Use case - allowing limited access for unauthenticated users
Consider an office with open use PCs in common areas. Staff and customers do not have to log in to these PCs and can use them for limited access to the Internet. From their desks, employees of this office log into PCs which are logged into the office network. The FortiGate unit on the office network uses single sign-on to get user credentials from the network authentication server.
The open use PCs have limited access to the Internet. Employee PCs can access internal resources and have unlimited access to the Internet.
To support these different levels of access you can add a user identity policy to the top of the policy list that allows authenticated users to access internal resources and to have unlimited access to the Internet. In this policy, select Skip this policy for unauthenticated user.
Add a normal firewall policy below this policy that allows limited access to the Internet.
Sessions from authenticated PCs will be accepted by the User Identity policy. Sessions from unauthenticated PCs will skip the User Identity policy and be accepted by the normal firewall policy.
Figure 116 shows how the FortiGate unit handles packets received from authenticated and unauthenticated users.
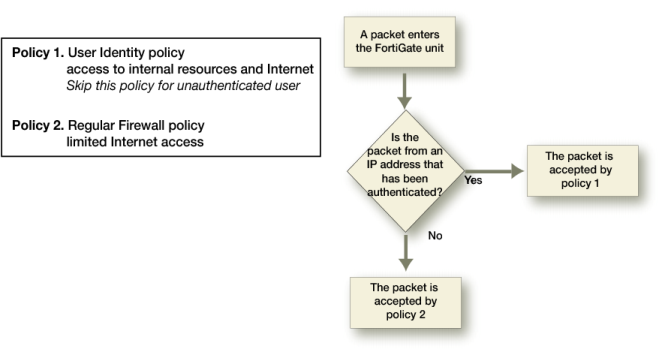 Packet flow for authenticated and unauthenticated users
Packet flow for authenticated and unauthenticated users Packet flow for authenticated and unauthenticated users
Packet flow for authenticated and unauthenticated users Packet flow for authenticated and unauthenticated users
Packet flow for authenticated and unauthenticated users