Managed FortiSwitch
This chapter describes new managed FortiSwitch features added to FortiOS 5.4.
In FortiOS 5.4.2 and 5.4.1, all FortiGate models (except the FortiGate-80C) support managing FortiSwitches (FortiLink). Note that FortiSwitchOS 3.4.2 or later is required by all of the managed switches. See the FortiOS Feature/Platform matrix for more details and up-to-date compatibility info.
In FortiOS 5.4.0, the following FortiGate models support managed FortiSwitch:
FGT-60D,
FGT-60D-POE,
FWF-60D,
FWF-60D-POE,
FGT-90D,
FGT-90D-POE,
FWF-90D,
FWF-90D-POE,
FGT-100D,
FGT-140D,
FGT-140D_POE,
FGT-140D_POE_T1,
FGT-200D,
FGT-240D,
FGT-280D,
FGT-280D_POE,
FGT-600C,
FGT-800C,
FGT-1000C,
FGT-1200D,
FGT-1500D,
FGT-3700D
FortiLink is enabled by default on all physical FortiGate models. FortiLink is disabled by default on all of the FortiGate VMs.
FortiLink interface mode available for on all FortiGate models (309382)(279014)
In FortiOS 5.4.1, all FortiGate models (except the FortiGate-80C) support managing FortiSwitches (FortiLink). Note that FortiSwitchOS 3.4.2 or later is required by all of the managed switches. See the FortiOS Feature/Platform matrix for more details and up-to-date compatibility info.
FortiSwitch interface mode (305212) (279014) (294607)
With prior releases, the FortiGate required a separate FortiLink for each managed FortiSwitch. Starting in FortiOS 5.4.1, the FortiGate requires only one active FortiLink to manage all of the subtending FortiSwitches. The FortiSwitches are inter-connected and operate as one Layer 2 stack.
