Using the CLI
The command line interface (CLI) is an alternative configuration tool to the web-based manager. While the configuration of the web-based manager uses a point-and-click method, the CLI requires typing commands or uploading batches of commands from a text file, like a configuration script.
This section also explains common CLI tasks that an administrator does on a regular basis and includes the topics:
Connecting to the CLI
You can access the CLI in three ways:
- Locally with a console cable — Connect your computer directly to the FortiGate unit’s console port. Local access is required in some cases:
- If you are installing your FortiGate unit for the first time and it is not yet configured to connect to your network, unless you reconfigure your computer’s network settings for a peer connection, you may only be able to connect to the CLI using a local serial console connection.
- Restoring the firmware utilizes a boot interrupt. Network access to the CLI is not available until after the boot process has completed, making local CLI access the only viable option.
- Through the network — Connect your computer through any network attached to one of the FortiGate unit’s network ports. The network interface must have enabled Telnet or SSH administrative access if you will connect using an SSH/Telnet client, or HTTP/HTTPS administrative access if you will connect using the CLI Console widget in the web-based manager.
- Locally with FortiExplorer — Connect your computer directly to the FortiGate unit’s USB management port. FortiExplorer provides direct access to the FortiOS setup wizard, Web-based Manager, and CLI console.
Connecting to the CLI using a local console
Local console connections to the CLI are formed by directly connecting your management computer or console to the FortiGate unit, using its DB-9 or RJ-45 console port. To connect to the local console you need:
- A computer with an available serial communications (COM) port.
- The RJ-45-to-DB-9 or null modem cable included in your FortiGate package.
- Terminal emulation software such as HyperTerminal for Microsoft Windows.
The following procedure describes connection using Microsoft HyperTerminal software; steps may vary with other terminal emulators.
To connect to the CLI using a local serial console connection
- Using the null modem or RJ-45-to-DB-9 cable, connect the FortiGate unit’s console port to the serial communications (COM) port on your management computer.
- On your management computer, start HyperTerminal.
- For the Connection Description, enter a Name for the connection, and select OK.
- On the Connect using drop-down list box, select the communications (COM) port on your management computer you are using to connect to the FortiGate unit.
- Select OK.
- Select the following Port settings and select OK.
| Bits per second | 9600 |
| Data bits | 8 |
| Parity | None |
| Stop bits | 1 |
| Flow control | None |
- Press Enter or Return on your keyboard to connect to the CLI.
- Type a valid administrator account name (such as
admin) and press Enter. - Type the password for that administrator account and press Enter. (In its default state, there is no password for the
adminaccount.)
The CLI displays the following text:
Welcome!
Type ? to list available commands.
You can now enter CLI commands, including configuring access to the CLI through SSH or Telnet.
Enabling access to the CLI through the network (SSH or Telnet)
SSH or Telnet access to the CLI is accomplished by connecting your computer to the FortiGate unit using one of its RJ‑45 network ports. You can either connect directly, using a peer connection between the two, or through any intermediary network.
|
|
If you do not want to use an SSH/Telnet client and you have access to the web-based manager, you can alternatively access the CLI through the network using the CLI Console widget in the web-based manager. |
You must enable SSH and/or Telnet on the network interface associated with that physical network port. If your computer is not connected directly or through a switch, you must also configure the FortiGate unit with a static route to a router that can forward packets from the FortiGate unit to your computer. You can do this using either a local console connection or the web-based manager.
Requirements
- A computer with an available serial communications (COM) port and RJ-45 port
- Terminal emulation software such as HyperTerminal for Microsoft Windows
- The RJ-45-to-DB-9 or null modem cable included in your FortiGate package
- A network cable
- Prior configuration of the operating mode, network interface, and static route.
To enable SSH or Telnet access to the CLI using a local console connection
- Using the network cable, connect the FortiGate unit’s network port either directly to your computer’s network port, or to a network through which your computer can reach the FortiGate unit.
- Note the number of the physical network port.
- Using a local console connection, connect and log into the CLI.
