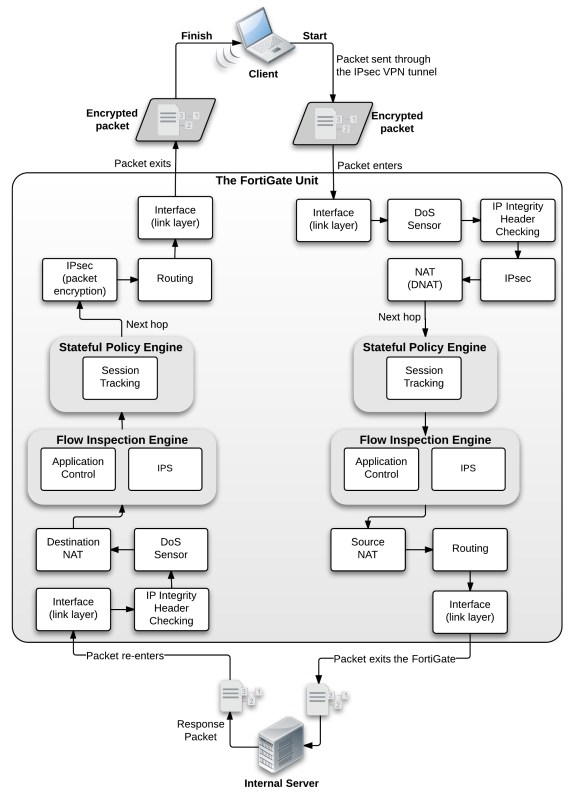
Example 3: Dialup IPsec VPN with application control
This example includes the following steps:
1. FortiGate unit receives IPsec packet from Internet
2. Packet intercepted by FortiGate unit interface
2.1 Link level CRC and packet size checking. If the size is correct, the packet continues, otherwise it is dropped.
3. DoS sensor - checks are done to ensure the sender is valid and not attempting a denial of service attack.
4. IP integrity header checking, verifying the IP header length, version and checksums.
5. IPsec
5.1 Determines that packet matched IPsec phase 1 configuration
5.2 Unencrypted packet
6. Next hop route
7. Stateful policy engine
7.1 Session tracking
8. Flow inspection engine
8.1 IPS
8.2 Application control
9. Source NAT
10. Routing
11. Interface transmission to network
12. Packet forwarded to internal server
Response from server
1. Server sends response packet
2. Packet intercepted by FortiGate unit interface
2.1 Link level CRC and packet size checking
3. IP integrity header checking.
4. DoS sensor
5. Flow inspection engine
5.1 IPS
5.2 Application control
6. Stateful policy engine
6.1 Session tracking
7. Next hop route
8. IPsec
8.1 Encrypts packet
9. Routing
10. Interface transmission to network
11. Encrypted Packet returns to internet
Figure 322 illustrates the process.