You use web application firewall policies to scan HTTP requests and responses against known attack signatures and methods and filter matching traffic. This section includes the following topics:
A web application firewall (WAF) is a security policy enforcement point positioned between a client endpoint and a web application. The primary purpose is to prevent attacks against the web servers. A WAF is deployed separately from the web application so that the process overhead required to perform security scanning can be offloaded from the web server, and policies can be administered from one platform to many servers.
A WAF uses methods that complement perimeter security systems, such as the FortiGate next-generation firewall. The FortiADC WAF module applies a set of policies to HTTP scanpoints, which are parsed contexts of an HTTP transaction.
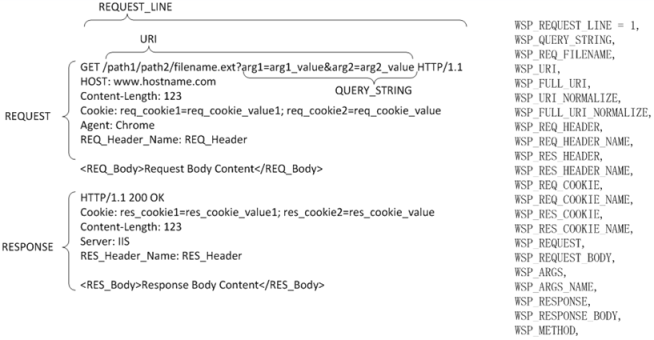
Figure 47 illustrates the scanpoints. In the WAF policy configurations, you have options to enable rules to detect attacks at the request line, query string, filename, URI, request headers, request body, response code, or response body.
In particular:
Policy rules are enforced (action taken) when scanning is completed at four checkpoints:
If the HTTP Request Header violates a rule, and the action is Deny, the attempted session is dropped and scanning for the transaction stops. If the action is Alert, the event is logged and rules processing continues.
Figure 48 shows the relationship between WAF configuration elements. A WAF profile comprises a Web Attack Signature policy, URL Protection policy, HTTP Protocol Constraint policy, SQL/XSS Injection Detection, and Bot Detection policy. The profile is applied to a load balancing virtual server, so all traffic routed to the virtual server is subject to the WAF rules. WAF profiles can be applied to HTTP and HTTPS virtual servers but not HTTP Turbo virtual servers.
The FortiADC WAF includes many predefined configuration elements to help you get started. It includes predefined WAF profiles, predefined Web Attack Signature policies, predefined HTTP Protocol Constraint policies, and predefined SQL/XSS Injection Detection policies.
The severity ratings for predefined Web Attack Signatures and the default severity rating for feature options like SQL/XSS Injection Detection are based on the Open Web Application Security Project (OWASP) Risk Rating Methodology. In order to harmonize the significance of severity levels in logs, we recommend you use this methodology to assign severity for any custom elements you create.
You can create exceptions so that traffic to specific hosts or URL patterns is not subject to processing by WAF rules. Exception lists are processed before traffic is inspected. If an exception applies, the traffic bypasses the WAF module.
Basic Steps
The FortiGuard Web Attack Signature service provides a database of attack signatures that is updated periodically to protect against new kinds of attacks. Table 58 summarizes the categories of threats that are detected by the signatures. The categories are reported in logs.
In the Web Attack Signature policy configuration, you can enable/disable the class of scanpoints and the action when traffic matches signatures.
There are three classes of scanpoints:
Header scanning is always a good practice, so enabling a policy always enables header scanning. Body scanning impacts performance, so you have the option of disabling body scanning if system utilization or latency become an issue.
You can specify separate actions for three event severities:
Table 56 describes the predefined policies. You can select the predefined policies in your WAF profiles, or you can create policies that enable a different set of scan classes or a different action. In this release, you cannot exclude individual signatures or create custom signatures. You can enable or disable the scan classes.
