Networking
This chapter describes new network features added to FortiOS 5.4.
FortiTelemetry replaces FortiClient Access and other FortiClient interface settings (372945 299371)
To configure an interface to listen for connections from devices with FortiClient installed, enable FortiTelemetryAdministrative Access. FortiTelemetry was called FCT-Access or FortiClient Access in FortiOS 5.2.
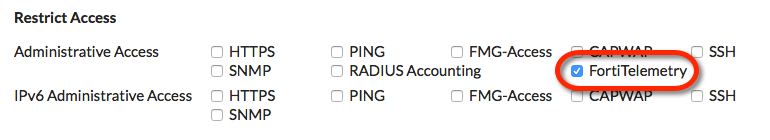
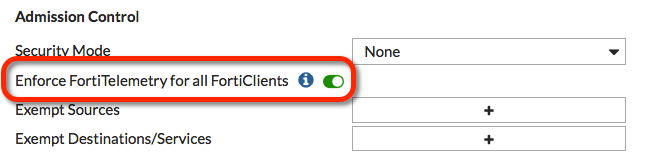
After enabling FortiTelemetry, under Admission Control you can select Enforce FortiTelemetry for all FortiClients to require clients to have FortiClient installed to be able to get access through the FortiGate. If you enable this feature you should also go to Security Profiles > FortiClient Profiles and configure FortiClient Profiles. Then you should add the configured FortiClient Profiles to firewall policies with device detection.
Use the following CLI command to enable FortiHeartBeat on an interface and enable enforcing FortiHeartBeat for all FortiClients:
config system interface
edit port1
set listen-forticlient-connection enable
set endpoint-compliance enable
end
After enabling FortiTelemetry, you can also enable DHCP server and turn on FortiClient On-Net Status to display the on-net status of FortiClient devices on the FortiClient Monitor (go to Monitor > FortiClient Monitor).
Use the following CLI command to enable FortiClient on-net status for a DHCP server added to the port1 interface:
config system dhcp server
edit 1
set interface port1
set forticlient-on-net-status enable
end
|
|
There was a name change involved with this feature. For 5.4.0, it was refered to as FortiHeartBeat, but this only appears in the 5.4.0 GA version of the FortiOS firmware. |
TLS support for Dynamic DNS Services (DDNS) (300231)
This feature is available on the FortiGate 140-POE
When clear-text is disable, the FortiGate will use ssl connection to send and receive updates to Dynamic DNS services.
To disable clear-text:
config system ddns
set clear-text disable
end
The ssl-certificate name can also be set in the same location using the command:
set ssl-certificate <cert_name>
Defaults:
- clear-text =
enable - ssl-certificate =
Fortinet_Factory
DDNS update override for DHCP (306525 290048)
This feature is available on the FortiGate 140-POE
DHCP server now has an override command option, which allows DHCP server communications to go through DDNS to do updates for the DHCP client.
- This will force a DDNS update of the AA field every time even if the DHCP client does not request it.
- This will allow the support of the allow/ignore/deny client-updates options.
Syntax:
config system dhcp server
edit 0
set ddns-update_override [enable | disable]
end
| disable | Disable DDNS update override for DHCP |
| enable | Enable DDNS update override for DHCP |
Enable or disable individual static and policy routes (174956)
CLI support has been added to [enable | disable] Static and Policy routes.
Syntax for static route in IPv4:
config route static
edit 0
set status [enable|disable]
end
Syntax for static route in IPv6:
config route static6
edit 0
set status [enable|disable]
end
Syntax for policy route in IPv4:
config router policy
edit 0
set status [enable|disable]
end
Syntax for policy route in IPv6:
config router policy6
edit 0
set status [enable|disable]
end
New option to allow copying of DSCP value in GRE tunnels (306331)
DSCP stands for the Differentiated services code point found in IPv4 and IPv6 headers, used for classifying and managing network traffic such as it relates to Quality of Service. This feature enables the keeping of the DSCP marking in the packets after encapsulation for going through GRE tunnels.
New DHCPv6 Prefix hint feature (302304)
This feature is used to "hint" to upstream DCHPv6 servers a desired prefix length for their subnet to be assigned in response to its request.
There is a possibility of duplicate prefixes being sent by ISP when using a /64 bit subnet because the first 64 bits of the address are derived from the mac address of the interface. This could cause an issue if the system administrator wishes to divide the host networks into 2 /64 bit subnets.
