What's new in FortiOS 5.6
This chapter describes new Security Profile features added to FortiOS 5.6.
FortiOS 5.6.4
These features first appeared in FortiOS 5.6.4.
FortiOS 5.6.3
These features first appeared in FortiOS 5.6.3.
Added multiple ports and port range support in the explicit ftp/web proxy (402775)
Added multiple ports and port range support in the explicit ftp/web proxy:
- added new monitor api endpoint for checking whether a list of TCP port ranges is being used, sample usage: /api/v2/monitor/system/check-port-availability?port_ranges=[{"start":8080,"end":8080},{"start":400,"end":600},{"start":1,"end":200}]&service=webproxy
- added GUI support for port ranges in web-proxy and ftp-proxy settings
Block access to unsupported FortiClient endpoints (457695)
You can use the following command to deny registration of unsupported FortiClients endpoints. An unsupported FortiClient endpoint means the endpoint is running FortiClient but for some reason not all of the criteria are available to identify the endpoint, or the endpoint may be running an unsupported version of FortiClient. Information required that is not available could include the endpoint's IP address or MAC address is not visible.
config endpoint-control setting
set forticlient-dereg-unsupported-client {enable | disable}
end
Exempt list fix (381762)
The FortiClient Monitor page now shows exempt device types, as opposed to just the device category. FortiOS can now differentiate the three cases both from backend and GUI.
Backend changes
Differentiate the three cases:
- exempt by custom device
- exempt by device category
- exempt by device group
GUI changes
- Monitor > FortiClient Monitor page:
- show device exempt reasons as any combination of device, device category, device group, source address.
- Update REST monitor api
- (URI: /api/v2/monitor/user/device/select?compliance_visibility=true)
- update "exempt_reason" field from string to array of strings in json result
FortiOS 5.6.1
These features first appeared in FortiOS 5.6.1.
FortiGuard WAN IP blacklist service is now online (404859)
The Fortiguard WAN IP blacklist service was not online in FortiOS 5.6.0. In FortiOS 5.6.1, a notification appears on the Dashboard when WAN IP is blacklisted. Clicking on the notification brings up the blacklist details.
Application Control GUI improvements (279956)
An All Categories button on the Security Profiles > Application Control page makes it easier to apply an action (Monitor, Allow, Block, Quarantine) to all categories at once.
Note that the All Categories selector goes blank when any of theactions to be applied to individual categories is manually changed to something different than what was selected for all the categories. The Unknown Application action will match the All Categories action unless that action is Quarantine, which is unsupported for unknown applications.
Industrial Application Control signatures (434592)
The application control category Industrial is now controlled by a FortiGuard license and the default disable mask is no longer needed. The special category is also no longer used.
GUI updates to reflect package and license changes for IPS, Application Control and Industrial signatures (397010)
The following changes have been made to the GUI to reflect changes in the signature databases:
- Application Control signature database information is displayed under on the System > FortiGuard page in the FortiCare section.
- The IPS package version and license status are shown in a separate section in System > FortiGuard page. A link to manually upload the IPS database signatures has been added.
- The Industrial package version and license status are shown in a separate section in System > FortiGuard page. A link to manually upload the Industrial database signatures is available. Access to the Industrial database is provided with the purchase of the FortiGuard Industrial Security Service. The row item for this license will not appear if you are not subscribed.
- Botnet category is no longer available when searching the Application Signatures list.
Improved FortiClient monitor display (378288)
The GUI for the Monitor > FortiClient Monitor page has been revised.
- new dropdown option: Online Only or Include Offline. The default is Online Only.
- new dropdown option
- Sending FortiTelemetry Only (default)
- Include All FortiTelemetry States
- Not Sending FortiTelemetry Only
- update: Compliance status for offline device is N/A
- update: offline status indicator to grey
- new compliance status text after the icon in Compliance column
- Moved Compliance column after Status column
- Combined unregistered endpoint devices with not registered devices
FortiSandbox integration with AntiVirus in quick mode (436380)
FortiSandbox options in an AntiVirus Security Profile in quick scanning mode can now be enabled with CLI commands.
CLI syntax
config antivirus profile
edit default
set ftgd-analytics disable/everything
set analytics-max-upload 10
set analytics-wl-filetype 0
set analytics-bl-filetype 0
set analytics-db enable/disable
set scan-mode quick
end
Pre-configured parental controls for web filtering (399715)
Pre-configured filters based on the Motion Picture Association of America (MPAA) ratings can now be added to the Web Filter Security Profile. This feature is already available on FortiCloud and uses the same ratings categories.
