The Fortinet Security Fabric provides a visionary approach to security that allows your organization to deliver intelligent, powerful, and seamless security. Fortinet offers security solutions for endpoints, access points, network elements, the data center, applications, cloud, and data, designed to work together as an integrated security fabric that can be integrated, analyzed, and managed to provide end-to-end protection for your network. Your organization can also add third-party products that are members of the Fortinet Fabric-Ready Partner Program to the Security Fabric.
All elements in the Security Fabric work together as a team to share policy, threat intelligence, and application flow information. This collaborative approach expands network visibility and provides fast threat detection in real time and the ability to initiate and synchronize a coordinated response, no matter which part of the network is being compromised. The Security Fabric allows your network to automatically see and dynamically isolate affected devices, partition network segments, update rules, push out new policies, and remove malware.
The Security Fabric is designed to cover the entire attack surface and provide you with complete visibility into your network. It allows you to collect, share, and correlate threat intelligence between security and network devices, centrally manage and orchestrate policies, automatically synchronize resources to enforce policies, and coordinate a response to threats detected anywhere across the extended network. The unified management interface provides you with cooperative security alerts, recommendations, audit reports, and full policy control across the Security Fabric that will give you confidence that your network is secure.
To configure the Security Fabric, go to Security Fabric > Settings.

The following options are available:
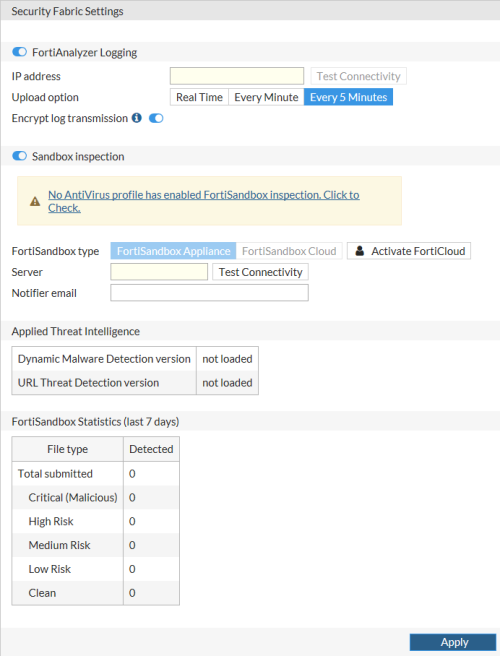
| FortiAnalyzer Logging | Enable to allow the Security Fabric to show logs for the entire Security Fabric. | |
| IP address | Enter the IP address of the FortiAnalyzer unit that you want the Security Fabric to send logs to. Select Test Connectivity to test if the FortiAnalyzer can be contacted. If the FortiAnalyzer functionality has not been enabled on the FortiManager, you will receive an error. |
|
| Upload option | Select how often you want the FortiProxy unit to send logs to the FortiAnalyzer unit: Real Time, Every Minute, or Every 5 Minutes. The default is Every 5 Minutes. | |
| Encrypt log transmission | Enable if you want log transmissions encrypted. The log transmissions are encrypted using SSL. | |
| Sandbox Inspection |
Enable to have the FortiProxy unit send suspicious files to FortiSandbox for inspection and analysis. When a FortiProxy unit sends files for sandbox inspection, the FortiSandbox uses virtual machines (VMs) running different operating systems to test the file and to determine if it is malicious. FortiSandbox can process multiple files simultaneously since the FortiSandbox has a VM pool. The time to process a file depends on hardware and the number of sandbox VMs used to scan the file. It can take 60 seconds to five minutes to process a file. To use sandbox inspection, you need an antivirus profile with FortiSandbox inspection enabled. |
|
| FortiSandbox type |
Select FortiSandbox Appliance or FortiSandbox Cloud. FortiSandbox is available as a physical or virtual appliance (FortiSandbox Appliance) or as a cloud advanced threat protection service (FortiSandbox Cloud). If you want to use FortiSandbox Cloud, you need an active FortiCloud account. If you do not have an active FortiCloud account, select Activate FortiCloud. |
|
| Server | Enter the IP address of the FortiSandbox server. Select Test Connectivity to test if the server can be contacted. | |
| Notifier email | Enter an email address for FortiSandbox notifications. | |
| Applied Threat Intelligence | Reports if Dynamic Malware Detection and URL Threat Detection are loaded and, if loaded, which version. | |
| FortiSandbox Statistics (last 7 days) | The last 7 days of FortiSandbox statistics. When a FortiProxy unit uses sandbox inspection, files are sent to the FortiSandbox. Then the FortiSandbox uses virtual machines (VMs) running different operating systems to test the file, to determine if it is malicious. If the file exhibits risky behavior or is found to contain a virus, a new signature can be added to both the local FortiProxy malware database and the FortiGuard AntiVirus signature database. |
|
| Apply | Select to save your changes. | |