Transparent web proxy (386474)
In addition to the Explicit Web Proxy, FortiOS now supports a Transparent web proxy. While it does not have as many features as Explicit Web Proxy, the transparent proxy has the advantage that nothing needs to be done on the user's system to forward supported web traffic over to the proxy. There is no need to reconfigure the browser or publish a PAC file. Everything is transparent to the end user, hence the name. This makes it easier to incorporate new users into a proxy deployment.
You can use the transparent proxy to apply web authentication to HTTP traffic accepted by a firewall policy. In previous versions of FortiOS, web authentication required using the explicit proxy.
Normal FortiOS authentication is IP address based. Users are authenticated according to their IP address and access is allowed or denied based on this IP address. On networks where authentication based on IP address will not work you can use the Transparent Web proxy to apply web authentication that is based on the user's browser and not on their IP address. This authentication method allows you to identify individual users even if multiple users on your network are connecting to the FortiGate from the same IP address.
Using the Transparent proxy
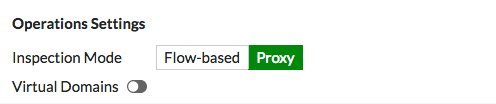
To implement the Transparent proxy, go to System > Settings and scroll down to Operations Settings and set the inspection mode to Proxy.
Then go to System > Feature Visibility and enable Explicit Proxy.

Then go to Security Profiles > Proxy Options, edit a proxy options profile and under Web Options enable HTTP Policy Redirect.
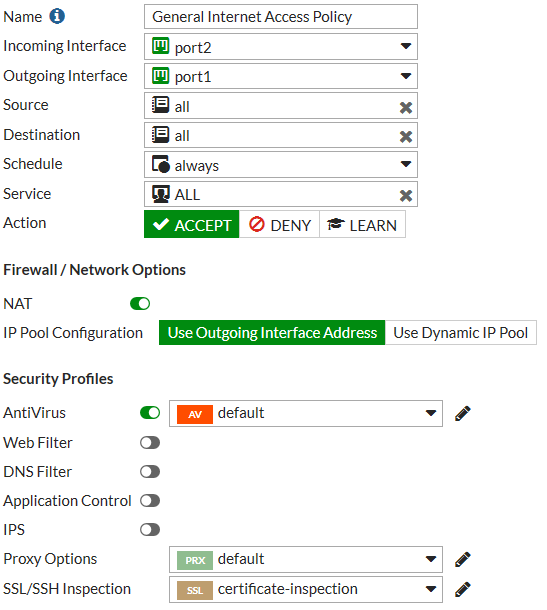
Then go to Policy & Objects > IPv4 Policy and create or edit a policy that accepts traffic that you want to apply web authentication to. This can be a general policy that accepts many different types of traffic as long as it also accepts the web traffic that you want to apply web authentication to.
Select a Security Profile and select the Proxy Options profile that you enabled HTTP Policy Redirect for.
Then go to Policy & Objects > Proxy Policy create a Transparent Proxy policy to accept the traffic that you want to apply web authentication to. Set the Proxy Type to Transparent Web. The incoming interface, outgoing interface, destination address, and schedule should either match or be a subset of the same options defined in the IPv4 policy. Addresses added to the Source must match or be a subset of the source addresses added to the IPv4 policy. You can also add the users to be authenticated by the transparent policy to the source field.
Select other transparent policy options as required.
More about the transparent proxy
The following changes are incorporated into Transparent proxy, some of which affect Explicit Web Proxy as well.
Flat policies
The split policy feature has been removed. This will make the explicit policy more like the firewall policy.
Authentication
The new authentication design is intended to separate authentication from authorization. Authentication has been moved into a new table in the FortiOS. This leaves the authorization as the domain of the explicit proxy policy.
Previously, if authentication was to be used:
- The policy would be classified as an identity based policy
- The policy would be split to add the authentication parameters
- The authentication method would be selected
- The user/group would be configured
Now:
The user/group is configured in the proxy policy
- A new authentication rule is added
- This option refers to the authentication scheme
- The authentication scheme has the details of the authentication method
The new authentication work flow for Transparent Proxy:
Toggle the transparent-http-policy match:
config firewall profile-protocol-options
edit <profile ID>
config http
set http-policy <enable|disable>
If disabled, everything works like before. If enabled, the authentication is triggered differently.
- http-policy work flow:
- For transparent traffic, if there is a regular firewall policy match, when the Layer 7 check option is enabled, traffic will be redirected to WAD for further processing.
- For redirected traffic, layer 7 policy (HTTP policy) will be used to determine how to do security checks.