Anti-Spam GUI updates (300423)
Changes made to the Anti-Spam profile update the GUI to reflect FortiOS 5.6 style.
FortiOS 5.6.0
These features first appeared in FortiOS 5.6.0.
Application control is now standard with FortiCare support
Application Control is now a standard part of any FortiCare support contract and the database for Application Control signatures is separate from the Intrusion Prevention System (IPS) database. However, botnet application signatures are still part of the IPS signature database since these are more closely related to security issues than application detection.
With the release of FortiOS 5.6.1, the Application Control signature database information is displayed under the System > FortiGuard page, in the FortiCare section. The botnet category is no longer available when you search for the Application Signatures list.
|
|
To receive updates to the Application Control signature database, you must have a valid FortiCare support contract. |
IPS / Application Control logging performance
There is a major boost to Application Control and IPS when logging is enabled. With the latest changes, the performance difference with or without logging enabled is negligible.
CASI functionality moved into application control (385183, 372103)
Cloud Access Security Inspection (CASI) is merged with Application Control resulting in changes to the GUI and the CLI.
GUI Changes
- Toggle option added to quickly filter CASI signatures in the Application Signatures list.
- Application Overrides table now shows any parent-child hierarchy using the --parent metadata on signatures. Deleting a parent app also deletes its child apps. And conversely, adding a child app will add all its parent apps but with implicit filter action.
- A policy breakdown is shown on existing application control profiles for policies using the profile. The breakdown indicates which policies are using a deep inspection.
- A breakdown is shown for application categories and filter overrides to indicate the number of CASI and non-CASI signatures. A lock icon is shown for applications requiring deep inspection.
CLI Changes
Commands removed:
config application casi profilecasi profileinconfig firewall policycasi profileinconfig firewall policy6casi-profile-statusandcasi-profileunderconfig firewall sniffercasi-profile-statusandcasi-profileunderconfig firewall interface-policy
Application control and Industrial signatures separate from IPS signatures (382053)
IPS, Application control and industrial signatures have been separated. The get system status command shows the versions of each signature database:
get system status Version: FortiGate-5001D v5.6.0,build1413,170121 (interim) Virus-DB: 42.00330(2017-01-23 01:16) Extended DB: 1.00000(2012-10-17 15:46) Extreme DB: 1.00000(2012-10-17 15:47) IPS-DB: 6.00741(2015-12-01 02:30) IPS-ETDB: 0.00000(2001-01-01 00:00) APP-DB: 6.00741(2015-12-01 02:30)
Block Google QUIC protocol in default Application Control configuration (385190)
QUIC is an experimental protocol from Google. With recent Google Chrome versions (52 and above), and updated Google services, more than half of connections to Google servers are now in QUIC. This affects the accuracy of Application Control. The default configuration for Application control blocks QUIC.
Users may enable QUIC with CLI commands.
CLI Syntax
config application list
edit <profile-name>
set options allow-quic
end
FortiClient profile improvements (386267, 375049)
FortiClient profiles have been changed in FortiOS 5.6 to include new protection features and to change organization of the GUI options. FortiClient profiles also use the FortiGate to warn or quarantine endpoints that are not compliant with a FortiClient profile.
A bug that prevented the Dialog and Device Inventory pages from loading when there is a large number of devices (for example, 10,000) has been fixed.
Default FortiClient profile
FortiClient profiles allow you to perform vulnerability scans on endpoints and make sure endpoints are running compliant versions of FortiClient. Also, security posture features cause FortiClient to apply realtime protection, AntiVirus, web filtering, and application control on endpoints.
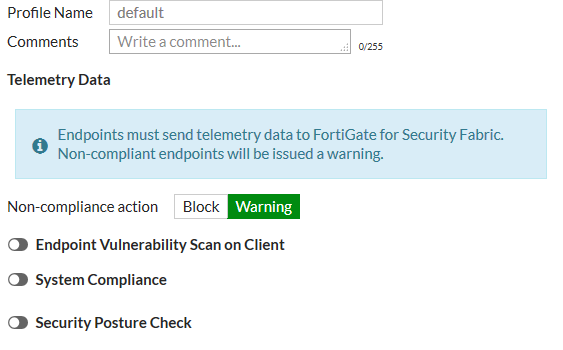
The default FortiClient profile also allows you to set a general Non-compliance action for endpoints that don't have FortiClient installed on them. The non-compliance action can be block or warning and is applied by the FortiGate. Blocked endpoints are quarantined by the FortiGate.
