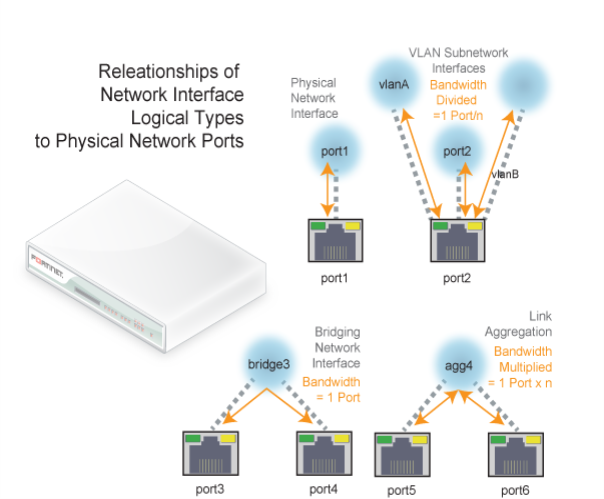
Initially, each physical network port (or, on FortiADC-VM, a vNIC) has only one network interface that directly corresponds to it — that is, a “physical network interface.” Multiple network interfaces (“subinterfaces” or “virtual interfaces”) can be associated with a single physical port, and vice versa (“redundant interfaces”/”NIC teaming”/”NIC bonding” or “aggregated links”). These can provide features such as link failure resilience or multi-network links.