Example
In this example, HTTPS and DNS traffic is sent from User 1 to FortiGate B, through FortiGate A. DSCP is enabled for both traffic directions on FortiGate A, and enabled only for reply traffic on FortiGate B. FortiGate A contains the following configuration:
config firewall policy
edit 2
set srcintf port6
set dstintf port3
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-forward enable
set diffserv-rev enable
set diffservcode-forward 101110
set diffservcode-rev 101111
end
FortiGate B contains the following configuration:
config firewall policy
edit 2
set srcintf wan2
set dstintf internal
set src addr all
set dstaddr all
set action accept
set schedule always
set service ANY
set diffserv-rev enable
set diffservcode-rev 101101
end
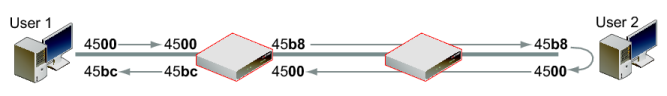
As a result, FortiGate A changes the DSCP field for both outgoing traffic and its reply traffic, but FortiGate B changes the DSCP field only for reply traffic which passes through its internal interface. Since the example traffic does not pass through the internal interface, FortiGate B does not mark the packets. The binary DSCP values in this configuration map to the following hexadecimal TOS field values:
• DSCP 000000 is TOS field 0x00
• DSCP 101101 is TOS field 0xb4, which is configured on FortiGate B but not observed by the sniffer because the example traffic originates from the FortiGate unit itself, and therefore does not match that security policy.
• DSCP 101110 is TOS field 0xb8, the recommended DSCP value for expedited forwarding (EF)
• DSCP 101111 is TOS field 0xbc
If you sent HTTPS or DNS traffic from User 1 to FortiGate B, the following would illustrate the IP headers observed for the request and the reply by sniffers on each of FortiGate A's and FortiGate B's network interfaces. The right-most two digits of each IP header are the TOS field, which contains the DSCP value.