- Enter the following command:
config system interface
edit <interface_str>
set allowaccess <protocols_list>
end
where:
<interface_str>is the name of the network interface associated with the physical network port and containing its number, such asport1<protocols_list>is the complete, space-delimited list of permitted administrative access protocols, such ashttps ssh telnet
For example, to exclude HTTP, HTTPS, SNMP, and PING, and allow only SSH and Telnet administrative access on
port1:
config system interface
edit port1
set allowaccess ssh telnet
end
- To confirm the configuration, enter the command to display the network interface’s settings.
show system interface <interface_str>
The CLI displays the settings, including the allowed administrative access protocols, for the network interfaces.
Connecting to the CLI using SSH
Once the FortiGate unit is configured to accept SSH connections, you can use an SSH client on your management computer to connect to the CLI.
Secure Shell (SSH) provides both secure authentication and secure communications to the CLI. FortiGate units support 3DES and Blowfish encryption algorithms for SSH.
Before you can connect to the CLI using SSH, you must first configure a network interface to accept SSH connections. The following procedure uses PuTTY. Steps may vary with other SSH clients.
To connect to the CLI using SSH
- On your management computer, start an SSH client.
- In Host Name (or IP Address), enter the IP address of a network interface on which you have enabled SSH administrative access.
- In Port, enter
22. - For the Connection type, select SSH.
- Select Open.
The SSH client connects to the FortiGate unit.
The SSH client may display a warning if this is the first time you are connecting to the FortiGate unit and its SSH key is not yet recognized by your SSH client, or if you have previously connected to the FortiGate unit but used a different IP address or SSH key. This is normal If your management computer is directly connected to the FortiGate unit with no network hosts between them.
- Click Yes to verify the fingerprint and accept the FortiGate unit’s SSH key. You will not be able to log in until you have accepted the key.
- The CLI displays a login prompt.
- Type a valid administrator account name (such as
admin) and press Enter. - Type the password for this administrator account and press Enter.
The FortiGate unit displays a command prompt (its host name followed by a
#. You can now enter CLI commands.
|
|
If three incorrect login or password attempts occur in a row, you will be disconnected. If this occurs, wait one minute, then reconnect to attempt the login again. |
Connecting to the CLI using Telnet
Once the FortiGate unit is configured to accept Telnet connections, you can use a Telnet client on your management computer to connect to the CLI.
|
|
Telnet is not a secure access method. SSH should be used to access the CLI from the Internet or any other untrusted network. |
Before you can connect to the CLI using Telnet, you must first configure a network interface to accept Telnet connections.
To connect to the CLI using Telnet
- On your management computer, start a Telnet client.
- Connect to a FortiGate network interface on which you have enabled Telnet.
- Type a valid administrator account name (such as
admin) and press Enter. - Type the password for this administrator account and press Enter.
The FortiGate unit displays a command prompt (its host name followed by a
#. You can now enter CLI commands.
|
|
If three incorrect login or password attempts occur in a row, you will be disconnected. If this occurs, wait one minute, then reconnect to attempt the login again. |
Connecting to the CLI locally with FortiExplorer
FortiExplorer is a standalone software solution that allows you to connect to your FortiGate device using the USB interface of your management computer. FortiExplorer provides direct access to the FortiOS setup wizard, Web-based Manager, and CLI console.
FortiExplorer is available for download from the Customer Service & Support website https://support.fortinet.com in firmware images. FortiExplorer is available for both Microsoft Windows and Mac OS X computers.
FortiExplorer provides a user-friendly tool that you can use to configure a FortiGate unit over a standard USB connection, rather than using a console cable or Ethernet connection.
|
|
Do not connect the USB cable until after FortiExplorer has been installed. |
Installing FortiExplorer on Microsoft Windows
To install FortiExplorer on a Microsoft Windows workstation:
- Double-click the .msi or .exe file and follow the instructions on-screen.
- Connect the USB cable to the FortiGate unit and then to the management computer.
- The FortiExplorer Fortinet Device Easy Configuration Utility opens when the USB cable is connected. Select Install the hardware automatically and select Next.
- After a moment, FortiExplorer will launch.
Installing FortiExplorer on Mac OS X
To install FortiExplorer on a Mac OS X workstation:
- Double-click the .dmg file and drag the FortiExplorer program file into the Applications folder.
- Connect the USB cable to the FortiGate unit and then to the management computer.
