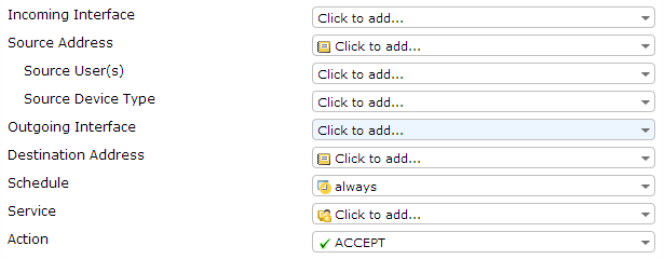
Unified Policy Management
The different creation pages in the web-based manager for policy types and subtypes (user-identity, device identity, and VPN) have been merged into a single main policy creation page. New fields have been added for Source User(s) and Source Device Type that remove the need for multiple authentication rules in a single police. This allows for greater control and customization of policies, as a combination of these source types can be used in a single policy rather than having to pick one type.
If both Source User(s) and Source Device Type are set, then traffic must match both fields in order to be accepted by the policy. Both these fields are optional; only Source Address must be set.
For policies that require user or device authentication, there is an implicit fall-through to allow traffic to be checked against other policies if it does not match the authentication requirements. This option cannot be disabled and the CLI command set fall-through-unauthenticated has been removed.
For more information about security policies in FortiOS 5.2, please see the FortiGate Cookbook recipe
Creating and ordering security policies to provide access to different users and devices, found at
docs.fortinet.com.
To create a policy for SSL VPNs, an SSL VPN interface is created and used as the source interface. For more information about this interface creation, see
“SSL VPN Configuration”.