FortiSandbox Integration
This chapter describes new FortiSandbox features added to FortiOS 5.4.
FortiSandbox Log entry (302818)
Users can correlate submissions to FortiSandbox with the verdict on those files by viewing results at Log & Report > AntiVirus.
Changes to FortiSandbox inspection options in AntiVirus profile
When configuring the AntiVirus profile's inspection options, users can withhold files from being submitted for inspection by type or by name pattern.
Changes to FortiSandbox GUI configuration options (354523)
This change allows you to enable the FortiSandbox appliance from the Dashboard's License Information widget.
- Go to Dashboard. Locate the License Information widget and click on the Configure button in the FortiSandbox row.
- You will be directed to the System > Cooperative Security Fabric page.
Continue with steps 3 to 9 under Connecting to a FortiSandbox below.
FortiSandbox Integration with FortiOS
The following improvements have been made to how sandboxing, using either a FortiSandbox Appliance or FortiCloud Sandboxing, integrates with a FortiGate unit.
See the Cookbook recipe Sandboxing with FortiSandbox and FortiClient, .
Connecting to a FortiSandbox
- Go to System > Cooperative Security Fabric and select Enable Sandbox Inspection.
- You can either select FortiSandbox Appliance or FortiSandbox Cloud.
- If you select FortiSandbox Appliance, add the Server IP address.
- Select Test Connectivity to verify that you can connect to FortiSandbox.
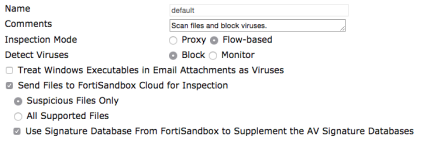
- Then edit an AntiVirus profile by going to Security Profiles > AntiVirus and selecting Send Filter to FortiSandbox Appliance for Inspection.
- In FortiOS 5.4.0, you can also elect to send Suspicious Files, Executable files or all supported files.
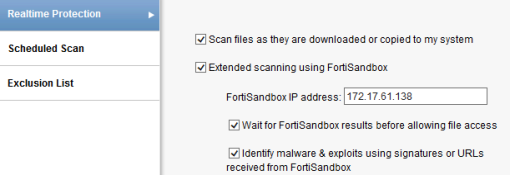
In FortiOS 5.4.1, you can choose to Treat Windows Executables in Email Attachments as Viruses and Send All Supported Files. When you select Send All Supported Files, you then have the option of withholding files from FortiSandbox inspection by type or by name pattern. - Select Use FortiSandbox Database to add signatures for suspicious files found by FortiSandbox to your FortiGate antivirus signature database.
- Then add this AntiVirus profile to a firewall policy to send files in traffic accepted by the firewall policy to FortiSandbox.
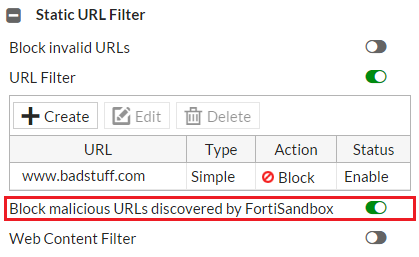
- You can also go to Security Profiles > Web Filter and select Block malicious URLs discovered by FortiSandbox.
Pushing malicious URLs to Web Filtering
The malicious URL database contains all malicious URLs active in the last month. The FortiSandbox can add the URLs where any malicious files originated to a URL filter, to block these files from being downloaded again from that URL.
This feature is enabled in a Web Filter profile under Security Profiles > Web Filter > Block malicious URLs discovered by FortiSandbox.
CLI Syntax
config webfilter profile
edit <profile>
config web
...
set blacklist [enable | disable]
...
end
Files blocked by a FortiSandbox signature can be viewed and filtered for in the FortiSandbox dashboard. Information on the current database for both malware signatures and blocked URLs can be found by going to System > Cooperative Security Fabric.
FortiSandbox Dashboard in FortiView
The FortiSandbox dashboard is available from FortiView > FortiSandbox. The dashboard shows all samples submitted for sandboxing. Information on the dashboard can be filtered by checksum, file name, result, source, status, and user name. Each entry also offers a drilldown view to show more details about a particular sample.

Pushing signatures to AntiVirus database
When a FortiSandbox discovers a malicious file, it can create a signature that is sent to the FortiGate to supplement the AntiVirus signature database. This signature can be used to block that file from entering the network again, and to prevent duplicates of the file being sent to the FortiSandbox in the future. This feature is enabled in an AntiVirus profile.
CLI Syntax
config antivirus profile
edit "default"
set ftgd-analytics {everything | suspicious}
set analytics-db {enable | disable}
end
Files blocked by a FortiSandbox signature can be viewed in entirety or as a filtered list in the FortiSandbox dashboard.
Information on the current database for malware signatures and blocked URLs can be found by going to System > Cooperative Security Fabric.
