ServiceNow Security Operations (SecOps) Integration
Scope and Purpose
ServiceNow FortiSIEM integration is designed to pull FortiSIEM incidents and triggering events from the remote FortiSIEM server every 30 seconds into the desired ServiceNow instance. FortiSIEM incidents pulled into the ServiceNow instance will be automatically mapped to new security incidents. Upon closing the created security incidents, the corresponding FortiSIEM incidents status on the remote FortiSIEM sever will also be updated.
XML Assets
The required XML files for this integration can be downloaded here.
File: FortiSIEM-ServiceNow-Integration-v1_3_6.zip
SHA256 hash: 945214c2128337dc7d8b03f80ebd51e1a07a8c75c855c3ec49583ca61d43e1f5
MD5 hash: d397ad5bf6ba0c0e15942958b95bad4e
Process Overview
-
The ServiceNow system administrator must request a new Paris release ServiceNow instance or login to an existing one to import the provided ServiceNow FortiSIEM integration XML file to ServiceNow.
-
The ServiceNow system administrator configures the REST Message API endpoints and Basic Auth Profile settings on the ServiceNow instance to make API calls to the remote FortiSIEM server.
-
The ServiceNow instance will begin to fetch FortiSIEM incidents and triggering events every 30 seconds.
-
The ServiceNow system administrator or ServiceNow users with security incident roles can view and update security incidents created from FortiSIEM incidents pulled.
Process and Workflow
The following information contains a detailed explanation on how ServiceNow FortiSIEM integration is set up and its usage.
ServiceNow FortiSIEM Integration Prerequisites
The following is required for ServiceNow FortiSIEM integration.
-
FortiSIEM server.
-
Paris release ServiceNow instance.
-
ServiceNow instance plugin – Security Incident Response Dependencies.
-
ServiceNow instance plugin – Security Incident Response.
ServiceNow FortiSIEM Integration Installation
A ServiceNow system administrator must take the following steps:
-
Request a new Paris release ServiceNow instance or login to an existing one.

-
In the ServiceNow instance, click the Application drop-down list and select Global.
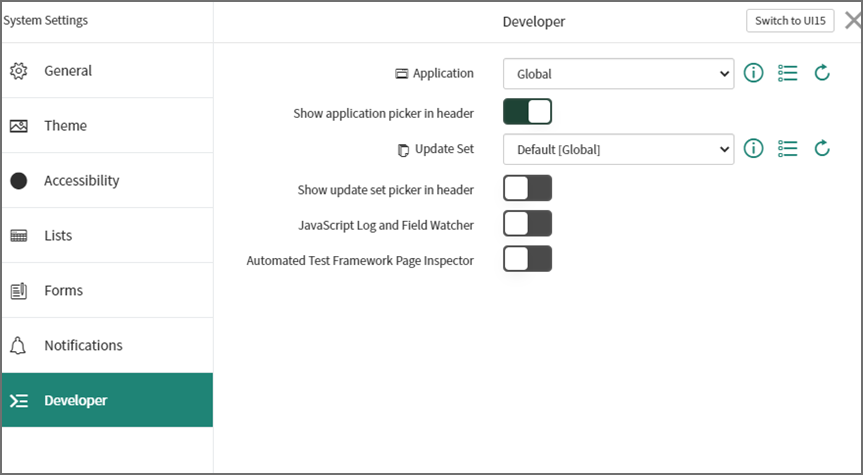
-
Click on the role drop down list and select Elevate Roles. Elevate the "System Administrator" role to "Security Admin". This new role ensures the success of the ServiceNow FortiSIEM integration import in the next step.


-
Navigate to System Definition - Tables, right click on Table Headers on the page, and select Import XML.

-
In "Import XML", select the provided
FSMSNIntegrationImportDatafile (See XML Assets) and click Upload.
-
After the upload is complete, navigate to System Web Services/Rest Message, and click on FSMAPI (This was imported in step 5) to change the FortiSIEM remote server API endpoint and basic auth profile.

-
In REST Message/FSMAPI, if the remote FortiSIEM server host name is different than the ones displayed, please manually change the hostname in “FSMAPI” and all the endpoints in HTTP Methods, as shown here. For HTTP Methods, please manually click on each record, and change the hostname.
Note: Only change the host name.(I.E.https://myNewHostName.com). The slashes or symbols after the host name must be retained.
-
In “REST Message/FSM API”, to change the basic auth profile, first click the search icon.

-
Click FSMBasicAuth, and change the user name and password accordingly. You may also create a new Basic auth profile.