By receiving a /60 bit (for example) network address, the administrator can then divide the internal host works without the danger of creating duplicate subnets.
Also included in the new feature are preferred times for the life and valid life of the DHCP lease.
DHCPv6 hint for the prefix length
set dhcp6-prefix-hint <DHCPv6 prefix that will be used as a hint to the upstream DHCPv6 server>
DHCPv6 hint for the preferred life time.
set dhcp6-prefix-hint-plt <integer> 1 ~ 4294967295 seconds or "0" for unlimited lease time
DHCPv6 hint for the valid life time.
set dhcp6-prefix-hint-vlt <integer> 1 ~ 4294967295 seconds or "0" for unlimited lease tim
The FortiOS DHCP server now has an increased number of DHCP option fields (307342)
In place of specific fields the DHCP server now maintains a table for the potential options. The FortiOS DHCP server supports upto a maximum of 30 custom options.These optional fields are set in the CLI.
To get to the DHCP server:
config system dhcp server
edit <integer - ID of the specific DHCP server>
To configure the options:
config options
Once in the options context, a few new configuration commands are available. First create an ID for the table entry:
edit <integer>
set code <integer between 0 - 4294967295 to determine the DHCP option>
set type [ hex | string | ip ]
set value <option content for DHCP option types hex and string>
set ip <option content for DHCP option type ip>
end
New option to dedicate a FortiGate interface to connect to a managed FortiSwitch (294607)
When setting up an interface, an additional option has been added to the potential addressing modes that dedicates the interface to being the connection to a FortiSwitch.This is covered in more detail in the FortiSwitch section.
New CLI option to change the maximum number of IP route cache entries (363410)
The maximum number of route cache entries is configurable.
Syntax:
config system global
set max-route-cache-size <integer between 0 - 2147483647>
end
Unsetting the field will cause the value to be set to the kernel calculated default.
config system global
unset max-route-cache-size
end
Support for 802.1x fallback and 802.1x dynamic VLANs (308012)
There are 4 modes when enabling 802.1x on a virtual switch interface:
| Default | In this mode, it works as it did previously. |
| Fallback | In fallback mode, the virtual switch will be treated as a master. Only one slave can refer to a fallback master. Those ports in the master virtual switch are always authorized. After passing 802.1x authentication, the ports will be stay authorized and moved to its slave virtual switch. |
| Dynamic-vlan | In dynamic-vlan mode, the virtual switch will also be treated as a master. However, many slaves can refer to a dynamic-vlan master. Those ports in the master virtual switch are always un-authorized. After passing 802.1x/MAB authentication, the ports will be set to authorized and moved to one of its slave virtual switches. |
| Slave | In slave mode, a master must be set through security-8021x-master attribute. A slave virtual switch will use its master virtual switch's security-groups settings for authentication. |
CLI example for fallback mode
config system virtual-switch
edit "fallsw"
set physical-switch "sw0"
config port
end
edit "trust"
set physical-switch "sw0"
end
config system interface
edit "fallsw"
set vdom "root"
set ip 192.168.20.1 255.255.255.0
set allowaccess ping https ssh snmp http telnet fgfm auto-ipsec radius-acct probe-response capwap
set type hard-switch
set security-mode 802.1X
set security-8021x-mode fallback(fallback mode master switch)
set security-groups "rds-grp"(the usergroup for 802.1x)
set snmp-index 10
next
edit "trust"
set vdom "root"
set ip 192.168.22.1 255.255.255.0
set allowaccess ping https ssh snmp http telnet fgfm auto-ipsec radius-acct probe-response
set type hard-switch
set security-mode 802.1X
set security-8021x-mode slave(slave mode switch)
set security-8021x-master "fallsw" (its master switch)
set snmp-index 6
next
end
CLI example for dynamic-vlan mode
config system virtual-switch
edit "internal"
set physical-switch "sw0"
edit "lan-trust"
set physical-switch "sw0"
next
edit "lan-vlan1000"
set physical-switch "sw0"
next
edit "lan-vlan2000"
set physical-switch "sw0"
config port
edit "internal1" (normally we should not add port in slave switch. This is used if user wants to manually add one port in slave)
end
end
config system interface
edit "internal"
set vdom "root"
set ip 192.168.11.99 255.255.255.0
set allowaccess ping https ssh http fgfm capwap
set type hard-switch
set security-mode 802.1X
set security-8021x-mode dynamic-vlan<------dynamic-vlan mode master switch
set security-groups "rds-grp"<------the usergroup for 802.1x
set snmp-index 15
next
edit "lan-trust"
set vdom "root"
set ip 192.168.111.99 255.255.255.0