FortiClient Monitoring and Quarantine
|
|
FortiClient monitoring and quarantine is currently only supported by FortiClient 5.4 for Windows. |
FortiSandbox uses a single signature to identify tens of thousands of variations of viral code. A FortiSandbox can send frequent, dynamic signature updates to a FortiGate and FortiClient, which allows files to be blocked before they are sent to the FortiSandbox.
With FortiSandbox, FortiClient, and FortiGate integration, you can configure a FortiGate to send files to FortiSandbox for scanning.
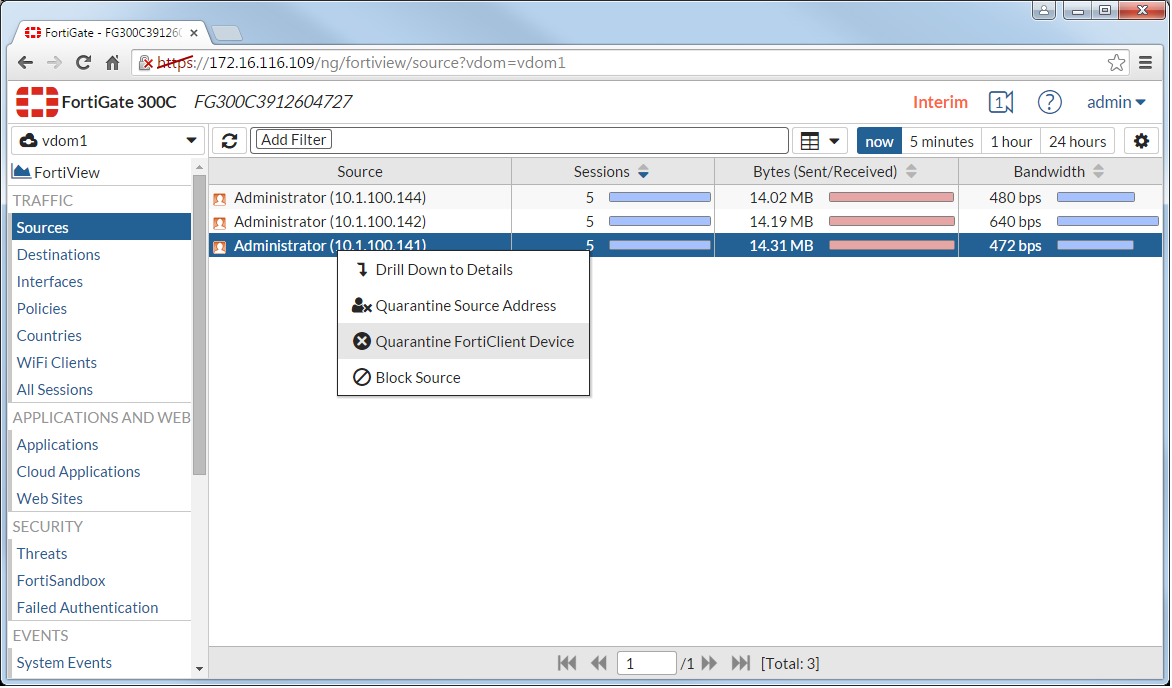
When FortiSandbox determines that a file is infected, it will notify the FortiGate of this event. Then, from FortiView, the administrator can take action to quarantine the endpoint which downloaded the infected file.
FortiGate administrators can quarantine endpoints from FortiView.
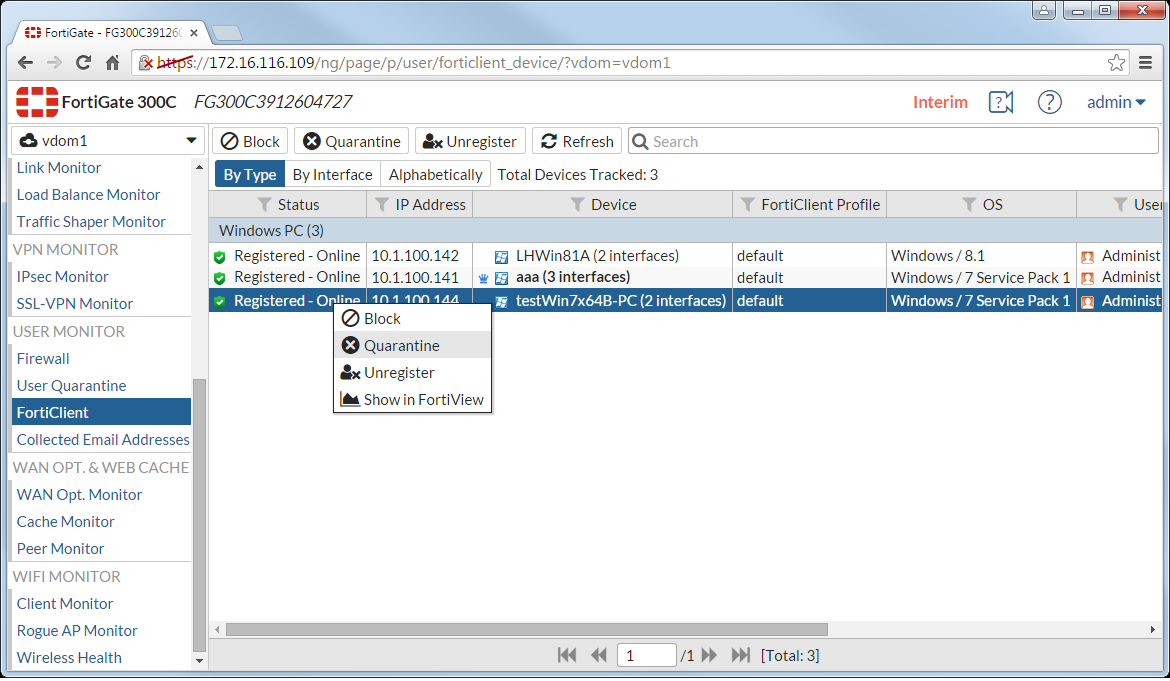
FortiGate administrators can also quarantine endpoints from the FortiClient Monitor.
