Global load balancing basics
The global load balancing (GLB) feature is a DNS-based solution that enables you to deploy redundant resources around the globe that you can leverage to keep your business online when a local area deployment experiences unexpected spikes or downtime.
In this solution, the FortiADC system implements a hardened BIND 9 DNS server that can be deployed as the authoritative name server for the DNS zones that you configure. You can create DNS policy rules that direct clients to the servers closest to them, and you can also administer the DNS policy rules to deal with changed circumstances and avoid outages. For example, during scheduled or unscheduled downtime, you can easily change the rules so that global traffic is forwarded to an available remote site that is usually reserved for its local clients.
The DNS server supports the following security features:
• DNSSEC—Domain Name System Security Extensions. DNSSEC provides authentication by associating cryptographically generated digital signatures with DNS resource record (RR) sets. The FortiADC system makes it easy to manage the keys that must be provided to DNS parent domains and the keys that must be imported from DNS child domains.
• Response rate limit—Helps mitigate DNS denial-of-service attacks by reducing the rate at which the authoritative name servers respond to high volumes of malicious queries.
• DNS forwarding—In a typical enterprise local area network, the client configuration has the IP address of an internal authoritative DNS server so that requests for internal resources can be answered directly from its zone data. Requests for remote resources are sent to another DNS server known as a forwarder. Using forwarders reduces the number of DNS servers that must be able to communicate with Internet DNS servers.
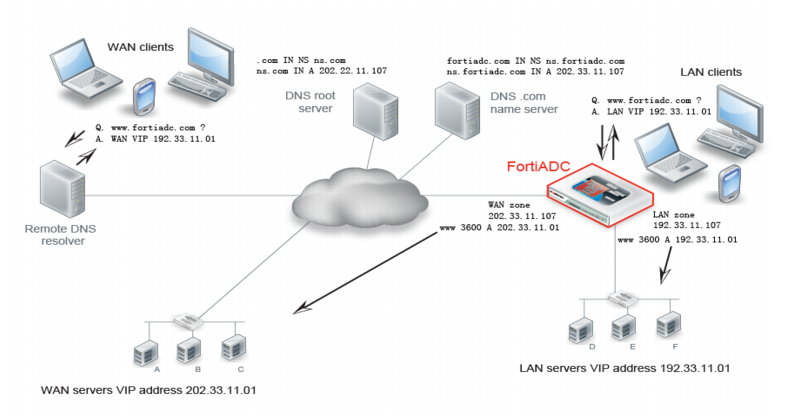
Figure 32 shows an example of a global load balancing deployment for an enterprise that has campus local area network (LAN) resources to serve campus employees and wide area network (WAN) resources to serve remote employees.
In this deployment, real servers A, B, and C belong to a virtual server located “off campus”; real servers D, E, and F belong to a virtual server located on campus. The resources hosted on the servers are identical and serve requests to the same site: www.fortiadc.com. The solution uses DNS to direct requests from source IP addresses within the campus IP address space to the LAN servers and requests from source IP addresses not in the campus IP address space to the WAN servers.
The deployment has the following basic steps:
1. FortiADC Global DNS zones—Create DNS zones for the LAN and WAN resources; and, for each zone, create A/AAAA records that map the hostname of the website to IP addresses that specify one or more virtual servers provisioned for zone. In the example below, the FortiADC DNS server has a LAN zone with an A/AAAA record that maps requests to www.fortiadc.com to the LAN zone virtual IP address 192.33.11.01; and a WAN zone with an A/AAAA record that maps requests to www.fortiadc.com to the WAN zone virtual IP address 202.33.11.0.
2. FortiADC Global DNS policy—Create a Global DNS policy that matches DNS requests from source IP addresses within the campus IP address space to the LAN zone records; and requests from IP addresses not within the campus IP address space to the WAN zone records.
3. LAN DNS—Configure DNS in your local network to use the FortiADC LAN zone virtual IP address as the authoritative name server for the domain.
4. WAN DNS—Configure the Internet DNS domain server (such as a DNS .com server) to use the WAN zone virtual IP address as the authoritative name server for the domain.