Endpoint vulnerability scanning
Similar to FortiOS 5.4 you can set the FortiClient Profile to run the FortiClient vulnerability scanner on endpoints and you can set the Vulnerability quarantine level to quarantine endpoints that don't comply.
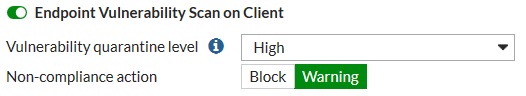
The vulnerability scan Non-compliance action can block or warn endpoints if the vulnerability scan shows they do not meet the vulnerability quarantine level.
System compliance
FortiOS 5.6 system compliance settings are similar to those in 5.4 with the addition of a non-compliance action. System compliance checking is performed by FortiClient but the non-compliance action is applied by the FortiGate.
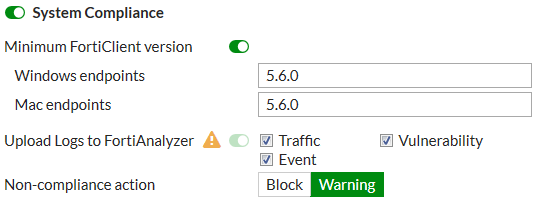
Security posture checking
Security posture checking collects realtime protection, antivirus protection, web filtering and application firewall features under the Security Posture Check heading.
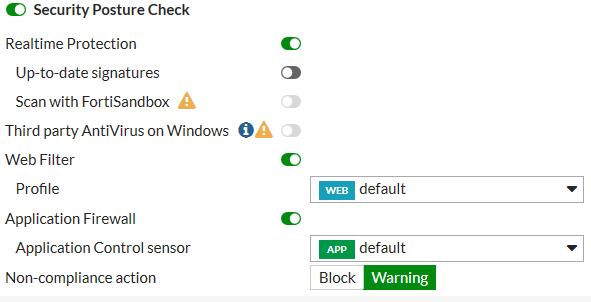
FortiClient endpoint license updates (401721)
FortiClient endpoint licenses for FortiOS 5.6.0 can be purchased in multiples of 100. There is a maximum client limit based on the FortiGate's model. FortiCare enforces the maximum limits when the customer is applying the license to a model.
If you are using the ten free licenses for FortiClient, support is provided on the Fortinet Forum (forum.fortinet.com). Phone support is only available for paid licenses.
| Model(s) | Maximum client limit |
|---|---|
| VM00 | 200 |
| FGT/FWF 30 to 90 series | 200 |
| FGT 100 to 400 series | 600 |
| FGT 500 to 900 series, VM01, VM02 | 2,000 |
| FGT 1000 to 2900 series | 20,000 |
| FGT 3000 to 3600 series, VM04 | 50,000 |
| FGT 3700D and above, VM08 and above | 100,000 |
Older FortiClient SKUs will still be valid and can be applied to FortiOS 5.4 and 5.6.
FortiClient Vulnerability Exemption Setting (407230)
A new CLI command provides a manual override for client computers with vulnerabilities that cannot be fixed.
CLI Syntax
New command to enable/disable compliance exemption for vulnerabilities that cannot be auto patched. Default is disable.
config endpoint-control profile
edit <profile-name>
config forticlient-winmac-setting
set forticlient-vuln-scan enable
set forticlient-vuln-scan-exempt [enable|disable]
end
next
end
New FortiGuard Web Filter categories (407574)
New categories added to FortiGuard Web Filter sub-categories:
- Under Security Risk:
- Newly Observed Domain (5.90)
- Newly Registered Domain (5.91)
- Under General Interest - Business
- Charitable Organizations (7.92)
- Remote Access (7.93)
- Web Analytics (7.94)
- Online Meeting (7.95)
Newly observed domain (NOD) applies to URLs whose domain name is not rated and were observed for the first time in the past 30 minutes.
Newly registered domain (NRD) applies to URLs whose domain name was registered in the previous 10 days.
Overall improvement to SSL inspection performance (405224)
The enabling / disabling of proxy cipher / kxp hardware acceleration in CP8/CP9 required restarting of the WAD daemon for the change to take effect; this bug has been repaired.
New CLI commands
The FortiGate will use the ssl-queue-threshold command to determine the maximum queue size of the CP SSL queue. In other words, if the SSL encryption/decryption task queue size is larger than the threshold, the FortiGate will switch to use CPU rather than CP. If less, it will employ CP.
config firewall ssl setting
set ssl-queue-threshold <integer>
end
The integer represents the maximum length of the CP SSL queue. Once the queue is full, the proxy switches cipher functions to the main CPU. The range is 0 - 512 and the default is 32.