- If the last matching factor is down to user ID, then it will trigger a new module to handle the L7 policy user authentication.
- Then propagate learned user information back to the system so that it can be used to match traffic for L4 policy.
New Proxy Type
There is a new subcategory of proxy in the proxy policy called Transparent Web. The old Web Proxy is now referred to as Explicit Web Proxy.
- This is set in the firewall policy
- It is available when the HTTP policy is enabled in the profile-protocol options for the firewall policy
- This proxy type supports OSI layer 7 address matching.
- This proxy type should include a source address as a parameter
- Limitations:
- It can be used for HTTPS traffic, if deep scanning is not used
- It only supports SNI address matching, i.e. domain names
- It does not support header types of address matching
- It only supports SSO authentication methods, no active authentication methods.
IP pools support
Proxies are now supported on outgoing IP pools.
SOCKSv5
SOCKSv5 authentication is now supported for explicit proxies.
To configure:
config authentication rule
edit <name of rule>
set protocol socks
end
Forwarding
Proxies support URL redirect/forwarding. This allows a non-proxy forwarding server to be assigned a rule that will redirect web traffic from one URL to another, such as redirecting traffic destined for youtube.com to restrict.youtube.com.
- A new option called "Redirect URL" has been added to the policy
- Traffic forwarding by VIP is supported
Support for explicit proxy address objects & groups into IPv4 firewall policies
This would allow the selection of web filter policy, SSL inspection policy, and proxy policy based on source IP + destination (address|explicit proxy object|category|group of any of those). This enables things like “do full SSL interception on www.google.com, but not the rest of the Search Engines category”.
Support application service in the proxy based on HTTP requests.
The application service can be configured using the following CLI commands:
config firewall service custom
edit <name of service>
set explicit-proxy enable
set app-service-type <disable|app-id|app-category>
set app-category <application category ID, integer>
set application <application ID, integer>
end
CLI
Changes:
| Previous | New |
|---|---|
config firewall explicit-proxy-policy
|
config firewall proxy-policy
|
config firewall explicit-proxy-address
|
config firewall proxy-address
|
config firewall explicit-proxy-addrgrp
|
config firewall proxy-addrgrp
|
|
config firewall explicit-proxy-policy edit <policy ID> set proxy web end |
config firewall proxy-policy edit <policy ID> set proxy explicit-web end |
Removals:
- "split-policy" from firewall explicit-proxy-policy.
The previous method to set up a split policy was:
config firewall explicit-proxy-policy
edit 1
set proxy web
set identity-based enable
config identity-based-policy
edit 1
set schedule "always"
set utm-status enable
set users "guest"
set profile-protocol-options "default"
next
end
next
end
- "auth relative" from firewall explicit-proxy-policy
The following attributes have been removed from firewall explicit-proxy-policy:
- identity-based
- ip-based
- active-auth-method
- sso-auth-method
- require-tfa
Moves:
users and groups from
firewall explicit-proxy-policy identity-based-policy
to
config firewall proxy-policy
edit 1
set groups <Group name>
set users <User name>
end
Additions:
authentication scheme
config authentication scheme
edit <name>
set method [ntlm|basic|digest|form|negotiate|fsso|rsso|none]
ntlm- NTLM authentication.basic- Basic HTTP authentication.digest- Digest HTTP authentication.form- Form-based HTTP authentication.negotiate- Negotiate authentication.fsso- FSSO authentication.rsso- RADIUS Single Sign-On authentication.none- No authentication.
authentication setting
config authentication setting
set active-auth-scheme <string>
set sso-auth-scheme <string>
set captive-portal <string>
set captive-portal-port <integer value from 1 to 65535>
active-auth-scheme- Active authentication method.sso-auth-scheme- SSO authentication method.captive-portal- Captive portal host name.captive-portal-port- Captive portal port number.
authentication rule
config authentication rule
edit <name of rule>
set status [enable|disable]
set protocol [http|ftp|socks]
set srcaddr <name of address object>
set srcaddr6 <name of address object>
set ip-based [enable|disable]
set active-auth-method <string>
set sso-auth-method <string>
set web-auth-cookie [enable|disable]
set transaction-based [enable|disable]
set comments
status- Enable/disable auth rule status.protocol- set protocols to be matchedsrcaddr /srcaddr6- Source address name. [srcaddr or srcaddr6(web proxy only) must be set].ip-based- Enable/disable IP-based authentication.active-auth-method- Active authentication method.sso-auth-method- SSO authentication method (requireip-basedenabled)web-auth-cookie- Enable/disable Web authentication cookie.transaction-based- Enable/disable transaction based authentication.comments- Comment.

