want to overwrite its current value.
- Click OK.
- For Data Mapping, click + and enter the mapping between data values in the external system and the destination CMDB.
For example, if you wanted to change all instances of California in the entries for the State attribute in the external system to CA in the destination CMDB, you would select the State attribute, enter California for From. and CA for To.
- For Column Mapping, click + and enter the mapping between columns in the Source CSV file and the Destination CMDB.
- In Attribute Mapping, map attributes to resources.
- Click OK.
- Click Save.
Step 2: Create a CMDB Inbound integration schedule
Updating FortiSIEM CMDB on a schedule:
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Click Schedule and then click +.
- Select the integration policies.
- Select a schedule.
Updating FortiSIEM CMDB on-demand (one-time):
- Log into your FortiSIEM Supervisor with administrator credentials.
- Go to ADMIN > Settings > General > External Integration.
- Select a specific integration policy and click Run.
Configuring Reputation System Integrations
VirusTotal Integration
Configuring VirusTotal for FortiSIEM Integration
Register at the VirusTotal website to obtain a user name, password, and the API key. For more information, see https://developers.virustotal.com/reference/overview#getting-started.
VirusTotal Incident Outbound Integration
Step 1: Create an Integration
To create an outbound integration, follow these steps.
- Go to Admin > Settings > General > External Integration.
- Click New to create a new integration or Edit to modify an existing integration.
- In the Integration Policy dialog box, provide the following values:
- Type: select Incident.
- Direction: select Outbound.
- Vendor: select VirusTotal.
- Instance: enter an instance name or accept the default.
- Plugin Name: is pre-populated with the name of the integration class:
com.accelops.service.integration.impl.VirusTotalIntegrationServiceImpl. - Password: enter your API key in the password field.
- Enter an optional Description of the integration.
- Click the edit icon next to the Incident Comments template.
- In the Incident Comments Template dialog box, select content from the Insert Content drop-down list.
- Click Save when you are finished.
- Click the edit icon next to the Organization Mapping.
- In the Org Mapping dialog box, click beneath External Company ID to enter the ID of the company you want to map to organizations.
- Click Save when you are finished.
-
Click the edit icon next to the Run for.
- In the Run for dialog box, select the organizations for which the integrations will be run.
- Click Save when you are finished.
- Enter the maximum number of incidents you want recorded in the Max Incidents field.
- Click Save.
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
FortiGuard IOC Lookup Integration
Configuring FortiGuard for FortiSIEM Integration
No additional license is required to use the FortiGuard feature. Follow the steps in FortiGuard Incident Outbound Integration and Adding Incident Notification Settings to configure this feature.
FortiGuard Incident Outbound Integration
To create an outbound integration, follow these steps.
Step 1: Create an Integration
- Go to ADMIN > Settings > General > External Integration.
- Click New to create a new integration or Edit to modify an existing integration.
- In the Integration Policy dialog box, provide the following values:
- Type: select Incident.
- Direction: select Outbound.
- Vendor: select FortiGuard IOC Lookup.
- Instance: enter an instance name or accept the default.
- Plugin Name: is pre-populated with the name of the integration class:
com.accelops.service.integration.impl.FortiGuardIOCIntegrationServiceImpl.
- Enter an optional Description of the integration.
- In the Max Incidents field, enter the maximum number of incidents you want recorded.
- Click Save.
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
RiskIQ Integration
Configuring RiskIQ for FortiSIEM Integration
Register at the RiskIQ website to obtain a user name, password, and the API keys. For more information, see https://api.riskiq.net/api/concepts.html.
RiskIQ Incident Outbound Integration
Step 1: Create an Integration
To create an outbound integration, follow these steps.
- Go to Admin > Settings > General > External Integration.
- Click New to create a new integration or Edit to modify an existing integration.
- In the Integration Policy dialog box, provide the following values:
- Type: select Incident.
- Direction: select Outbound.
- Vendor: select RiskIQ.
- Instance: enter an instance name or accept the default.
- Plugin Name: is pre-populated with the name of the integration class:
com.accelops.phoenix.jira.JiraTicketIntegration. - Username and Password, enter your RiskIQ user name and the API key as the password.
- Enter an optional Description of the integration.
- Click the edit icon next to Attribute Mapping.
- In the Incident Comments Template dialog box, select content from the Insert Content drop-down list.
- Click Save when you are finished.
- Click the edit icon next to the Organization Mapping to map attributes to resources.
-
Click the edit icon next to the Run for.
- In the Run for dialog box, select the organizations for which the integrations will be run.
- Click Save when you are finished.
- Enter the maximum number of incidents you want recorded in the Max Incidents field.
- Click Save.
Step 2: Link Integration to a Notification Policy
You need to link the integration to a notification policy, so that the integration runs when the notification policy triggers.
Take the following steps.
- Go to ADMIN > Settings > General > Notification Policy.
- Click New to create a new policy or Edit to edit an existing policy.
- In the Notification Settings dialog box, select Action > Invoke an Integration Policy, then select the edit icon.
- Choose a specific integration from the drop-down list.
- Click Save.
Configuring Communication through Proxies
If you want the communication between the FortiSIEM Supervisor and the external system to go through a proxy, then complete the following steps
- Login to Supervisor as
admin. - Go to the glassfish configuration directory:
/opt/glassfish/domains/domain1/config. - Add proxy server information to the
domain.xmlfile:<jvm-options>-Dhttp.proxyHost=172.30.57.100</jvm-options>
<jvm-options>-Dhttp.proxyPort=3128</jvm-options>
<jvm-options>-Dhttp.proxyUser=foo</jvm-options>
<jvm-options>-Dhttp.proxyPassword=password</jvm-options>
- Restart glassfish.
Modifying an External System Integration
Complete these steps to modify an External System Integration.
- Use the below options to modify an External System Integration setting.
Settings Guidelines Edit To edit an External System Integration setting. Delete To delete an External System Integration setting. - Click Save.