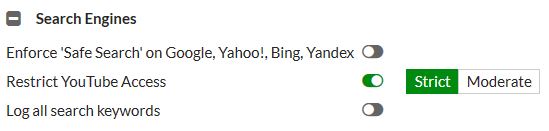
DNS profile supports safe search (403275)
Users can take advantage of pre-defined DNS doctor rules to edit DNS profiles and provide safe search for Google, Bing, and YouTube.
To add safe search to a DNS profile - GUI
- Go to Security Profiles > DNS Filter.
- Edit the default filter or create a new one.
- Enable Enforce 'Safe Search on Google, Bing, YouTube'.
- Select Strict or Moderate level of restriction for YouTube Access.
To add safe search to a DNS profile - CLI
config dnsfilter profile
edit "default"
set safe-search enable
set youtube-restrict {strict | moderate} (only available is safe-search enabled)
next
end
Changes to default SSL inspection configuration (380736)
SSL inspection is mandatory in the CLI and GUI and is enabled by default.
GUI Changes
- Updated edit dialogues for IPv4/IPv6 Policy and Explicit Proxy Policy
- SSL/SSH inspection data displayed in muted palette
- disabled the toggle button for this option
- set the default profile as "certificate-inspection"
- Updated list pages for IPv4/IPv6 Policy and Explicit Proxy Policy
- Add validation for "ssl-ssh-profile" when configuring UTM profiles
- Updated SSL/SSH Inspection list page
- disabled delete menu on GUI for default ssl profiles
- changed "Edit" menu to "View" menu for default ssl profiles
- added implicit class (grayed) the default ssl profile entries
- Updated SSL/SSH Inspection edit dialog
- disabled all the inputs for default ssl profiles except download/view trusted certificate links
- changed button to "Return" for default ssl profiles to return the list page
- Updated Profile Group edit dialog
- removed checkbox for "ssl-ssh-profile" option, make it always required.
CLI changes
1. ssl-ssh-profile default value is certificate-inspection when applicable in table firewall.profile-group, firewall.policy, firewall.policy6, firewall.proxy-policy
2. make default profiles "certificate-inspection", "deep-ssl-inspection' read only in table firewall.ssl-ssh-profile
Botnet database changes (390756)
Starting in FortiOS 5.6, FortiGate units and FortiGuard Distribution Servers (FDS0 will use object IDs IBDB and DBDB to download and update the Botnet database. Botnet protection will be part of the AntiVirus contract.
FortiOS 5.4 uses object IDs IRDB and BDDB.
Fortinet Security Fabric audit check for endpoint vulnerability and unauthorized FAP and FSW (401462)
The new Security Fabric Audit feature allows for the display of endpoint vulnerability status in real-time. Users can see:
- FortiClient devices that have critical vulnerabilities detected.
- Discovered FortiSwitches that have not yet been authorized.
- Discovered FortiAPs that have not yet been authorized.
Change to CLI commands for configuring custom Internet services (397029)
Custom internet services are no longer configured through use of the commands config application internet-service and config application internet-service-custom in the CLI.
These commands are replaced by config firewall internet-service and config firewall internet-service-custom.
CLI Syntax - examples
config firewall internet-service 1245324
set name "Fortinet-FortiGuard"
set reputation 5
set icon-id 140
set offset 1602565
config entry
edit 1
set protocol 6
set port 443
set ip-range-number 27
set ip-number 80
next
edit 2
set protocol 6
set port 8890
set ip-range-number 27
set ip-number 80
next
edit 3
set protocol 17
set port 53
set ip-range-number 18
set ip-number 31
next
edit 4
set protocol 17
set port 8888
set ip-range-number 18
set ip-number 31
next
end
end
config firewall internet-service-custom
edit "custom1"
set comment "custom1"
config entry
edit 1
set protocol 6
config port-range
edit 1
set start-port 30
set end-port 33
next
end
set dst "google-drive" "icloud"
next
end
next
end
Enable "sync-session-ttl" in "config ips global" CLI by default (399737)
sync-session-ttl is now set to enable by default in order to:
- enhance detection of P2P traffic. Efficient detection of P2P is important on hardware accelerated platforms
- ensure that IPS and the kernel use the same ttl
- ensure that IPS sessions time out sooner
New diagnose command to delete avatars (388634)
Commands to delete avatars by FortiClient UID or avatar name have been added to the CLI.
the two following commands has been added to diagnose endpoint avatar:
diagnose endpoint avatar delete <ftcl_uid>diagnose endpoint avatar delete <ftcl_uid> <username>
The attribute delete did not exist before. The values <fctl_uid> and <user_name> describe a set of avatars. If only <fctl_uid> is defined, all avatars belonging to this FortiClient UID that are not being used will be removed. If both values are defined, the avatar belonging to them will be removed unless they are being used in which case this call will cause an error to user.