When clients in the LAN request www.fortiadc.com, the local name server replies with an IP address from the LAN zone records. When clients in the WAN request www.fortiadc.com, the Internet DNS process ultimately resolves the query with an IP address from the FortiADC name server WAN zone records.
You can add multiple records for a hostname, corresponding with redundant deployments of the virtual servers. DNS uses weighted round-robin to select a record from multiple matching entries, so you can use the weight setting to manage load among them.
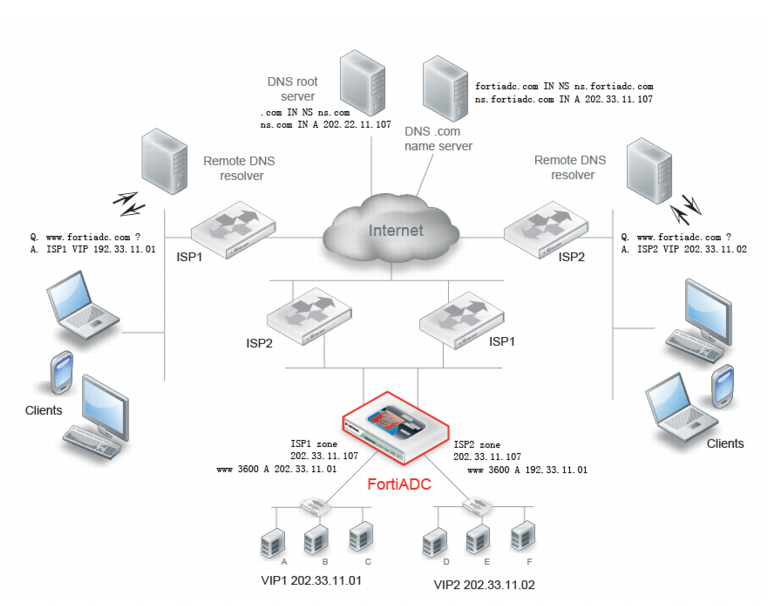
Figure 33 shows an example of a global load balancing deployment for a business that provides resources for clients to access over the public Internet.
In this deployment, real servers A, B, and C belong to a virtual server that has been provisioned for requests forwarded through ISP1; real servers D, E, and F are provisioned for requests forwarded through ISP2. The resources hosted on the servers are identical and serve requests for the same site: www.fortiadc.com. The solution uses DNS to direct requests from source IP addresses within the ISP1 address space to ISP1 servers and requests from source IP addresses within the ISP2 address space to the ISP2 servers.
The deployment has the following basic steps:
1. FortiADC Global DNS zones—Create DNS zones for ISP1 and ISP2; and, for each zone, create A/AAAA records that map the hostname of the website to IP addresses that specify one or more virtual servers provisioned for the zone. In the example below, the FortiADC DNS server has a zone named ISP1 with an A/AAAA record that maps requests to www.fortiadc.com to the IP address for a local virtual server provisioned for ISP1; and a zone named ISP2 with an A/AAAA record that maps requests to www.fortiadc.com to the IP address for a local virtual server provisioned for ISP2.
2. FortiADC Global DNS policy—Create a Global DNS policy that matches DNS requests from source IP addresses within the ISP1 IP address space to the ISP1 zone records; and requests from IP addresses within the ISP2 IP address space to the ISP2 zone records.
3. Internet DNS—Configure the Internet DNS domain server (such as a DNS .com server) to use the FortiADC DNS server as the authoritative name server for the domain fortiadc.com.
The Internet DNS system ultimately queries the FortiADC zone records for information to resolve the client requests. When clients from ISP1 request fortiadc.com, the FortiADC DNS server replies with information from ISP1 zone records. When clients from ISP2 request fortiadc.com, the FortiADC DNS server replies with information from ISP2 zone records.
You can add multiple records for a hostname, corresponding with redundant deployments of the virtual servers. DNS uses weighted round-robin to select a record from multiple matching entries, so you can use the weight setting to manage load among them.