NP4 IPsec VPN offloading configuration example
Hardware accelerated IPsec processing, involving either partial or full offloading, can be achieved in either tunnel or interface mode IPsec configurations.
To achieve offloading for both encryption and decryption:
• In Phase 1 configuration’s Advanced section, Local Gateway IP must be specified as an IP address of a network interface associated with a port attached to a network processor. (In other words, if Phase 1’s Local Gateway IP is Main Interface IP, or is specified as an IP address that is not associated with a network interface associated with a port attached to a network processor, IPsec network processing is not offloaded.)
• In Phase 2 configuration’s P2 Proposal section, if the checkbox “Enable replay detection” is enabled, enc-offload-antireplay and dec-offload-antireplay must be set to enable in the CLI.
• offload-ipsec-host must be set to enable in the CLI.
This section contains example IPsec configurations whose IPsec encryption and decryption processing is hardware accelerated by an NP4 unit contained in a FortiGate-5001B at both ends of the VPN tunnel.
| Hardware accelerated IPsec VPN does not require both tunnel endpoints to have the same network processor model. However, if hardware is not symmetrical, the packet forwarding rate is limited by the slower side. |
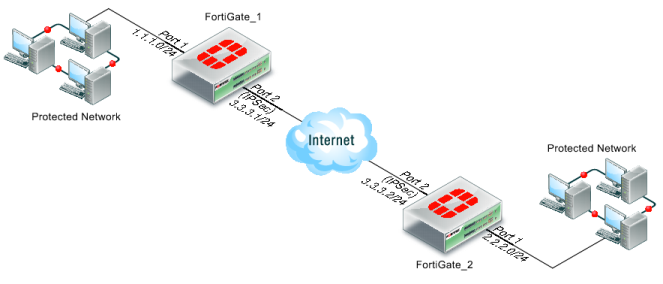
Figure 141: Example network topology for offloaded IPsec processing
Table 45: Example ports and IP addresses for offloaded IPsec processing
| FortiGate_1 | FortiGate_2 |
| Port | IP | Port | IP |
IPsec tunnel | FortiGate-5001B port 2 | 3.3.3.1/24 | FortiGate-5001B port 2 | 3.3.3.2/24 |
Protected network | FortiGate-5001B port 1 | 1.1.1.0/24 | FortiGate-5001B port 1 | 2.2.2.0/24 |
This section includes the following topics: