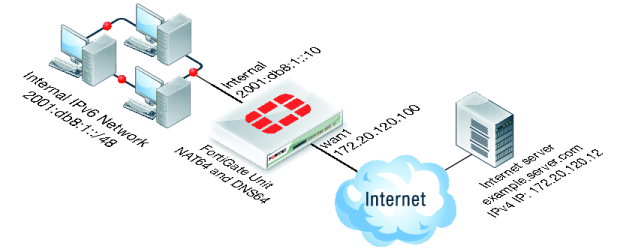
NAT64 and DNS64
NAT64 is used to translate IPv6 addresses to IPv4 addresses so that a client on an IPv6 network can communicate transparently with a server on an IPv4 network. NAT64 is usually implemented in combination with DNS64. DNS64 synthesizes AAAA records from A records and is used to synthesize IPv6 addresses for hosts that only have IPv4 addresses.
With a NAT64 and DNS64 configuration in place on a FortiGate unit, clients on an IPv6 network can transparently connect to addresses on an IPv4 network. NAT64 and DNS64 perform IPv4 to IPv6 transition, allowing clients that have already switched to IPv6 addresses to continue communicating with servers that still use IPv4 addresses.
To configure NAT64 to allow a host on the IPv6 network to connect to the Internet server
In this example the Internal IPv6 network address is 2001:db8:1::/48 and the external IPv4 network address is 172.20.120.0/24. NAT64 is configured to allow a user on the internal network to connect to the server at IPv4 address 172.20.120.12. In this configuration, sessions exiting the wan1 interface must have their source address changed to and IPv4 address in the range 172.20.120.200 to 172.20.120.210.
1. Enter the following command to enable NAT64.
config system nat64
set status enable
end
| Enabling NAT64 with the config system nat64 command means that all IPv6 traffic received by the current VDOM can be subject to NAT64 if the source and destination address matches an NAT64 security policy. By default, the setting always-senthetize-aaaa-record is not enabled. With this setting disabled, the DNS proxy will attempt to find an AAAA records for queries to domain names and therefore resolve the host names to IPv6 addresses. If the DNS proxy cannot find an AAAA record, it synthesizes one by adding the NAT64 prefix to the A record. By using the nat64-prefix option of the config system nat64 command to change the default nat64 prefix (the default is the well known prefix 64:ff9b::/96) and setting always-senthetize-aaaa-record to enable, the DNS proxy does not check for AAAA records and always synthesizes AAAA records. |
As an alternative to the above entry, there is the optional configuration that would allow the resolution of CNAME queries.
config system nat64
set status enable
set nat64-prefix 64:ff9b::/96
set always-synthesize-aaaa-record enable
end
2. Enter the following command to add an IPv6 firewall address for the internal network:
config firewall address6
edit internal-net6
set ip6 2001:db8::/48
end
3. Enter the following command to add an IPv4 firewall address for the external network:
config firewall address
edit external-net4
set subnet 172.20.120.0/24
set associated-interface wan1
end
4. Enter the following command to add an IP pool containing the IPv4 address that the should become the source address of the packets exiting the wan1 interface:
config firewall ippool
edit exit-pool4
set startip 172.20.120.200
set endip 172.20.120.210
end
5. Enter the following command to add a NAT64 policy that allows connections from the internal IPv6 network to the external IPv4 network:
config firewall policy64
edit 0
set srcintf internal
set srcaddr internal-net6
set dstintf wan1
set dstaddr external-net4
set action accept
set schedule always
set service ANY
set logtraffic enable
set ippool enable
set poolname exit-pool4
end
| The srcaddr can be any IPv6 firewall address and the dstaddr can be any IPv4 firewall address. Other NAT64 policy options include fixedport, that can be used to prevent NAT64 from changing the destination port. You can also configure traffic shaping for NAT64 policies. |
How a host on the internal IPv6 network communicates with example.server.com that only has IPv4 address on the Internet
1. The host on the internal network does a DNS lookup for example.server.com by sending a DNS query for an AAAA record for example.server.com.
2. The DNS query is intercepted by the FortiGate DNS proxy.
3. The DNS proxy attempts to resolve the query with a DNS server on the Internet and discovers that there are no AAAA records for example.server.com.
| The previous step is skipped if always-senthetize-aaaa-record is enabled. |
4. The DNS proxy performs an A-record query for example.server.com and gets back an RRSet containing a single A record with the IPv4 address 172.20.120.12.
5. The DNS proxy then synthesizes an AAAA record. The IPv6 address in the AAAA record begins with the configured NAT64 prefix in the upper 96 bits and the received IPv4 address in the lower 32 bits. By default, the resulting IPv6 address is 64:ff9b::172.20.120.12.
6. The host on the internal network receives the synthetic AAAA record and sends a packet to the destination address 64:ff9b::172.20.120.12.
7. The packet is routed to the FortiGate internal interface where it is accepted by the NAT64 security policy.
8. The FortiGate unit translates the destination address of the packets from IPv6 address 64:ff9b::172.20.120.12 to IPv4 address 172.20.120.12 and translates the source address of the packets to 172.20.120.200 (or another address in the IP pool range) and forwards the packets out the wan1 interface to the Internet.