- Double-click the FortiExplorer icon to launch the application.
Starting the CLI from FortiExplorer
The below image shows the FortiExplorer tool connected to a FortiGate 100D device. You have two options for connecting to the CLI.
- The left window pan, in the Devices section, under the specific FortiGate's name, select on Command-line Interface. Select the text
- In the main window pane, at the bottom, there is an icon of a terminal window beside the text Command-line Interface. Select the icon.
Selecting either of these links will open a terminal emulation or command line interface in the main window pane of the FortiExplorer window.
Command syntax
When entering a command, the command line interface (CLI) requires that you use valid syntax and conform to expected input constraints. It will reject invalid commands.
Fortinet documentation uses the following conventions to describe valid command syntax
Terminology
Each command line consists of a command word that is usually followed by words for the configuration data or other specific item that the command uses or affects:
get system admin
To describe the function of each word in the command line, especially if that nature has changed between firmware versions, Fortinet uses terms with the following definitions.
Command syntax terminology
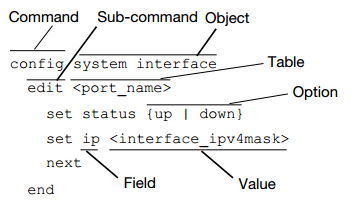
- command — A word that begins the command line and indicates an action that the FortiGate unit should perform on a part of the configuration or host on the network, such as
configorexecute. Together with other words, such as fields or values, that end when you press the Enter key, it forms a command line. Exceptions include multiline command lines, which can be entered using an escape sequence.
Valid command lines must be unambiguous if abbreviated. Optional words or other command line permutations are indicated by syntax notation. - sub-command — A kind of command that is available only when nested within the scope of another command. After entering a command, its applicable sub-commands are available to you until you exit the scope of the command, or until you descend an additional level into another sub-command. Indentation is used to indicate levels of nested commands.
Not all top-level commands have sub-commands. Available sub-commands vary by their containing scope. - object — A part of the configuration that contains tables and/or fields. Valid command lines must be specific enough to indicate an individual object.
- table — A set of fields that is one of possibly multiple similar sets which each have a name or number, such as an administrator account, policy, or network interface. These named or numbered sets are sometimes referenced by other parts of the configuration that use them.
- field — The name of a setting, such as
iporhostname. Fields in some tables must be configured with values. Failure to configure a required field will result in an invalid object configuration error message, and the FortiGate unit will discard the invalid table. - value — A number, letter, IP address, or other type of input that is usually your configuration setting held by a field. Some commands, however, require multiple input values which may not be named but are simply entered in sequential order in the same command line. Valid input types are indicated by constraint notation.
- option — A kind of value that must be one or more words from of a fixed set of options.
Indentation
Indentation indicates levels of nested commands, which indicate what other subcommittees are available from within the scope. For example, the edit sub-command is available only within a command that affects tables, and the next sub-command is available only from within the edit sub-command:
config system interface
edit port1
set status up
end
Notation
Brackets, braces, and pipes are used to denote valid permutations of the syntax. Constraint notations, such as <address_ipv4>, indicate which data types or string patterns are acceptable value input.
Command syntax notation
| Convention | Description |
|---|---|
Square brackets [ ] |
A non-required word or series of words. For example:[verbose {1 | 2 | 3}]indicates that you may either omit or type both the verbose word and its accompanying option, such as verbose 3. |
Angle brackets < > |
A word constrained by data type. The angled brackets contain a descriptive name followed by an underscore ( _ ) and suffix that indicates the valid data type. For example, <retries_int>, indicates that you should enter a number of retries, such as 5.Data types include:
|
|
|
Curly braces { } |
A word or series of words that is constrained to a set of options delimited by either vertical bars or spaces. You must enter at least one of the options, unless the set of options is surrounded by square brackets [ ]. |
Options delimited by vertical bars | |
Mutually exclusive options. For example:{enable | disable}indicates that you must enter either enable or disable, but must not enter both. |
| Options delimited by spaces | Non-mutually exclusive options. For example:{http https ping snmp ssh telnet}indicates that you may enter all or a subset of those options, in any order, in a space-delimited list, such as: ping https ssh |
Sub-commands
Each command line consists of a command word that is usually followed by words for the configuration data or other specific item that the command uses or affects:
get system admin
Sub-commands are available from within the scope of some commands.When you enter a sub-command level, the command prompt changes to indicate the name of the current command scope. For example, after entering:
config system admin
the command prompt becomes:
(admin)#
Applicable sub-commands are available to you until you exit the scope of the command, or until you descend an additional level into another sub-command.