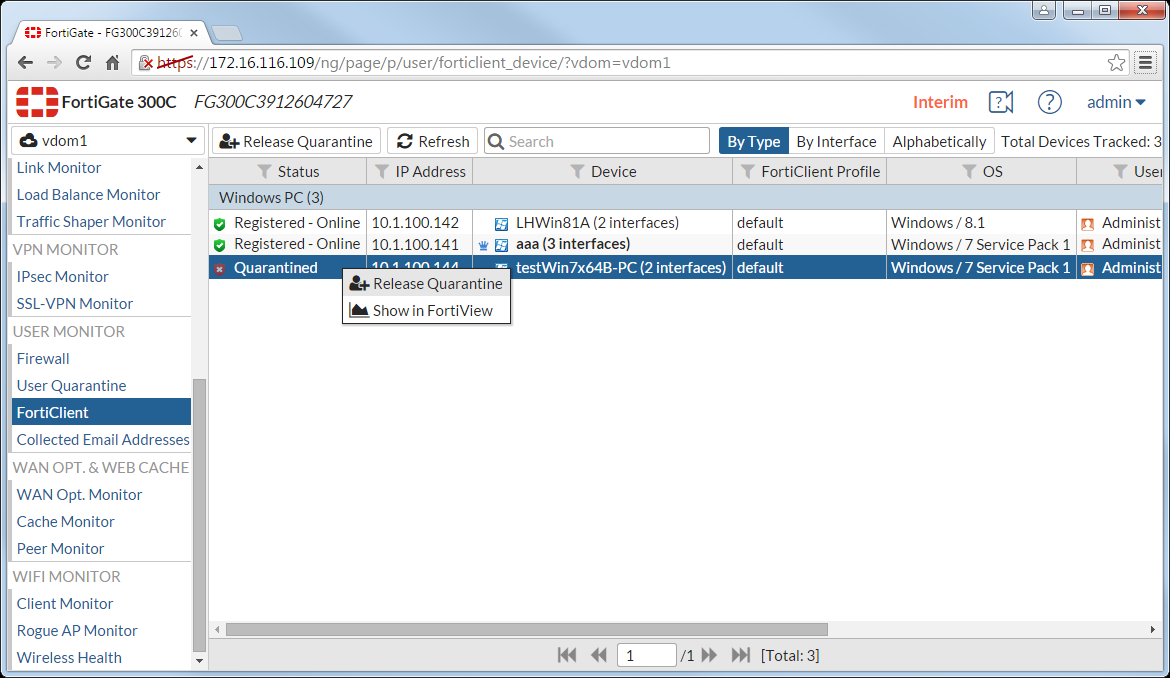
FortiGate administrators can also manually release a quarantined endpoint.
To support this, the FortiClient now supports host-level quarantine by cuting off other network traffic from the endpoint directly and preventing it from infecting or scanning the local network.
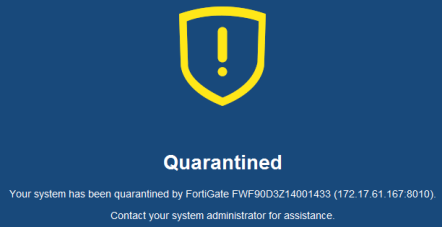
When a device is under quarantine, FortiClient cannot be shutdown or uninstalled. A user is also unable to unregister from the FortiGate that quarantined them, or register to another FortiGate unit.
Alternately, FortiGate can release the file to the client before receiving the FortiSandbox scan results, and then have FortiClient quarantine the device when the scan results are available if required.

