Redundant Internet Installation in NAT/Route Mode
| If you have previously configured your FortiGate using the standard installation, you will have to delete all routes and policies that refer to an interface that will be used to provide redundant Internet. This includes the default Internet access policy that is included on many FortiGate models. |
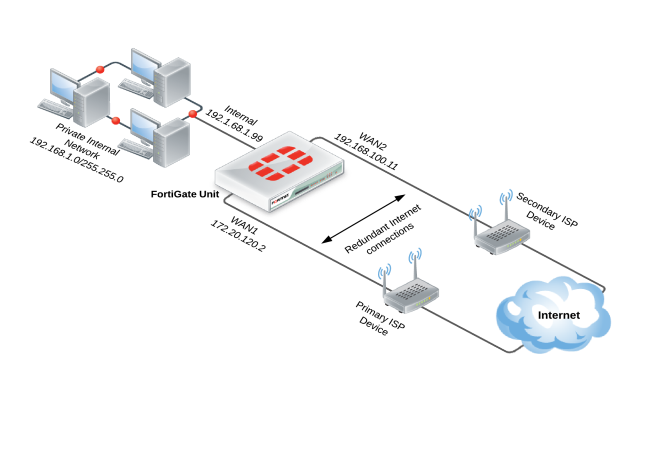
1. Connect the FortiGate’s Internet-facing interfaces (typically WAN1 and WAN2) to your ISP-supplied equipment.
2. Go to System > Network > WAN Link Load Balancing to create a WAN link interface, which is used to group multiple Internet connections together so that the FortiGate unit can treat them as a single interface.
| If you are using FortiOS 5.2.0, go to System > Network > Interfaces and select Create New > Virtual WAN to create a virtual WAN link (this feature was renamed WAN link interface in FortiOS 5.2.1). |
3. Select an appropriate method of WAN Load Balancing from the following options:
• Source IP based - The next hop is based on the traffic’s source IP address.
• Weighted Round Robin - Weight is input for all the active members of the WAN link.
• Spill-over - A traffic cap is defined for active members; when it is exceeded, the traffic will automatically activate the standby link.
• Source-Destination IP based - The next hop is based on both the traffic’s source and destination IP address.
• Measured-Volume based - A volume ratio is set for each active member of the WAN link.
4. Add your Internet-facing interfaces to the WAN link interface, configuring load balancing as required for each interface.
5. Go to Router > Static > Static Routes and create a new default route. Set Device to the virtual WAN link.
6. If your network uses IPv4 addresses, go to Policy & Objects > Policy > IPv4 and select Create New to add a security policy that allows users on the private network to access the Internet.
If your network uses IPv6 addresses, go to Policy & Objects > Policy > IPv6 and select Create New to add a security policy that allows users on the private network to access the Internet. If the IPv6 menu option is not available, go to System > Config > Features, turn on IPv6, and select Apply. For more information on IPv6 networks, see the IPv6 Handbook.
In the policy, set the Incoming Interface to the internal interface and the Outgoing Interface to the WAN link interface. You will also need to set Source Address, Destination Address, Schedule, and Service according to your network requirements. You can set these fields to the default all/ANY settings for now but should create the appropriate objects later after the policies have been verified.
Make sure the Action is set to ACCEPT. Turn on NAT and make sure Use Destination Interface Address is selected. Select OK.
| It is recommended to avoid using any security profiles, such as AntiVirus or web filtering, until after you have successfully installed the FortiGate unit. After the installation is verified, you can apply any required security profiles. For more information about using security profiles, see the Security Profiles handbook. |
Results
Users on the internal network are now able to browse the Internet. They should also be able to connect to the Internet using any other protocol or connection method that you defined in the security policy.
The amount of traffic will use an individual member of the WAN link interface will depend on the load balancing method you selected. You can view this usage by going to System > FortiView > All Sessions and viewing the Dst Interface column. If this column is not shown, right-click on the title row and select Dst Interface from the dropdown menu. Scroll to the bottom of the menu and select Apply.
 using redundant Internet
using redundant Internet using redundant Internet
using redundant Internet using redundant Internet
using redundant Internet