For example, the edit sub-command is available only within a command that affects tables; the next sub-command is available only from within the edit sub-command:
config system interface
edit port1
set status up
next
end
Sub-command scope is indicated by indentation.
Available sub-commands vary by command. From a command prompt within config, two types of sub-commands might become available:
- commands affecting fields
- commands affecting tables
Commands for tables
| clone <table> | Clone (or make a copy of) a table from the current object. For example, in config firewall policy, you could enter the following command to clone security policy 27 to create security policy 30:clone 27 to 30In config antivirus profile, you could enter the following command to clone an antivirus profile named av_pro_1 to create a new antivirus profile named av_pro_2:clone av_pro_1 to av_pro_2clone may not be available for all tables. |
| delete <table> | Remove a table from the current object. For example, in config system admin, you could delete an administrator account named newadmin by typing delete newadmin and pressing Enter. This deletes newadmin and all its fields, such as newadmin’s first-name and email-address.delete is only available within objects containing tables. |
| edit <table> | Create or edit a table in the current object. For example, in config system admin:• edit the settings for the default admin administrator account by typing edit admin. • add a new administrator account with the name newadmin and edit newadmin‘s settings by typing edit newadmin.edit is an interactive sub-command: further sub-commands are available from within edit.edit changes the prompt to reflect the table you are currently editing.edit is only available within objects containing tables.In objects such as security policies, <table> is a sequence number. To create a new entry without the risk of overwriting an existing one, enter edit 0. The CLI initially confirms the creation of entry 0, but assigns the next unused number after you finish editing and enter end. |
| end | Save the changes to the current object and exit the config command. This returns you to the top-level command prompt. |
| get | List the configuration of the current object or table. • In objects, get lists the table names (if present), or fields and their values.• In a table, get lists the fields and their values.For more information on get commands, see the CLI Reference. |
| purge | Remove all tables in the current object. For example, in config user local, you could type get to see the list of user names, then type purge and then y to confirm that you want to delete all users.purge is only available for objects containing tables.Caution: Back up the FortiGate unit before performing a purge. purge cannot be undone. To restore purged tables, the configuration must be restored from a backup.Caution: Do not purge system interface or system admin tables. purge does not provide default tables. This can result in being unable to connect or log in, requiring the FortiGate unit to be formatted and restored. |
| rename <table> to <table> | Rename a table. For example, in config system admin, you could rename admin3 to fwadmin by typing rename admin3 to fwadmin.rename is only available within objects containing tables. |
| show | Display changes to the default configuration. Changes are listed in the form of configuration commands. |
Example of table commands
From within the system admin object, you might enter:
edit admin_1
The CLI acknowledges the new table, and changes the command prompt to show that you are now within the admin_1 table:
new entry 'admin_1' added
(admin_1)#
Commands for fields
| abort | Exit both the edit and/or config commands without saving the fields. |
| append | Add an option to an existing list. |
| end | Save the changes made to the current table or object fields, and exit the config command. (To exit without saving, use abort instead.) |
| get | List the configuration of the current object or table. • In objects, get lists the table names (if present), or fields and their values.• In a table, get lists the fields and their values. |
| move | Move an object within a list, when list order is important. For example, rearranging security policies within the policy list. |
| next | Save the changes you have made in the current table’s fields, and exit the edit command to the object prompt. (To save and exit completely to the root prompt, use end instead.)next is useful when you want to create or edit several tables in the same object, without leaving and re-entering the config command each time.next is only available from a table prompt; it is not available from an object prompt. |
| select | Clear all options except for those specified. For example, if a group contains members A, B, C, and D and you remove all users except for B, use the command select member B. |
| set <field> <value> | Set a field’s value. For example, in config system admin, after typing edit admin, you could type set password newpass to change the password of the admin administrator to newpass.Note: When using set to change a field containing a space-delimited list, type the whole new list. For example, set <field> <new‑value> will replace the list with the <new-value> rather than appending <new-value> to the list. |
| show | Display changes to the default configuration. Changes are listed in the form of configuration commands. |
| unselect | Remove an option from an existing list. |
| unset <field> | Reset the table or object’s fields to default values. For example, in config system admin, after typing edit admin, typing unset passwordadmin administrator account to the default (in this case, no password). |
Example of field commands
From within the admin_1 table, you might enter:
set password my1stExamplePassword
to assign the value my1stExamplePassword to the password field. You might then enter the next command to save the changes and edit the next administrator’s table.