| Policy | Status | Action |
|---|---|---|
|
High-Level-Security |
Scan HTTP header—Enabled. Scan HTTP Request Body—Enabled. Scan HTTP Response Body—Disabled. |
High Severity Action—Deny. Medium Severity Action—Deny. Low Severity Action—Alert. |
|
Medium-Level-Security |
Scan HTTP header—Enabled. Scan HTTP Request Body—Enabled. Scan HTTP Response Body—Disabled. |
High Severity Action—Deny. Medium Severity Action—Alert. Low Severity Action—Alert. |
|
Alert-Only |
Scan HTTP header—Enabled. Scan HTTP Request Body—Disabled. Scan HTTP Response Body—Disabled. |
High Severity Action—Alert. Medium Severity Action—Alert. Low Severity Action—Alert. |
Before you begin:
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
|
Status |
Enable/disable scanning against the signature database. This includes HTTP header scanning but not HTTP body scanning. |
|
Request Body Status |
Enable/disable scanning of the HTTP request body. |
|
Response Body Status |
Enable/disable scanning of the HTTP response body. |
|
High Severity Action |
The default is alert, but we recommend you deny traffic that matches high severity signatures. |
|
Medium Severity Action |
The default is alert. For stricter security, you can deny traffic that matches medium severity signatures. |
|
Low Severity Action |
The default is alert. Recommended for low severity signatures. |
| Signature | |
| Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
| Status | Enable/disable the signature. |
| Exception Name | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
| Description | A string to describe the purpose of the configuration, to help you and other administrators more easily identify its use. |
Table 58 summarizes the categories of threats that are detected by the signatures.
| Category (ID) | Subcategory (ID) |
|---|---|
|
Cross Site Scripting (1) |
|
|
SQL Injection (2) |
|
|
Generic Attacks (3) |
OS Command Injection (1) |
|
Coldfusion Injection (2) |
|
|
LDAP Injection (3) |
|
|
Command Injection (4) |
|
|
Session Fixation (5) |
|
|
File Injection (6) |
|
|
PHP Injection (7) |
|
|
SSI Injection (8) |
|
|
UPDF XSS (9) |
|
|
Email Injection (10) |
|
|
HTTP Response Splitting (11) |
|
|
RFI Injection (12) |
|
|
|
|
|
Trojans (4) |
|
|
Information Disclosure (5) |
Zope Information Leakage (13) |
|
CF Information Leakage (14) |
|
|
PHP Information Leakage (15) |
|
|
ISA Server Existence Revealed (16) |
|
|
Microsoft Office Document Properties Leakage (17) |
|
|
CF Source Code Leakage (18) |
|
|
IIS Information Leakage (19) |
|
|
Weblogic information leakage (20) |
|
|
Generic Filename and Directory leakage (21) |
|
|
ASP/JSP Source Code Leakage (22) |
|
|
PHP Source Code Leakage (23) |
|
|
SQL Error leakage (24) |
|
|
HTTP Header Leakage (25) |
|
|
WordPress Leakage (26) |
|
|
Known Exploits (6) |
Oracle 9i (27) |
|
Coppermine Photo Gallery (28) |
|
|
Netscape Enterprise Server (29) |
|
|
Cisco IOS HTTP Service (30) |
|
|
Microsoft SQL Server (31) |
|
|
HP OpenView Network Node Manager (32) |
|
|
Best Sofrware SalesLogix (33) |
|
|
IBM Lotus Domino Web Server (34) |
|
|
Microsoft IIS (35) |
|
|
Microsoft Windows Media Services (36) |
|
|
Dave Carrigan Auth_LDAP (37) |
|
|
427BB 38) |
|
|
RaXnet Cacti Graph (39) |
|
|
CHETCPASSWD (40) |
|
|
SAP (41) |
|
|
Credit Card Detection (7) |
|
|
Bad Robot (8) |
|
URL protection policies can filter HTTP requests that match specific character strings and file extensions.
Before you begin:
After you have configured URL protection policies, you can select them in WAF profiles.
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
|
URL Access Rule |
|
|
Full URL Pattern |
Matching string. Regular expressions are supported. |
|
Action |
The default is alert. |
|
Severity |
The default is low. |
| Exception Name | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
|
File Extension Rule |
|
|
File Extension Pattern |
Matching string. Regular expressions are supported. |
|
Action |
The default is alert. |
|
Severity |
The default is low. |
| Exception Name | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
The HTTP Protocol Constraint policy includes the following rules:
Table 60 describes the predefined policies.
| Predefined Rules | Description |
|---|---|
|
High-Level-Security |
Protocol constraints enabled with default values. Action is set to deny. Severity is set to high. |
|
Medium-Level-Security |
Protocol constraints enabled with default values. Action is set to alert. Severity is set to medium. |
|
Alert-Only |
Protocol constraints enabled with default values. Action is set to alert. Severity is set to low. |
If desired, you can create user-defined rules to filter traffic with invalid HTTP request methods or drop packets with the specified server response codes.
