execute commands
You can use the command-line interface (CLI) execute commands to run diagnostic utilities, such as nslookup, ping, traceroute, and tcpdump.
The following example shows the list of execute commands:
FortiADC-VM # execute ?
backup backup
caching caching management
certificate certificate
checklogdisk find and correct errors on the log disk
date set/get date and time
factoryreset reset to factory default
formatlogdisk format log disk to enhance performance
log log management
nslookup nslookup
ping ping <host name | host ip>
ping-option ping option settings
ping6 ping <host name | host ipv6>
ping6-option ping6 option settings
reboot reboot the system
reload reload appliance
restore restore
shutdown shutdown appliance
tcpdump tcpdump <Port Number> [filter]
tcpdump-file tcpdump-file
traceroute traceroute
vmware vmware
execute commands example: ping and traceroute
If the system cannot connect to other hosts, try using ICMP (ping and traceroute) to determine if the host is reachable or to locate the node of your network at which connectivity fails, such as when static routes are incorrectly configured.
For example, you might use ping to determine that 172.16.1.10 is reachable:
execute ping 172.16.1.10
PING 172.16.1.10 (172.16.1.10): 56 data bytes
64 bytes from 172.16.1.10: icmp_seq=0 ttl=64 time=2.4 ms
64 bytes from 172.16.1.10: icmp_seq=1 ttl=64 time=1.4 ms
64 bytes from 172.16.1.10: icmp_seq=2 ttl=64 time=1.4 ms
64 bytes from 172.16.1.10: icmp_seq=3 ttl=64 time=0.8 ms
64 bytes from 172.16.1.10: icmp_seq=4 ttl=64 time=1.4 ms
--- 172.20.120.167 ping statistics ---
5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 0.8/1.4/2.4 ms
or that 192.168.1.10 is not reachable:
execute ping 192.168.1.10
PING 192.168.1.10 (192.168.1.10): 56 data bytes
Timeout ...
Timeout ...
Timeout ...
Timeout ...
Timeout ...
--- 192.168.1.10 ping statistics ---
5 packets transmitted, 0 packets received, 100% packet loss
Similar displays occur when using the IPv6 versions of the tools:
execute ping6 2607:f0b0:f:420::
PING 2607:f0b0:f:420:: (2607:f0b0:f:420::): 56 data bytes
--- 2607:f0b0:f:420:: ping statistics ---
5 packets transmitted, 0 packets received, 100% packet loss
If the host is not reachable, you can use traceroute to determine the router hop or host at which the connection fails:
execute traceroute 192.168.1.10
traceroute to 192.168.1.10 (192.168.1.10), 32 hops max, 72 byte packets
1 192.168.1.2 2 ms 0 ms 1 ms
2 * * *
execute command example: tcpdump
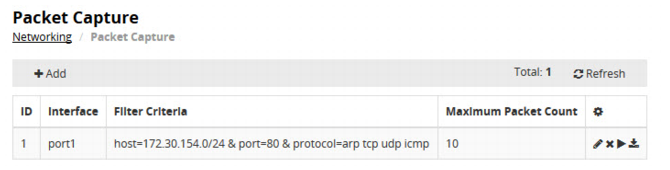
The FortiADC OS includes the tcpdump utility, which you can use to capture packets.
The tcpdump utility on the FortiADC OS supports the following syntax:
execute tcpdump <Interface> "Expression" [Count] [File_type] [File_name]
<Interface> | Network interface to listen for traffic, such as port1 or port2. |
"Expression" | Specify a filter expression to determine the packets that are captured. Only packets that match the expression are captured. If no expression is specified, all packets received at the interface are captured. For information on filter expressions, see the TCP dump man page: |
[Count] | Specify the number of packets to capture and then exit. The valid range is 1 to 10,000. If you do not specify a count, you can terminate the capture by pressing Ctrl-C. |
[File_type] | Specify pcap or text. If you do not specify a file type, the results are printed to the screen and not to a file. |
[File_name] | Specify the filename for the saved capture. Do not specify a filename extension. The extension .pcap or .txt is added automatically. |
You can use the tcpdump-file command to manage the packet capture files. The following example shows the list of tcpdump-file options:
FortiADC-VM # execute tcpdump-file
cat show one file
delete delete one file
list list all files
upload upload
The following examples show the tcpdump commands:
FortiADC-VM # execute tcpdump port1 "tcp port 80" 5 text test1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on port1, link-type EN10MB (Ethernet), capture size 65535 bytes
5 packets captured
5 packets received by filter
0 packets dropped by kernel
FortiADC-VM # execute tcpdump-file list
-rw-r--r-- 1 0 0 577 Sep 3 14:31 test1.txt
FortiADC-VM # execute tcpdump-file upload tftp test1.txt 172.30.144.5