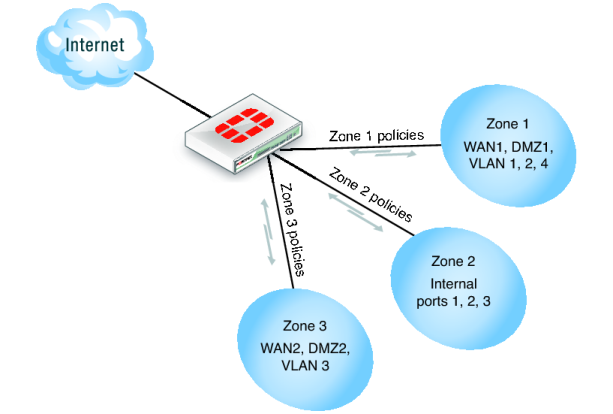
Zones
Zones are a group of one or more FortiGate interfaces, both physical and virtual, that you can apply security policies to control inbound and outbound traffic. Grouping interfaces and VLAN subinterfaces into zones simplifies the creation of security policies where a number of network segments can use the same policy settings and protection profiles. When you add a zone, you select the names of the interfaces and VLAN subinterfaces to add to the zone. Each interface still has its own address and routing is still done between interfaces, that is, routing is not affected by zones. Security policies can also be created to control the flow of intra-zone traffic.
For example, in the illustration below, the network includes three separate groups of users representing different entities on the company network. While each group has its own set of port and VLANs, in each area, they can all use the same security policy and protection profiles to access the Internet. Rather than the administrator making nine separate security policies, he can add the required interfaces to a zone, and create three policies, making administration simpler.
You can configure policies for connections to and from a zone, but not between interfaces in a zone. Using the above example, you can create a security policy to go between zone 1 and zone 3, but not between WAN2 and WAN1, or WAN1 and DMZ1.
See Also
This example explains how to set up a zone to include the Internal interface and a VLAN.
To create a zone - web-based manager
1. Go to System > Network > Interface.
2. Select the arrow on the Create New button and select Zone.
3. Enter a zone name of Zone_1.
4. Select the Internal interface and the virtual LAN interface vlan_accounting created previously.
5. Select OK.
To create a zone - CLI
config system zone
edit Zone_1
set interface internal VLAN_1
end