Permissions
Depending on the account that you use to log in to the FortiGate unit, you may not have complete access to all CLI commands. Access profiles control which CLI commands an administrator account can access. Access profiles assign either read, write, or no access to each area of the FortiGate software. To view configurations, you must have read access. To make changes, you must have write access.
Unlike other administrator accounts, the administrator account named admin exists by default and cannot be deleted. The admin administrator account is similar to a root administrator account. This administrator account always has full permission to view and change all FortiGate configuration options, including viewing and changing all other administrator accounts. Its name and permissions cannot be changed. It is the only administrator account that can reset another administrator’s password without being required to enter that administrator’s existing password.
|
|
Set a strong password for the admin administrator account, and change the password regularly. By default, this administrator account has no password. Failure to maintain the password of the admin administrator account could compromise the security of your FortiGate unit. |
For complete access to all commands, you must log in with the administrator account named admin.
Tips
Basic features and characteristics of the CLI environment provide support and ease of use for many CLI tasks.
Help
To display brief help during command entry, press the question mark (?) key.
- Press the question mark (?) key at the command prompt to display a list of the commands available and a description of each command.
- Type a word or part of a word, then press the question mark (?) key to display a list of valid word completions or subsequent words, and to display a description of each.
Shortcuts and key commands
Shortcuts and key commands
| Action | Keys |
|---|---|
| List valid word completions or subsequent words. If multiple words could complete your entry, display all possible completions with helpful descriptions of each. |
? |
| Complete the word with the next available match. Press the key multiple times to cycle through available matches. |
Tab |
| Recall the previous command. Command memory is limited to the current session. |
Up arrow, or Ctrl + P |
| Recall the next command. | Down arrow, or Ctrl + N |
| Move the cursor left or right within the command line. | Left or Right arrow |
| Move the cursor to the beginning of the command line. | Ctrl + A |
| Move the cursor to the end of the command line. | Ctrl + E |
| Move the cursor backwards one word. | Ctrl + B |
| Move the cursor forwards one word. | Ctrl + F |
| Delete the current character. | Ctrl + D |
| Abort current interactive commands, such as when entering multiple lines. If you are not currently within an interactive command such as config or edit, this closes the CLI connection. |
Ctrl + C |
| Continue typing a command on the next line for a multi-line command. For each line that you want to continue, terminate it with a backslash ( \ ). To complete the command line, terminate it by pressing the spacebar and then the Enter key, without an immediately preceding backslash. |
\ then Enter |
Command abbreviation
You can abbreviate words in the command line to their smallest number of non‑ambiguous characters.
For example, the command get system status could be abbreviated to g sy stat.
Adding and removing options from lists
When adding options to a list, such as a user group, using the set command will remove the previous configuration. For example. if you wish to add user D to a user group that already contains members A, B, and C, the command would need to be set member A B C D. If only set member D was used, then all former members would be removed from the group.
However, there are additional commands which can be used instead of set for changing options in a list.
Additional commands for lists
| append | Add an option to an existing list. For example, append member would add user D to a user group while all previous group members are retained |
| select | Clear all options except for those specified. For example, if a group contains members A, B, C, and D and you remove all users except for B, use the command select member B. |
| unselect | Remove an option from an existing list. For example, unselect member A would remove member A from a group will all previous group members are retained. |
Environment variables
The CLI supports the following environment variables. Variable names are case-sensitive.