Depending on the network topology, you can also configure a standby FortiLink.
On the FortiGate, you configure the FortiLink as a single port or as a logical interface with multiple ports. The logical interface types supported include link-aggregation group (LAG), hardware switch and software switch.
FortiSwitch stacking (305212) (310481)
You can connect the managed FortiSwitches in a single-tier topology (aka Stack), or in a hierarchical topology.
In a single-tier topology, you connect a FortiLink from the FortiGate to one switch, and connect the switches in a ring using inter-switch links. Optionally, you can connect a standby FortiLink from the FortiGate to one of the other switches. This FortiLink remains in standby mode unless the active link fails. The following figure shows a single-tier topology with FortiGate HA:
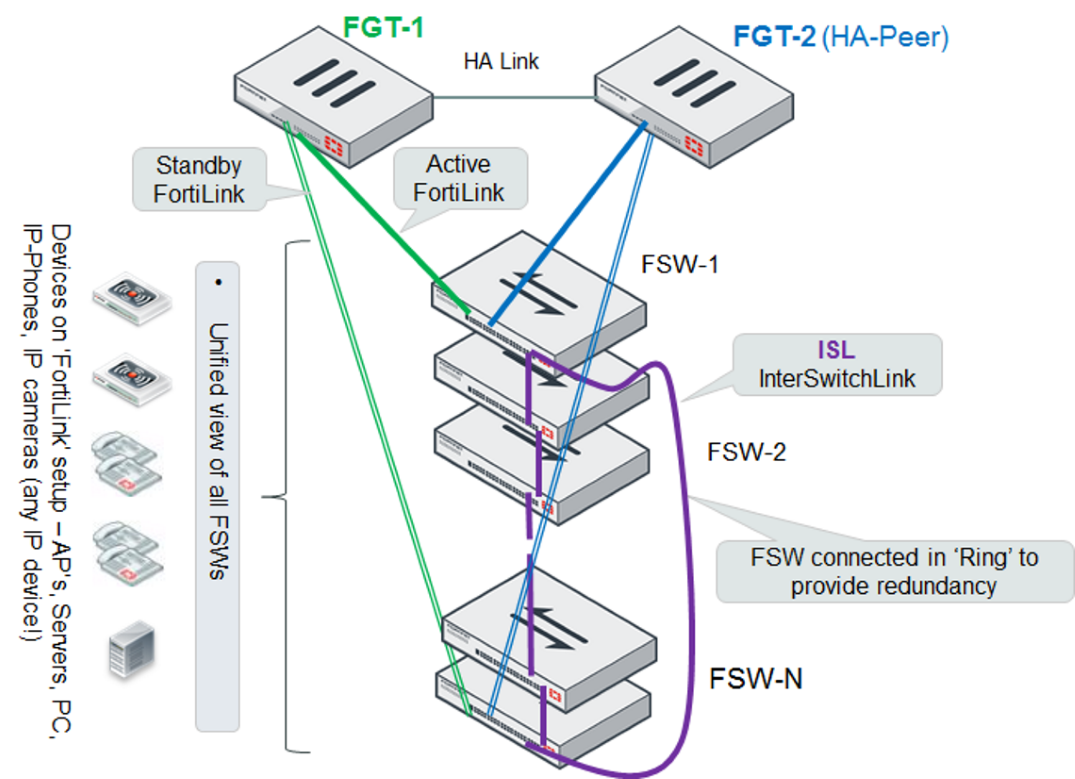
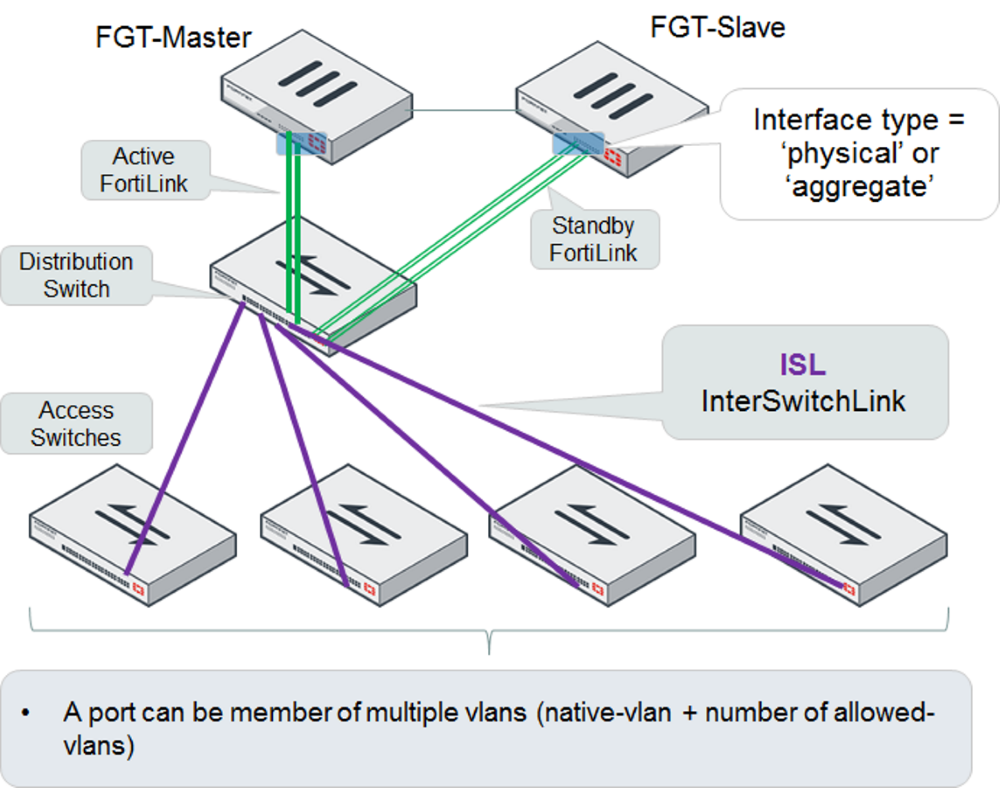
In a hierarchical topology, the FortiSwitches are connected in two tiers, and operate as one Layer 2 cluster. You connect a FortiLink from the top-tier switch to the FortiGate, and the FortiGate then manages each switch separately.
Both topologies support FortiGate HA mode. The following figure shows a hierarchical topology with FortiGate HA:
Execute FortiSwitch commands from a FortiGate (300505)
From the FortiGate, you can execute FortiSwitch commands on the managed FortiSwitch.
