Planning the network topology
To receive traffic intended for servers that your FortiADC appliance will balance and do content routing for, you usually should install the FortiADC appliance between the servers and all clients that access them. One-arm topologies are possible, but if there is any routing misconfiguration, traffic could accidentally bypass FortiADC.
The network configuration should ensure that all network traffic destined for the back-end servers must first pass to or through the FortiADC appliance. Usually, clients access back-end servers from the Internet through a firewall such as a FortiGate, so the FortiADC appliance should be installed between your servers and the firewall. If you will be load balancing between server clusters scattered world-wide by using global server load balancing, this topology should be duplicated at each location.
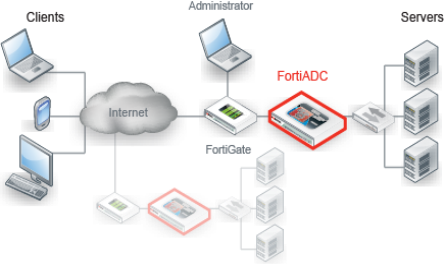
| FortiADC appliances are not general-purpose firewalls. While they are security-hardened network appliances, security is not their primary purpose, and you should not allow to traffic pass through without inspection. FortiADC and FortiGate complement each other to improve security, availability, and performance. |
| Virtual servers can be on the same subnet as physical servers. This configuration creates a one-arm load balancer. For example, the virtual server 10.0.0.2/24 could forward to the physical server 10.0.0.3-200. However, this is not recommended. Unless your network’s routing configuration prevents it, it could allow clients that are aware of the physical server’s IP address to bypass the FortiADC appliance by accessing the physical server directly. |
Other topology details and features vary by the mode in which the FortiADC appliance will operate. For example, FortiADC appliances operating in high availability (HA) pairs or configured to perform network address translation (NAT) instead of route-based forwarding will affect redundant switches and possibly the configuration of your routers.