-
The integration uses a “HTTPS outbound REST end point”, and requires the FortiSIEM certificate to be added to the ServiceNow Certificate Trust Store. Please follow the sub-steps here before proceeding to step 11.
-
Retrieve destination server SSL certificates. This can be given by the network administrator of the destination server, or by using the Linux command:
openssl s_client -connect <destination_server_name>:443 –showcerts
To gather the specific certificate, run this command from a Linux server:echo | openssl s_client -connect <destination_server_name>:443 2>&1 | sed --quiet '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > <destination_server_name>.pem
A sample SSL certificate is shown here.
-
Validate retrieved SSL certificate in part a to see if it has any issues or errors. It can be done through https://www.digicert.com/help/ or through the Linux command:
openssl s_client -connect <destination_server_name>:443 –showcerts
If the certificate has issues or errors, please contact the destination server administrator for a correct one. For any reason that a correct SSL certificate cannot be obtained, please refer to step 10g for a temporary workaround in a ServiceNow instance. Note that this workaround is not recommended for ServiceNow production instances. -
Now, upload the retrieved SSL certificate in part a to the ServiceNow instance. Navigate to System Definition/Certificates and on the right panel, click New.

-
On the new dialog box, take the following steps:
-
In the Name field, enter a name for the certificate.
-
From the Format drop-down list, select PEM.
-
From the Type drop-down list, select Trust Store Cert.
-
In the PEM Certificate field, enter/paste the SSL certificate retrieved in 10a.
-
When done, click Submit.

-
-
Once the certificate has been created, click on it.

-
Click Validate Stores/Certificates to ensure it is valid.

If it is valid, a “Valid trust_store” message will show. If you get an invalid certificate, please contact the destination server administrator.

-
Note: This is workaround step in ServiceNow instance to solve invalid certification issue encountered in step 10b.
This is only recommended for ServiceNow developer instances.
To proceed, take the following steps:-
Navigate to System Definition / Tables.

-
Search for “sys_properties”, click on System Property from the displayed records and navigate to Related Links.

-
Click Show List to open up all system properties entries stored in the current instance.

-
Next to the System Properties header, click New.

-
Enter the following:
In the Name field, enter "com.glide.communications.httpclient.verify_revoked_certificate".
In the Type field, enter "true|false".
In the Value field, enter "false".

-
Click Submit.
-
If the certificate in use by FortiSIEM is also Self Signed, then set the following System Property to false . Under the same section, search for com.glide.communications.httpclient.verify_hostname and change to false.

-
-
Once this record has been created, the ServiceNow instance will ignore any SSL certification validation issues or errors encountered.
The installation is now complete.
ServiceNow FortiSIEM Integration Usage
The ServiceNow FortiSIEM Integration can be used in the following ways:
View Scheduled Jobs
The ServiceNow system administrator can view scheduled jobs that are running every 30 seconds to pull FSM incidents and FSM triggering events in “System Definitions/ Scheduled Jobs”.

Monitor Scheduled Job Execution Logs
The ServiceNow system administrator can monitor the scheduled job execution logs in System Log / All.

Examine FortiSIEM Incidents, Logs, and Triggering Events
Fetched FortiSIEM incidents will be stored in the “fsm_incidents” table, and logs will be stored in “fsm_fetch_incidents_log” table. Fetched FSM triggering events will be stored in “fsm_triggering_events” table, and logs will be stored in the “fsm_riggering_events_log” table. The link between incidents and events will be stored in the “fsm_incidents_triggering_events_link” table.

View Corresponding Security Incidents
After a FortiSIEM incident has been fetched, a corresponding security incident will be created with the short description:
FSM : <IncidentTitle> - FSM Incident - <IncidentID>

Examine Security Incidents in Detail
Security incidents created by FortiSIEM incident contain the “Category”, “Source”, “Priority”, “Description”, “Short Description”, and “Company” fields, pre-defined based on corresponding FortiSIEM incident fields.

Customized "FortiSIEM Incident" Page
Security incident created by FortiSIEM incidents also have a customized UI section FSM Incident, which can be used to view FortiSIEM incident details and triggering events. For the current version V1.3.6, 10 triggering events are fetched per FortiSIEM incident.

ServiceNow FortiSIEM Integration Deletion
Deleting the Integration will remove the FortiSIEM configuration, scheduled jobs, GUI elements, Incident information from FortiSIEM and Triggering events in ServiceNow. Do not proceed if these ServiceNow elements and FortiSIEM Incident data is needed in your ServiceNow instance.
To remove ServiceNow FortiSIEM Integration, take the following steps as a ServiceNow system administrator:
-
Navigate to System Settings, and set Application to Global.