This feature adds a simple scripting mechanism for users to configure generic commands to be executed on the switch.
Create a command
Use the following syntax to create a command file:
config switch-controller custom-command
edit <cmd-name>
set command " <FortiSwitch commands>"
The following example creates a command file to set the STP max-age parameter:
config switch-controller custom-command
edit "stp-age-10"
set command "config switch stp setting
set max-age 10
end
"
next
end
Execute a command
After you have created a command file, use the following command on the FortiGate to execute the command file on the target switch:
exec switch-controller custom-command <cmd-name> <target-switch>
The following example runs command stp-age-10 on the specified target FortiSwitch:
FGT30E3U15003273 # exec switch-controller custom-command stp-age-10 S124DP3X15000118
Allow all defined VLANs in a FortiSwitch configuration (303818)
New port configuration option enables all defined vlans to be allowed on this port. The default value is disabled. This is a conveniece feature, to avoid having to configure all VLANs explicitly in the allowed-vlans field.
The following example shows the CLI commands to enable all VLANs on port1 of a managed switch:
FG080D3914002825 (managed-switch) # edit S124DN3W14000009
FG080D3914002825 (S124DN3W14000009) # config ports
FG080D3914002825 (ports) # edit port1
FG080D3914002825 (port1) # set allowed-vlans-all enable
When allowed-vlans-all is enabled, the allowed-vlans attribute is hidden.
FortiSwitch logs can be configured to be FortiOS system event logs (286258)
You can enable/disable the managed FortiSwitches to export their syslogs to the FortiGate. The setting is global, and the default setting is disabled.
The FortiGate sets the user field to "fortiswitch-syslog” for each entry, to allow a level of filtering.
CLI Command Syntax
config switch-controller switch-log
status (enable | disable)
severity [ emergency | alert | critical | error | warning | notification | information | debug ]
end
Stage or schedule FortiSwitch firmware upgrades (290916)
CLI Changes:
Stage FortiSwitch image to a managed FortiSwitch device.
execute switch-controller stage-swtp-image <vdom> <fortiswitch-id> <filename>
Example:
execute switch-controller stage-swtp-image root S124DN3W14000009 S124DN-IMG.swtp
S124DN3W14000009 # get system status
Version: FortiSwitch-124D v3.4.0,build0156,150929 (Interim)
S124DN3W14000009 # execute reboot
Display FortiSwitch port statistics in the FortiGate (303833)
Using the FortiGate CLI, display FortiSwitch port statistics.
Enter the following command. If you omit the port parameter, the FortiGate displays statistics for all of the ports:
diagnose switch-controller dump port-stats <switch id> <port>
The following example displays FortiSwitch port statistics for port1:
diagnose switch-controller dump port-stats S124DN3W14000095 port1
S124DN3W14000095 : Port1
tx-bytes 0, tx-packets 0, tx-mcast 0, tx-errors 0, tx-drops 0, tx-egoodpkts 0, rx-bytes 0, rx-packets 0,
rx-mcast 0, rx-errors 0, rx-drops 0, rx-emcasts 0, rx-ebroadcasts 0, rx-eundersize 0, rx-efragments 0, rx-eoversize 0, rx-ejabbers 0
rx-ecollisions 0, rx-ecrcalignments 0, rx-egoodpkts 0, rx-l3packets 0,
FortiLink per switch port connected device visibility (356560)(0357579) (302087) (303835) (357579)
In the FGT GUI, User & Device > Device LIst displays a list of devices attached to the FortiSwitch ports. For each device, table displays the IP address of the device, and the interface (FSW name and port).
From the CLI, the following command displays information about the host devices:
diagnose switch-controller dump mac-hosts_switch-ports
For each device, the CLI displays the IP address of the device, and the interface (FSW name and port).
Display FortiSwitches in Cooperative Security Fabric (CSF) Physical Topology (366873)
Each managed FortiSwitch is displayed as a device subtending the FortiGate.
Log message written when a FortiSwitch connects or disconnects (366519)
Add switch id to the log that is generated when a FortiSwitch connects to the FortiGate, or disconnects.