set allowaccess ping https ssh snmp http telnet fgfm auto-ipsec radius-acct probe-response capwap
set type hard-switch
set security-mode 802.1X
set security-8021x-mode slave<-----slave mode switch
set security-8021x-master "internal"<-----its master switch
set snmp-index 7
next
edit "lan-vlan1000"
set vdom "root"
set ip 192.168.110.1 255.255.255.0
set allowaccess ping https ssh snmp http telnet fgfm auto-ipsec radius-acct probe-response capwap
set type hard-switch
set security-mode 802.1X
set security-8021x-mode slave<-----slave mode switch
set security-8021x-master "internal"<-----its master switch
set security-8021x-dynamic-vlan-id 1000 <-----the matching vlan id for this virtual switch
set snmp-index 16
next
edit "lan-vlan2000"
set vdom "root"
set ip 192.168.220.1 255.255.255.0
set allowaccess ping https ssh snmp http telnet fgfm auto-ipsec radius-acct probe-response capwap
set type hard-switch
set security-mode 802.1X
set security-8021x-mode slave
set security-8021x-master "internal"
set security-8021x-dynamic-vlan-id 2000
set snmp-index 17
end
config user group
edit "rds-grp"
set dynamic-vlan-id 4000(default vlan id if there is no vlan attribute return from server)
set member "190"
end
Internet-Service database (288672 281333 291858)
Go to Policy & Objects > Internet Service Database to view the Internet Service Database. The database contains detailed information about services available on the Internet such as DNS servers provided by Adobe, Google, Fortinet, Apple and so on and a wide range of other services. For each service the database includes the IP addresses of the servers that host the service as well as the port and protocol number used by each IP address.
Interfaces assigned to Virtual Wired Pairs don't have "roles" (296519 )
Assigning an interface to be part of a virtual wire pairing will remove the "role" value from the interface.
STP (Spanning Tree Protocol) support for models with hardware switches (214901 291953)
STP used to be only available on the old style switch mode for the internal ports. It is now possible to activate STP on the hardware switches found in the newer models. These models use a virtual switch to simulate the old Switch Mode for the Internal ports.
The syntax for enabling STP is as follows:
config system interface
edit lan
set stp [enable | disable]
end
Command to determine interface transceiver optical signal strength (205138 282307)
The new get system interface transceiver command can be used to determine optical signal strength when using SFP/SFP+ modules. The command can be used for trouble shooting fiber optic connections to service providers. This command is hardware dependent and currently supported by FortiGate models that include various SFP/SFP+ interfaces including the FortiGate-100D/200D-POE/400D/500D/900D/1000D/1200D/1500D/3700D/3700DX) models.
New command to get IPv6 multicast router information (267650)
The following command displays IPv6 multicast router information just like the IPv4 version of the command.
get router info6 multicast.
FortiGate DHCP works with DDNS to allow FQDN connectivity to leased IPs (267043)
As clients are assigned IP addresses, they send back information that would be found in an A record to the FortiGate's DHCP server, which can take this information and passes it back to a corporate DNS server so that even devices using leased IP address can be reached using FQDNs. The settings for this feature are configured through the CLI using the ddns-update command and some other ddns related options.
Fortinet's Dynamic DNS services (FortiDDNS) can be registered to a public IP address (251748)
Fortinet's Dynamic DNS services (FortiDDNS) can be registered to a public IP address even if the FortiGate itself does not have any physical interfaces on the Internet. This is applicable when the FortiGate is behind other networking devices that are employing NAT. This can be configured in the GUI as well as CLI.
Can use firewall addresses for static route destinations (273672)
To help prevent false positive when scanning for duplicate static routes, the dst_addr field is also checked.
Can use firewall addresses for policy route destinations (244101)
When configuring a policy route, firewall addresses and address groups can be used. The only exception for address types that can be used is the URL type of address object.
Enhance TWAMP Light functionality with server/controller functionality (249255)
TWAMP(Two-Way Active Measurement Protocol) Light is a simplified architecture within the TWAMP standard. Its purpose is to measure the round trip IP performance between any two devices within a network that supports the protocol. Now FortiOS operates in more than just the role of responder/reflector.The server/controller functionality has been added.
