Adding DoS Anomaly protection to a FortiGate interface
New DoS policies allow you to apply DoS anomalies to all traffic that hits a FortiGate interface. This is the only way to apply DoS anomaly protection.
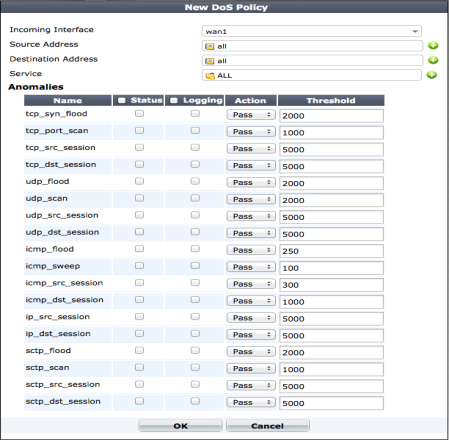
To add a DoS policy go to Policy > Policy > DoS Policy and select Create New to add a new DoS policy. Select the FortiGate interface to add the policy to and select the source and destination addresses and services that will match the packets that you want to apply DoS anomalies to.
Enable one or more DoS anomalies. For each anomaly you can enable logging, set the action to pass or block and change the threshold.
Use the following command to add a DoS policy from the CLI that adds syn flood protection for all traffic hitting the wan2 interface:
config firewall DoS-policy
edit 1
set interface wan2
set srcaddr all
set dstaddr all
set service ALL
config anomaly
edit tcp_syn_flood
set status enable
set log enable
set action block
end
end
DoS sensors no longer available. DoS policies are the most common method for applying DoS anomalies in FortiOS 5.0.
You can also use the following command to apply DoS anomalies to a one-arm sniffer configuration.
config firewall sniffer
Interface policies are still available in FortiOS 5.0 from the CLI using the following commands:
config firewall interface-policy
config firewall interface-policy6
You can use interface policies to apply application control, intrusion protection, virus scanning, web filtering, email filtering and data leak protection to traffic received by an interface.
The following commands are also available for adding sniffer interface policies, which are similar to interface policies:
config firewall sniff-interface-policy
config firewall sniff-interface-policy6
All of these command have similar syntax for applying Security Features to traffic connecting to or sniffed by a FortiGate interface.