FS1D483Z14000057 is connected
FS1D483Z14000057 is disconnected
FortiGate CLI support for FortiSwitch features (on non-FortiLink ports)
You can configure additional FortiSwitch capabilities (STP, LAG, Storm Control) directly from the FortiGate, without the need to log in to the FortiSwitch.
Configuring STP
Starting in FortiSwitch release 3.4.2, STP is enabled by default for the non-FortiLink ports on the switch.
You can enable or disable STP globally, or per-switch-port.
Use the following CLI commands for global configuration:
config switch-controller stp-settings
set status enable/disable
set name <name>
set revision <stp revision>
set hello-time <hello time>
set forward-time <forwarding delay>
set max-age <maximum aging time>
set max-hops <maximum number of hops>
end
Use the following commands for global configuration:
config switch-controller managed-switch
edit <switch-id>
config ports
edit <port name>
set stp-state (enabled | disabled)
end
Configuring LAG
You can configure a link aggregation group for non-fortilink ports on a FortiSwitch. You cannot configure ports from different FortiSwitches in one LAG.
config switch-controller managed-switch
edit <switch-id>
config ports
edit <trunk name>
set type trunk
set mode < static | lacp > Link Aggreation mode
set bundle (enable | disable)
set min-bundle <int>
set max-bundle <int>
set members < port1 port2 ...>
next
end
end
end
Configuring Storm Control
Storm control prevents traffic on a LAN from being disrupted by a broadcast, multicast, or unicast storm on a port. Storm control uses the data rate of the link to measure traffic activity.
When the data rate exceeds the configured threshold, storm control drops excess traffic. You can configure the types of traffic to drop: broadcast, unknown unicast, or multicast.
The Storm Control settings are global to all of the non-FortiLink ports on the managed switches. Use the following CLI commands to configure storm control:
config switch-controller switch-storm-control
set rate <rate>
set unknown-unicast (enable | disable)
set unknown-multicast (enable | disable)
set broadcast (enable | disable)
end
The Rate units is packets per second. The default value is 500.
New FortiLink topology diagram (289005 271675 277441)
For managed FortiSwitches (WIFI & Switch Controller > Managed FortiSwitch), the system now displays the overall topology of the managed FortiSwitches that are connected to this FortiGate.
The topology lists the FortiLink ports on the FortiGate, and displays a full faceplate for each connected FortiSwitch (also showing the FortiLink ports on each FortiSwitch). You can right-click to authorize a managed FortiSwitch or left-click to edit the managed FortiSwitch information.
The topology can displays multiple FortiLinks to each FortiSwitch, as FortiOS 5.4 provides support for FortiLink as a LAG.
New interface option to auto-authorize extension devices 294966
If you enable the auto-authorize option on a FortiGate FortiLink port, the FortiGate will automatically authorize the managed FortiSwitch connected to this FortiLink. The new option is only visible when the interface type is set to Dedicate to Extension Device.
New CLI setting to enable pre-standard PoE detection on managed FortiSwitch ports 293512
This feature is available in FortiSwitchOS 3.3.2 and later releases.
Use the following commands to enable this setting on a managed FortiSwitch port:
config switch-controller managed-switch
edit $FSW
config ports
edit "port1"
set poe-pre-standard-detection enable/disable (the default is disable)
next
end
end
Reset any POE port (by toggling the power OFF and then ON):
execute switch-controller poe-reset <fortiswitch-id> <port>
Display general POE status:
get switch-controller <fortiswitch-id> <port>
FortiGate HA cluster support for Managed Switches (276488)
Added the capability to support managed switches from a FortiGate HA cluster. If a standby FortiGate becomes active, it automatically establishes connectivity with the managed switches.
FortiLink GUI updates (288963)
New VLAN view to create and manage VLANs, including setting the VLAN id.
New Ports view of the managed FortiSwitches. The view now displays port status, including the assigned VLAN and the POE status for each port.
This view provides a clearer way to assign VLAN attributes to multiple ports on different FortiSwitches. The VLAN ID and color of each VLAN is clearly visible in the port assignment list. Also, when you configure a VLAN, you can now specify the VLAN ID.