Fortinet bar option disabled in profile protocol options when VDOM is in flow-based inspection mode (384953)
In order to prevent the Fortinet Bar from being enabled and redirecting traffic to proxy (WAD) when a VDOM is in flow-based mode, the Fortinet Bar option is disabled in profile protocol options.
SSL/SSH profile certificate handling changes (373835)
In order to support DSA and ECDSA key exchange (in addition to RSA) in SSL resign and replace mode, CLI commands for deep-inspection have changed. The certname command in ssl-ssh-profile has been removed.
To select from the list of available certificates in the system, use the CLI below.
edit deep-inspection
set server-cert-mode re-sign
set certname-{rsa | dsa | ecdsa}
Restricting access to YouTube (replacement for the YouTube Education filter feature) (378277)
Previous versions of FortiOS supported YouTube for Schools (YTfS). As of July 1, 2016 this feature is no longer supported by YouTube. Instead you can use the information in the YouTube support article Restrict YouTube content on your network or managed devices to achieve the same result. FortiOS supports applying Strict or Moderate restrictions using HTTP headers as described in this article.
In FortiOS 5.6 with inspection mode set to proxy-based, in a Web Filter profile under Search Engines you can select Restrict YouTube Access and select either Strict or Moderate.
Enhancements to IPS Signatures page (285543)
The IPS signatures list page now shows which IPS package is currently deployed. Users can also change their IPS package by linking directly to the FortiGate's System > FortiGuard page from the IPS Signatures list page.
DLP sensor GUI changes (307225)
The DLP sensor for file size has been corrected to indicate that the file size has to be greater than the number of KB entered. Previously, the GUI incorrectly showed that the files size could be greater than or equal to the number of KB entered.
Web Filter profile page GUI updates (309012)
The GUI for the Web Filter security profile and Web Profile Overrides pages are changed.
Web Filter profile page
- removed multilist for override user group and profile
- replaced FortiGuard categories actions icons with font icons
- added tooltip for Allow users to override blocked categories to explain the policy group dependency
Web Profile Overrides page
- removed multilist of user, user group, original profile, new profile
- duplicate profile for new profile (for bug #284239)
Web Filter Quota traffic can no longer be set to 0 (374380)
To fix a bug in older major release, the CLI has been changed so that minimum traffic quota does not allow 0 as an entry. The value entered must be in the range of 1 - 4,294,967,295; if 0 is entered, then an error message will be returned.
CLI Commands:
config webfilter profile
edit default
config ftgd-wf
config quota
edit 1
set type traffic
set value {a number in the range of 1 - 4,294,967,295}
Webcache-https and SSL deep inspection profile configuration changes (381101)
In older releases, the CLI blocked the configuration of the SSL deep inspection profile when webcache-https was enabled. This bug is fixed in FortiOS 5.6.0.
FortiGate conserve mode changes (242562, 386503)
The following changes were made to rework conserve mode and facilitate its implementation:
- Implemented CLI commands to configure extreme, red, and green memory usage thresholds in percentages of total RAM. Memory used is the criteria for these thresholds, and set at 95% (extreme), 88% (red) and 82% (green).
- Removed structure av_conserve_mode, other changes in kernel to obtain and set memory usage thresholds from the kernel
- Added conserve mode diagnostic command
diag hardware sysinfo conserve, which displays information about memory conserve mode. - Fixed conserve mode logs in the kernel
- Added conserve mode stats to the proxy daemon through command
diag sys proxy stats all | grep conserve_mode
New custom IPS and Application Control Signatures list (280954)
You can now create IPS and Application control custom signatures by going to Security Profiles > Custom Signatures. From here you can create and edit all custom IPS and Application Control signatures.
Default inspection mode set to flow-based (377392)
In FortiOS 5.6.0, the following changes were made to inspection mode:
- factory default sets the FortiGate to flow-based inspection with VDOM disabled
- whenever a VDOM is created, the default inspection mode is flow-based
- when in flow-based inspection mode, the Inspection Mode will not appear on the Dashboard; it will appear when in proxy-based inspection mode.
You must use the CLI to set the FortiGate to proxy-based inspection. To change the inspection mode back to flow-based inspection, you may use the GUI or the CLI.
config system settings
edit <name_str>
set inspection-mode {proxy | flow}
end