-
Click on the role drop down list and select Elevate Roles. Elevate the "System Administrator" role to "Security Admin". This role ensures the success of the ServiceNow FortiSIEM integration import in the next step.


-
With the elevated role, navigate to System Definition - Tables. Right click on “table headers” on the page and select Import XML.

-
In “Import XML”, select the provided
FSMSNIntegrationDeleteDatafile (See XML Assets) and click Upload.
-
To complete the deletion process, you must have the elevated “Security Admin” permission, and change Application to “Security Incident Response”.

-
Navigate to System Definition - Tables, right click on “table headers” of the page and select Import XML.

-
In “Import XML”, select the provided
delete_sys_ui_sectionfile (See XML Assets) and click Upload.
The ServiceNow FortiSIEM Integration deletion is now complete.
ServiceNow and FortiSIEM Field Mappings
FortiSIEM Closed State Mappings
|
FortiSIEM Incident State |
ServiceNow Incident State |
|---|---|
| MANUALLY CLEARED, 2 | Closed |
FortiSIEM Incident Category Field: "phSubIncidentCategory" Mappings
|
FortiSIEM Incident Category |
ServiceNow Category |
FortiSIEM Major Rule Categories |
|---|---|---|
| Audit | Policy violation | Change |
| Authentication | Failed login | Security |
| Command and Control | Malware | Security |
| Command and Control | Malware | Security |
| Credential Access | Unauthorized access | Security |
| Defense Evasion | Privilege escalation | Security |
| Discovery | Reconnaissance activity | Security |
| Execution | Malicious code activity | Security |
|
Exfiltration |
Confidential personal identity data exposure |
Security |
|
Exploit |
Malware |
Security |
|
Initial Access |
Unauthorized access |
Security |
|
Lateral Movement |
Privilege esclation |
Security |
|
Mail Server |
Spam source |
Security |
|
Malware |
Malware |
Security |
|
Persistence |
Malware |
Security |
|
Policy Violation |
Policy violation |
Security |
|
Privilege Escalation |
Privilege escalation |
Security |
|
Reconnaissance |
Reconnaissance activity |
Security |
|
Suspicious Activity |
Reconnaissance activity |
Security |
|
UEBA |
Insider Breach |
Security |
The following FortiSIEM incidents do not have a mapping to ServiceNow SecOps categories.
|
FortiSIEM |
ServiceNow |
FortiSIEM Major Rule Categories |
|---|---|---|
| Application | Performance | |
| Behavioral Anomaly | Security | |
| Collection | Security | |
| CPU | Performance | |
| Database | Performance | |
| Domain Controller | Performance | |
| Environmental | Performance | |
| FortiSIEM | Performance | |
| Hardware | Performance | |
| HVAC | Performance | |
| Impact | Performance | |
| Interface | Performance | |
| License | Availability | |
| Memory | Performance | |
| Network | Performance | |
| Performance | Performance | |
| SDN | Performance | |
| Server | Performance | |
| Storage | Performance | |
| Storage I/O | Performance | |
|
Storage Space |
|
Performance |
|
UPS |
|
Performance |
|
Video Conferencing |
|
Performance |
|
VoIP |
|
Performance |
|
WAN |
|
Performance |
|
Windows Cluster Service |
|
Performance |
|
Windows File System Replication |
|
Performance |
FortiSIEM Incident Severity Field: "eventSeverity" Mappings
|
FortiSIEM Severities |
ServiceNow Severities |
|---|---|
| 10 | 1 - Critical |
|
9 |
2 - High |
|
5 to 8 |
3 - Moderate |
|
1 to 4 |
4 - Low |
|
N/A |
5 - Planning |
FortiSIEM Triggering Events Attributes Displayed in ServiceNow
|
Name |
Attribute Name |
Type |
Always Present in Triggering Events |
|---|---|---|---|
| Event Receive Time | phRecvTime | date | Yes |
| Event Type | eventType | string | Yes |
| Reporting IP | reptDevIpAddr | IP | Yes |
| Source IP | srcIpAddr | IP | No |
| Source TCP/UDP Port | srclpPort | uint16 | No |
| Destination IP | destipAddr | IP | No |
| Destination TCP/UDP Port | destipPort | uint16 | No |
| User | User | string | No |
|
Raw Event Log |
rawEventMsg |
string |
Yes |
Here is an example.

Known Limitations
The following are known limitation for this integration:
-
Incidents are synced by ServiceNow to FortiSIEM every 30 seconds. This is not configurable.
-
Incident status changes in FortiSIEM, e.g. are not synced to ServiceNow.
-
Incident External ID and External Incident Status is not synced to FortiSIEM from ServiceNow until there is a change to the ServiceNow incident such as the State or assignment to a User.