Environment variables
| $USERFROM | The management access type (ssh, telnet, jsconsole for the CLI Console widget in the web-based manager, and so on) and the IP address of the administrator that configured the item. |
| $USERNAME | The account name of the administrator that configured the item. |
| $SerialNum | The serial number of the FortiGate unit. |
For example, the FortiGate unit’s host name can be set to its serial number.
config system global
set hostname $SerialNum
end
Special characters
The characters <, >, (,), #, ', and “ are not permitted in most CLI fields. These characters are special characters, also known as reserved characters.
You may be able to enter special character as part of a string’s value by using a special command, enclosing it in quotes, or preceding it with an escape sequence — in this case, a backslash ( \ ) character.
In other cases, different keystrokes are required to input a special character. If you need to enter ? as part of config, you first need to input CTRL-V. If you enter the question mark (?) without first using CTRL-V, the question mark has a different meaning in CLI: it will show available command options in that section.
For example, if you enter ? without CTRL-V:
edit "*.xe
token line: Unmatched double quote.
If you enter ? with CTRL-V:
edit "*.xe?"
new entry '*.xe?' added
Entering special characters
| Character | Keys |
|---|---|
| ? | Ctrl + V then ? |
| Tab | Ctrl + V then Tab |
| Space (to be interpreted as part of a string value, not to end the string) |
Enclose the string in quotation marks: "Security Administrator”.Enclose the string in single quotes: 'Security Administrator'.Precede the space with a backslash: Security\ Administrator. |
| ' (to be interpreted as part of a string value, not to end the string) |
\' |
| " (to be interpreted as part of a string value, not to end the string) |
\" |
| \ | \\ |
Using grep to filter get and show command output
In many cases, the get and show (and diagnose) commands may produce a large amount of output. If you are looking for specific information in a large get or show command output, you can use the grep command to filter the output to only display what you are looking for. The grep command is based on the standard UNIX grep, used for searching text output based on regular expressions.
Use the following command to display the MAC address of the FortiGate unit internal interface:
get hardware nic internal | grep Current_HWaddr
Current_HWaddr 00:09:0f:cb:c2:75
Use the following command to display all TCP sessions in the session list and include the session list line number in the output
get system session list | grep -n tcp
Use the following command to display all lines in HTTP replacement message commands that contain URL (upper or lower case):
show system replacemsg http | grep -i url
There are three additional options that can be applied to grep:
-A <num> After
-B <num> Before
-C <num> Context
The option -f is also available to support Fortinet contextual output, in order to show the complete configuration. The following example shows the difference in output when -f option is used versus when it is not.
Using -f:
show | grep -f ldap-group1
config user group
edit "ldap-group1"
set member "pc40-LDAP"
next
end
config firewall policy
edit 2
set srcintf "port31"
set dstintf "port32"
set srcaddr "all"
set action accept
set identity-based enable
set nat enable
config identity-based-policy
edit 1
set schedule "always"
set groups "ldap-group1"
set dstaddr "all"
set service "ALL"
next
end
next
end
Without using -f:
show | grep ldap-group1
edit "ldap-group1"
set groups "ldap-group1"
Language support and regular expressions
Characters such as ñ, é, symbols, and ideographs are sometimes acceptable input. Support varies by the nature of the item being configured. CLI commands, objects, field names, and options must use their exact ASCII characters, but some items with arbitrary names or values may be input using your language of choice. To use other languages in those cases, you must use the correct encoding.
Input is stored using Unicode UTF-8 encoding but is not normalized from other encodings into UTF-8 before it is stored. If your input method encodes some characters differently than in UTF-8, your configured items may not display or operate as expected.
Regular expressions are especially impacted. Matching uses the UTF‑8 character values. If you enter a regular expression using another encoding, or if an HTTP client sends a request in an encoding other than UTF‑8, matches may not be what you expect.
For example, with Shift-JIS, backslashes ( \ ) could be inadvertently interpreted as the symbol for the Japanese yen ( ¥ ) and vice versa. A regular expression intended to match HTTP requests containing money values with a yen symbol therefore may not work it if the symbol is entered using the wrong encoding.