Before you begin:
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
|
Request Parameters |
|
|
Maximum URI Length |
Maximum characters in an HTTP request URI. The default is 2048. The valid range is 1-8192. |
| Illegal Host Name | Enable/disable hostname checks. A domain name must consist of only the ASCII alphabetic and numeric characters, plus the hyphen. The hostname is checked against the set of characters allowed by the RFC 2616. Disallowed characters, such as non-printable ASCII characters or other special characters (for example, '<', '>', and the like), are a symptom of an attack. |
| Illegal HTTP Version | Enable/disable the HTTP version check. Well-formed requests include the version of the protocol used by the client, in the form of HTTP/v where v is replaced by the actual version number (one of 0.9, 1.0, 1.1). Malformed requests are a sign of traffic that was not sent from a normal browser and are a symptom of an attack. |
| Maximum Cookie Number In Request | Maximum number of cookie headers in an HTTP request. The default is 16. The valid range is 1-32. |
| Maximum Header Number In Request | Maximum number of headers in an HTTP request. The default is 50. Requests with more headers are a symptom of a buffer overflow attack or an attempt to evade detection mechanisms. The valid configuration range is 1-100. |
| Maximum Request Header Name Length | Maximum characters in an HTTP request header name. The default is 1024. The valid range is 1-8192. |
| Maximum Request Header Value Length | Maximum characters in an HTTP request header value. The default is 4096. Longer headers might be a symptom of a buffer overflow attack. The valid configuration range is 1-8192. |
| Maximum URL Parameter Name Length | Maximum characters in a URL parameter name. The default is 1024. The valid range is 1-2048. |
| Maximum URL Parameter Value Length | Maximum characters in a URL parameter value. The default is 4096. The valid range is 1-8192. |
| Maximum Request Header Length | Maximum length of the HTTP request header. The default is 8192. The valid range is 1-16384. |
| Maximum Request Body Length | Maximum length of the HTTP body. The default is 67108864. The valid range is 1-67108864. |
|
Request Method Rule |
|
|
Method |
Select one or more methods to match in the HTTP request line:
Note: The first 8 methods are described in RFC 2616. The group Others contains not commonly used HTTP methods defined by Web Distributed Authoring and Version (WebDAV) extensions. |
|
Action |
The default is alert. |
|
Severity |
The default is low. |
| Exception | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
|
Response Code Rule |
|
|
Minimum Status Code / Maximum Status Code |
Start/end of a range of status codes to match. You can specify codes 400 to 599. |
|
Action |
The default is alert. |
|
Severity |
The default is low. |
| Exception | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
SQL/XSS Injection Detection policies detect SQL injection and cross-site scripting (XSS) attacks. Injection occurs when user-supplied data is sent to an interpreter as part of a command or query. In an SQL injection attack, attackers craft HTTP requests that cause SQL queries to be executed directly against the web application’s database. XSS injection attacks cause a web browser to execute a client-side script.
In contrast to signature-based detection, the WAF SQL and XSS injection detector module detects SQL and XSS injection through lexical analysis, which is a complementary method and is faster.
The policy enables/disables scanpoints, the action when traffic matches signatures, and the event severity.
You can enable detection in the following scanpoints:
Header scanning is recommended. Body scanning impacts performance, so you have the option of disabling body scanning if system utilization or latency become an issue.
Table 62 describes the predefined policies.
If desired, you can create user-defined policies.
Before you begin:
After you have created an SQL injection/XSS policy, you can specify it in a WAF profile configuration.
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
| SQL | |
|
SQL Injection Detection |
Enable/disable SQL injection detection. |
|
URI Detection |
Enable/disable detection in the HTTP request. |
|
Referer Detection |
Enable/disable detection in the Referer header. |
|
Cookie Detection |
Enable/disable detection in the Cookie header. |
|
Body Detection |
Enable/disable detection in the HTTP Body message. |
|
Action |
The default is alert, but we recommend you deny SQL Injection. |
|
Severity |
The default is low, but we recommend you rate this high or medium. |
| SQL Exception Name | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
| XSS | |
|
XSS Injection Detection |
Enable/disable XSS injection detection. |
|
URI Detection |
Enable/disable detection in the HTTP request. |
|
Referer Detection |
Enable/disable detection in the Referer header. |
|
Cookie Detection |
Enable/disable detection in the Cookie header. |
|
Body Detection |
Enable/disable detection in the HTTP Body message. |
|
Action |
The default is alert, but we recommend you deny XSS Injection. |
|
Severity |
The default is low, but we recommend you rate this high or medium. |
| XSS Exception Name | Select an exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
Exceptions identify specific hosts or URL patterns that are not subject to processing by WAF rules.