More information about interface status available from GUI (240285)
The following information is added to the 'hover' details for each port on the GUI FortiGate faceplate:
- MAC address
- Tx/Rx bytes
- Tx/Rx packets
- Tx/Rx errors
In addition, optional columns are added to the interface list to allow users to see all of the above information.
Virtual WAN link fixes (255122)
The firmware now has the following fixes or improvements to Virtual WAN links (VWL):
- Better support for dynamic interfaces (PPPoE and DHCP).
- It can remove dynamically added routes, and restore these routes once the interfaces are not members.
- It can count pppoe interface sessions.
- It can generate a proute for a PPPoE interface. In this proute, the gateway is specified, while the outgoing (PPPoE)interface will not set.
- Adjust the route policy for a manual mode VWL service
- Support HTTP monitor by version 1.1, which obsoletes version 1.0's behavior.
- Apply multiple dst and src new feature for one policy to VWL.
- Improvements to CLI usability:
- It hides interfaces that are being used in a policy or a zone
- There is a check when adding an interface to a static route. This check will raise an error if the interface is a member of a VWL.
- Updates a proute, if based on config change, if the associated link-monitor dies.
- Fix some inappropriate messages.
- Revised the minimum value of interval for a link-monitor object. The new value is 1, so it can be compatible with V5.0. When the timeout is 1, and interval is 1.
Router > Static > Settings GUI options available from the CLI only
As part of the new WAN Load Balancing feature, the FortiOS 5.2 Router > Static > Settings GUI page has been removed. WAN Load Balancing should be used instead of the 5.2 ECMP Load Balancing Method settings. The 5.2 Link Health Monitor definitions are now only available from the CLI.
Ports preassigned as sniffer ports by default (261921)
Some models of FortiGate, by default have ports preconfigured as sniffer ports.
The models and ports preconfigered in sniffer mode are as follows:
- FortiGate 300D
- Port4
- Port8
- FortiGate 500D
- Port5
- Port6
- Port13
- Port14
Enable or disable inspecting IPv4 and IPv6 ICMP traffic (258734)
In order for the inspection of assymetric ICMP traffic to not affect TCP and UDP traffic, a pair of settings have been added that can enable/disable the inspection of ICMP traffic being routed assymetricly for both IPv4 and IPv6.
The syntax in the CLI for configuring the setting is:
- IPv4
config system settings
set asymroute-icmp
end
- IPv6
config system settings
set asymroute6-icmp
end
Send GARP on aggregate MAC change (273363)
FortiGates will send out GARP (Gratuitous Address Resolution Protocol) announcements if the MAC address of a link aggregated interface has changed to a new IP pool address due to a link failure or change in ports. This is needed when using networking devices, such as some switches, that don't perform this function when they receive LACP (Link Aggregation Control Protocol) information about changes in the MAC information.
Support split ports (252444)
The 5001D 40 GB can be split into 4 10 GB ports.This is done through a combination of hardware and software configuration. A specific 40 GB connector is used to connect to the 40 GB port and normally, the other end of the fibre optic cable would connect to another 40 GB port but a special cable can be used that is a single 40 GB connector at one end and 4 10 GB connections at the other. To use this set up the port also has to be configured to be a split port.
The configuration option can be found in the CLI:
config system global
set port-split port1 port2
end
The ports will be checked to make sure that they are not in use or referenced by other policy configurations. If in use the command will be aborted. Changing the port to be a split port will require a system reboot.
Add FortiClient enforcement to interfaces (253933)
The use of FortiClient can be enforced on individual interfaces. Go to Network > Interfaces and pick the interface of your choice. Under the heading Admission Control, you can enable the setting Allow FortiClient Connections.Once this setting is enabled, two more options become visible, Discover Clients (Broadcast) and FortiClient Enforcement. By enabling FortiClient Enforcement you enforce that in order for incoming traffic to pass through that interface it must be initiated by a device running FortiClient.
Once the use of FortiClient is enforced on the interface, FortiClient profiles should also be configured for the incoming connections. You can also set up any exemptions that are needed. Just below the FortiClient Enforcement option are fields for Exempt Sources and Exempt Destinations/Services. These can be selected from address or services object already configured on the FortiGate.