For best results, you should:
- use UTF-8 encoding, or
- use only the characters whose numerically encoded values are the same in UTF‑8, such as the US-ASCII characters that are also encoded using the same values in ISO 8859-1, Windows code page 1252, Shift-JIS and other encodings, or
- for regular expressions that must match HTTP requests, use the same encoding as your HTTP clients.
|
|
HTTP clients may send requests in encodings other than UTF-8. Encodings usually vary by the client’s operating system or input language. If you cannot predict the client’s encoding, you may only be able to match any parts of the request that are in English, because regardless of the encoding, the values for English characters tend to be encoded identically. For example, English words may be legible regardless of interpreting a web page as either ISO 8859-1 or as GB2312, whereas simplified Chinese characters might only be legible if the page is interpreted as GB2312. |
If you configure your FortiGate unit using other encodings, you may need to switch language settings on your management computer, including for your web browser or Telnet/SSH client. For instructions on how to configure your management computer’s operating system language, locale, or input method, see its documentation.
If you choose to configure parts of the FortiGate unit using non-ASCII characters, verify that all systems interacting with the FortiGate unit also support the same encodings. You should also use the same encoding throughout the configuration if possible in order to avoid needing to switch the language settings of the web-based manager and your web browser or Telnet/SSH client while you work.
Similarly to input, your web browser or CLI client should usually interpret display output as encoded using UTF-8. If it does not, your configured items may not display correctly in the web-based manager or CLI. Exceptions include items such as regular expressions that you may have configured using other encodings in order to match the encoding of HTTP requests that the FortiGate unit receives.
To enter non-ASCII characters in the CLI Console widget
- On your management computer, start your web browser and go to the URL for the FortiGate unit’s web-based manager.
- Configure your web browser to interpret the page as UTF-8 encoded.
- Log in to the FortiGate unit.
- Go to System > Dashboard > Status.
- In title bar of the CLI Console widget, click Edit (the pencil icon).
- Enable Use external command input box.
- Select OK.
- The Command field appears below the usual input and display area of the CLI Console widget.
- In Command, type a command.
Entering encoded characters (CLI Console widget):

- Press Enter.
In the display area, the CLI Console widget displays your previous command interpreted into its character code equivalent, such as:
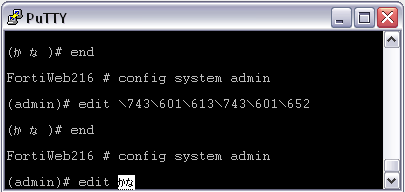
edit \743\601\613\743\601\652
and the command’s output.
To enter non-ASCII characters in a Telnet/SSH client
- On your management computer, start your Telnet or SSH client.
- Configure your Telnet or SSH client to send and receive characters using UTF-8 encoding.
Support for sending and receiving international characters varies by each Telnet/SSH client. Consult the documentation for your Telnet/SSH client.
- Log in to the FortiGate unit.
- At the command prompt, type your command and press Enter.
Entering encoded characters (PuTTY):
You may need to surround words that use encoded characters with single quotes ( ' ).
Depending on your Telnet/SSH client’s support for your language’s input methods and for sending international characters, you may need to interpret them into character codes before pressing Enter.
For example, you might need to enter:
edit '\743\601\613\743\601\652'
- The CLI displays your previous command and its output.
Screen paging
You can configure the CLI to pause after displaying each page’s worth of text when displaying multiple pages of output. When the display pauses, the last line displays ‑‑More‑‑. You can then either:
- press the spacebar to display the next page.
- type
Qto truncate the output and return to the command prompt.
This may be useful when displaying lengthy output, such as the list of possible matching commands for command completion, or a long list of settings. Rather than scrolling through or possibly exceeding the buffer of your terminal emulator, you can simply display one page at a time.
To configure the CLI display to pause when the screen is full:
config system console
set output more
end
Baud rate
You can change the default baud rate of the local console connection.
To change the baud rate enter the following commands:
config system console
set baudrate {115200 | 19200 | 38400 | 57600 | 9600}
end
Editing the configuration file on an external host
You can edit the FortiGate configuration on an external host by first backing up the configuration file to a TFTP server. Then edit the configuration file and restore it to the FortiGate unit.
Editing the configuration on an external host can be timesaving if you have many changes to make, especially if your plain text editor provides advanced features such as batch changes.