Before you begin:
After you have created an exception object, you can specify it in WAF profiles and individual WAF feature rules.
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
|
Exception Host Status |
Enable/disable setting exceptions by host pattern. |
| Exception Host | Matching string. Regular expressions are supported. For example, you can specify www.example.com, *.example.com, or www.example.* to match a literal host pattern or a wildcard host pattern. |
| Exception URL |
Matching string. Must begin with a URL path separator (/). Regular expressions are supported. For example, you can specify pathnames and files with expressions like |
Bot detection policies use signatures and source behavior tracking to detect client traffic likely to be generated by robots instead of genuine clients. Some bots, such as search engine crawlers, are "good bots" that perform search indexing tasks that can result in more legitimate users being directed to your site. You enable a whitelist to permit those. "Bad bots" are known to send traffic that has an negative impact on site availability and integrity, such as DDoS attacks or content scrapping. You want to block these.
To get started, you can use predefined whitelists (known good bots) and blacklists (known bad bots). You can also specify a rate limit threshold of HTTP requests/second for sources not matched to either whitelist or blacklist. The rate limit threshold can be useful in detecting "unknown bots".
In the event of false positives, you can use the user-specified whitelist table to fine-tune detection.
Before you begin:
After you have configured Bot Detection policies, you can select them in WAF profiles.
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
| Status | Enable/disable Bot detection. |
| Search Engine Status | Enable/disable the predefined search engine spider whitelist. The list is included in WAF signature updates from FortiGuard. |
| Bad Robot Status | Enable/disable the predefined bad robot blacklist. The list is included in WAF signature updates from FortiGuard. |
|
HTTP Request Rate |
Specify a threshold (HTTP requests/second/source) to trigger the action. Bots send HTTP request traffic at extraordinarily high rates. The source is tracked by source IP address and User-Agent. The default is 0 (off). The valid range is 0-100,000,000 requests per second. |
|
Action |
The default is alert. |
|
Severity |
The default is low. |
| Block Period |
The default is 3600 seconds. The valid range is 1-3600. The maximum size of the block IP address table is 100,000 entries. If the table is full, the earliest entry will be deleted. |
|
Whitelist |
|
| IPv4/Netmask | Matching subnet (CIDR format). |
| URL Pattern | Matching string. Regular expressions are supported. |
| URL Parameter Name | Matching string. Regular expressions are supported. |
| Cookie Name | Matching string. Regular expressions are supported. |
| User Agent | Matching string. Regular expressions are supported. |
A WAF profile references the WAF policies that are to be enforced.
Table 66 describes the predefined profiles. In many cases, you can use predefined profiles to get started.
| Predefined Profiles | Description |
|---|---|
|
High-Level-Security |
|
|
Medium-Level-Security |
|
|
Alert-Only |
|
If desired, you can create user-defined profiles. The maximum number of profiles per VDOM is 255.
Before you begin:
After you have created a WAF profile, you can specify it in a virtual server configuration.
| Settings | Guidelines |
|---|---|
|
Name |
Configuration name. Valid characters are After you initially save the configuration, you cannot edit the name. |
|
Description |
A string to describe the purpose of the configuration, to help you and other administrators more easily identify its use. |
|
Web Attack Signature |
Select a predefined or user-defined Web Attack Signature configuration object. |
|
URL Protection |
Select a user-defined URL Protection configuration object. |
|
HTTP Protocol Constraint |
Select a predefined or user-defined HTTP Protocol Constraint configuration object. |
|
SQL/XSS Injection Detection |
Select a predefined or user-defined SQL/XSS Injection Detection configuration object. |
| Exception Name | Select a user-defined exception configuration object. Exceptions identify specific hosts or URL patterns that are not subject to processing by this rule. |
| Bot Detection | Select a user-defined Bot Detection configuration object. |