In the CLI the enforcement can be set up as follows:
config system interface
edit port1
set listen-forticlient-connection [enable|disable]
set endpoint-compliance [enable|disable]
end
Botnet C&C protection added to interfaces (254959)
The function of Botnet and Command & Control traffic protection is not new but how it can be configured has changed. It is no longer part of the AntiVirus Security profile.
The option to ScanOutgoing Connections to Botnet Sites has been added to the Interface page in the GUI.
The options are Disable, Block and Monitor.
In the CLI, the botnet scan can be configured on the interface by entering the following commands:
config system interface
edit <interface>
set scan-botnet-connections [disable | block | monitor]
end
It is also possible to enable the scanning of botnet and C&C traffic in
- Firewall policies
config firewall policy
edit <policyid>
set scan-botnet-connections [disable | block | monitor]
end
- Firewall explicit proxy policies
config firewall explicit-proxy-policy
edit <policyid>
set scan-botnet-connections [disable | block | monitor]
end
- Firewall interface policy
config firewall interface-policy
edit <policyid>
set scan-botnet-connections [disable | block | monitor]
end
- Firewall sniffer
config firewall sniffer
edit <policyid>
set scan-botnet-connections [disable | block | monitor]
end
Netflow 9.0 support (167405)
Netflow is a networking feature introduced by Cisco to collect and export information about traffic flow through routers.
The CLI changes that enable and configure "NetFlow" traffic are:
config system netflow
set collector-ip <collector IP>
set collector-port <NetFlow collector port>
set csource-ip <Source IP for NetFlow agent>
set cactive-flow-timeout <time in minutes of timeout to report active flows>
set cinactive-flow-timeout <time in seconds of timeout for periodic report of finished flows>
end
These setting can also be configured per VDOM by going to:
config system vdom-netflow
A Netflow sampler will also have to be enabled on specific interfaces.
IPv6 blackhole static routing (220101)
System administrators use black hole routing to divert undesirable traffic, such as packets from a Denial of Service (DoS) attack or communications from an illegal source. The traffic is routed to a dead interface, or a host designed to collect information for investigation. This mitigates the impact of the attack on the network.
The use of blackhole routing is enabled in the CLI as follows:
config router static6
edit <ID #>
set blackhole enable
end
A collection of Routing changes (261043)
A few new settings have been added to the CLI to assist in the supporting of the IPsec Auto Discovery feature. They are designed for:
- The support of the RIPng (RIP next generation) network command
- Limiting the maximum metric allowed to output for RIPng
- Fix NSM missing kernel address update info
The actual new settings are:
config router rip
set max-out-metric <integer value 1 - 15>
end
config router ripng
set max-out-metric <integer value 1 - 15>
end
config router ripng
config network
edit <ID # of network>
set prefix <IPv6 prefix>
end
end
DHCPv6 prefix delegation (266061)
Prefix delegation is now support for DHCP for IPv6 addressing. It is not practical to manually provision networks on a large scale in IPv6 networking. The DHCPv6 prefix delegation feature is used to assign a network address prefix, and automate the configuration and provisioning of the public routable addresses for the network.
Enabling the prefix delegation is done only in the CLI as in the following example:
config system interface
edit "wan1"
config ipv6
set ip6-mode dhcp
set ip6-allowaccess ping
set dhcp6-prefix-delegation enable
end
end
Proxy-arp extensions (250651)
The proxy-arp configuration can be extendend to an IP address range rather than a single IP address. A new setting has been added to the CLI. When configuring the proxy-arp, in addtion to setting the IP address, an end-ip address can also be set. If it is not set, the proxy-arp will be a single address as before. An example configuration using the new setting would be a follows:
config system proxy-arp
edit 1
set interface "internal"
set ip 192.168.1.100
set end-ip 192.168.1.102
end
Routing
Add asymmetric route for icmp/icmp6:
Adding asymmetric route for icmp/icmp6 without effecting tcp/udp.
Enhance TWAMP Light functionality with server/controller functionality
Add support for twamp lite mode for both controller and responder site.
CLI changes:
Add twamp protocol as a probe protocol in the link-monitor CLI.
config vdom
edit root
config system link-monitor
edit lnkmt1
set protocol twamp //TWAMP link monitor.
end
end
Route Lookup
Route Lookup is under Router > Monitor > Routing Monitor, the input criteria are Destination IP address/FQDN, and an enable check box for IPv6.
After clicking on Search button, the trace result will be selected on routing monitor page with highlight.