To edit the configuration on your computer
- Use
execute backupto download the configuration file to a TFTP server, such as your management computer. - Edit the configuration file using a plain text editor that supports Unix-style line endings.
|
|
Do not edit the first line. The first line(s) of the configuration file (preceded by a # character) contains information about the firmware version and FortiGate model. If you change the model number, the FortiGate unit will reject the configuration file when you attempt to restore it. |
- Use
execute restoreto upload the modified configuration file back to the FortiGate unit.
The FortiGate unit downloads the configuration file and checks that the model information is correct. If it is, the FortiGate unit loads the configuration file and checks each command for errors. If a command is invalid, the FortiGate unit ignores the command. If the configuration file is valid, the FortiGate unit restarts and loads the new configuration.
Using Perl regular expressions
Some FortiGate features, such as spam filtering and web content filtering can use either wildcards or Perl regular expressions.
See http://perldoc.perl.org/perlretut.html for detailed information about using Perl regular expressions. For more information on using Perl expressions see the Security Profiles chapter of The Handbook.
Differences between regular expression and wildcard pattern matching
In Perl regular expressions, the period (‘.’) character refers to any single character. It is similar to the question mark (‘?’) character in wildcard pattern matching. As a result:
fortinet.comnot only matchesexample.combut also matchesexampleacom,examplebcom,exampleccomand so on.
To match a special character such as the period ('.') and the asterisk (‘*’), regular expressions use the slash (‘\’) escape character. For example:
- To match
example.com, the regular expression should beexample\.com.
In Perl regular expressions, the asterisk (‘*’) means match 0 or more times of the character before it, not 0 or more times of any character. For example:
exam*\.commatchesexammmm.combut does not matcheample.com.
To match any character 0 or more times, use ‘.*’ where ‘.’ means any character and the ‘*’ means 0 or more times. For example:
- the wildcard match pattern
exam*.comis equivalent to the regular expressionexam.*\.com.
Word boundary
In Perl regular expressions, the pattern does not have an implicit word boundary. For example, the regular expression “test” not only matches the word “test” but also matches any word that contains the word “test” such as “atest”, “mytest”, “testimony”, “atestb”. The notation “\b” specifies the word boundary. To match exactly the word “test”, the expression should be \btest\b.
Case sensitivity
Regular expression pattern matching is case sensitive in the Web and Spam filters. To make a word or phrase case insensitive, use the regular expression /i. For example, /bad language/i will block all instances of “bad language” regardless of case.
Perl regular expression examples
| Expression | Matches |
|---|---|
| abc | abc (that exact character sequence, but anywhere in the string) |
| ^abc | abc at the beginning of the string |
| abc$ | abc at the end of the string |
| a|b | either of a and b |
| ^abc|abc$ | the string abc at the beginning or at the end of the string |
| ab{2,4}c | an a followed by two, three or four b's followed by a c |
| ab{2,}c | an a followed by at least two b's followed by a c |
| ab*c | an a followed by any number (zero or more) of b's followed by a c |
| ab+c | an a followed by one or more b's followed by a c |
| ab?c | an a followed by an optional b followed by a c; that is, either abc or ac |
| a.c | an a followed by any single character (not newline) followed by a c |
| a\.c | a.c exactly |
| [abc] | any one of a, b and c |
| [Aa]bc | either of Abc and abc |
| [abc]+ | any (nonempty) string of a's, b's and c's (such as a, abba, acbabcacaa) |
| [^abc]+ | any (nonempty) string which does not contain any of a, b and c (such as defg) |
| \d\d | any two decimal digits, such as 42; same as \d{2} |
| /i | makes the pattern case insensitive. For example, /bad language/i blocks any instance of “bad language” regardless of case. |
| \w+ | a "word": a nonempty sequence of alphanumeric characters and low lines (underscores), such as foo and 12bar8 and foo_1 |
| 100\s*mk | the strings 100 and mk optionally separated by any amount of white space (spaces, tabs, newlines) |
| abc\b | abc when followed by a word boundary (e.g. in abc! but not in abcd) |
| perl\B | perl when not followed by a word boundary (e.g. in perlert but not in perl stuff) |
| \x | tells the regular expression parser to ignore white space that is neither backslashed nor within a character class. You can use this to break up your regular expression into (slightly) more readable parts. |