SSH inspection
FortiOS 5.0 includes a new SSH proxy, available on selected models, that supports decrypting and inspecting SSH sessions to block or log the following:
• SSH remote execution
• Port forwarding
• SSH remote shell
• x11 server forwarding
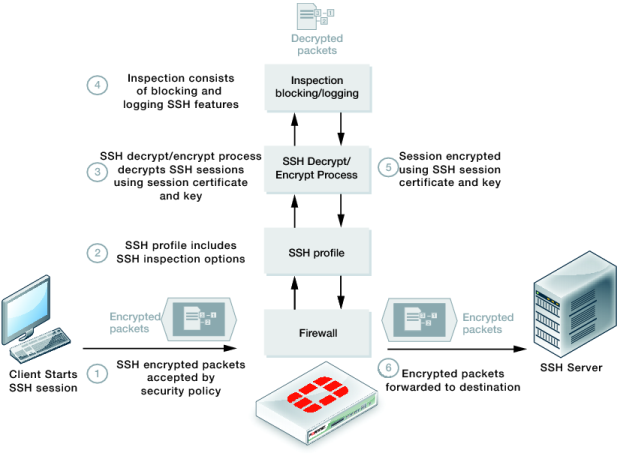
Similar to SSL content inspection, the SSH proxy intercepts the SSH key exchange between the SSH client and server when an SSH session is being set up. All traffic that is part of the SSH session is decrypted by the SSH proxy and SSH inspection features are applied according to the SSH profile in the security policy that accepts the SSH traffic. After inspection, the session is re-encrypted and forwarded to the recipient.
SSH inspection is enabled by default in a SSL/SSH inspection profile.
Figure 38: SSH inspection
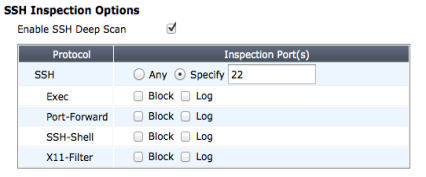
To configure SSH inspection, go to Policy > Policy > SSL/SSH Inspection and create or edit an SSL/SSH Inspection profile and ensure that SSH Inspection Options are enabled. Then configure the port or ports to look for SSH traffic on. The default port is 22 but you can add more. You can then block or log Exec commands, port-forwarding, SSH shells, and X11 FIlters.
Then add this profile to security policy that accepts SSH traffic. Enable the required Security Profiles in the policy.
From the CLI:
config firewall profile-protocol-options
edit new-profile
config ssh
set port <number> <number> ... (default is port 22)
set inspect-all {enable | disable}
set options {allow-invalid-server-cert | ssl-ca-list }
set oversize-limit <size>
set block {exe | port-forward | ssh-shell | x11-filter}
end