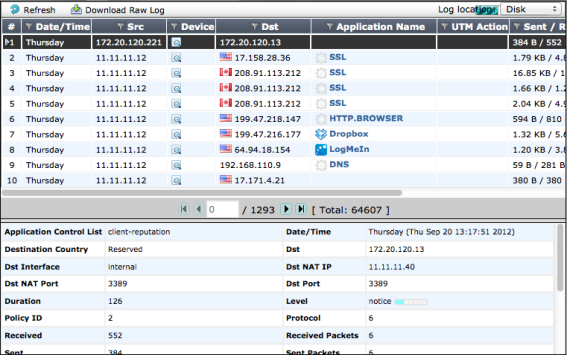
Log Viewer Improvements
In FortiOS 5.0, the Log & Report menu provides access to the following types of log messages:
• Traffic log
• Forward Traffic - log messages for traffic passing through the FortiGate unit. Includes traffic log messages as well as Security log messages so that you can view messages about Security events (such as a message indicating that a virus was found) in the same location as the traffic log messages that recorded the current traffic at the time. From the forward traffic log viewer, you can also view content logs and quarantined files. Forward traffic log messages also include log messages created when you enable logging for the IPv4 and IPv6 security policy implicit security policies.
• Local Traffic - Log messages for traffic terminating at the FortiGate unit. All traffic terminating at the FortiGate unit is allowed or denied by a local in policy. To view local in policies go to Policy > Policy > Local In Policy. You can enable and disable logging for local in traffic from here as well.
• Multicast Traffic - Log messages for multicast traffic passing through the FortiGate unit and allowed by multicast traffic policies
• Invalid Packets - Log messages recorded when the FortiGate unit receives invalid packets.
• Event log - Event log messages organized into the following categories:
• System
• Router
• VPN
• User
• WAN Opt. & Cache
• WiFi
From each of these log message viewers, you can download raw log messages, adjust the column settings to display the ones you are most interested in, filter the messages according to a wide range of criteria and display detailed information for a selected log message. In addition, you can control the source of the log messages that are displayed. For example, setting the log location source can be the disk, if your FortiGate unit has available internal storage.
Other logging improvements include:
• New event log types including event logs for FortiClient usage.
• Traffic log messages for packets blocked by the implicit policies that appear at the bottom of IPv4 and IPv6 policy lists. You can enable logging for these policies by editing them and selecting Log Violation Traffic.
• When you enable logging on a security policy and a session begins, the FortiGate unit logs that session as well as logging when that session closes. These traffic logs contain the log fields status=start, when a session has started, and status=close, when the session ends.
• Email filter log messages now contain a new field, the cc field, which provides all the email addresses that were copied (or cc'd) to the original email message.
• There are two new event logs that contain information about the FSSO polling daemon: one event log is recorded when a logged on user adds or replaces an old user; the second event log is recorded when an old user is logged off because of inactivity or when replaced.
From the CLI, all of these and some other options are available from the new config log setting command. This command configures traffic logging settings per VDOM.